附件下载见:CTF-Archives/2024-qwbs8: 第八届 “强网杯” 全国网络安全挑战赛
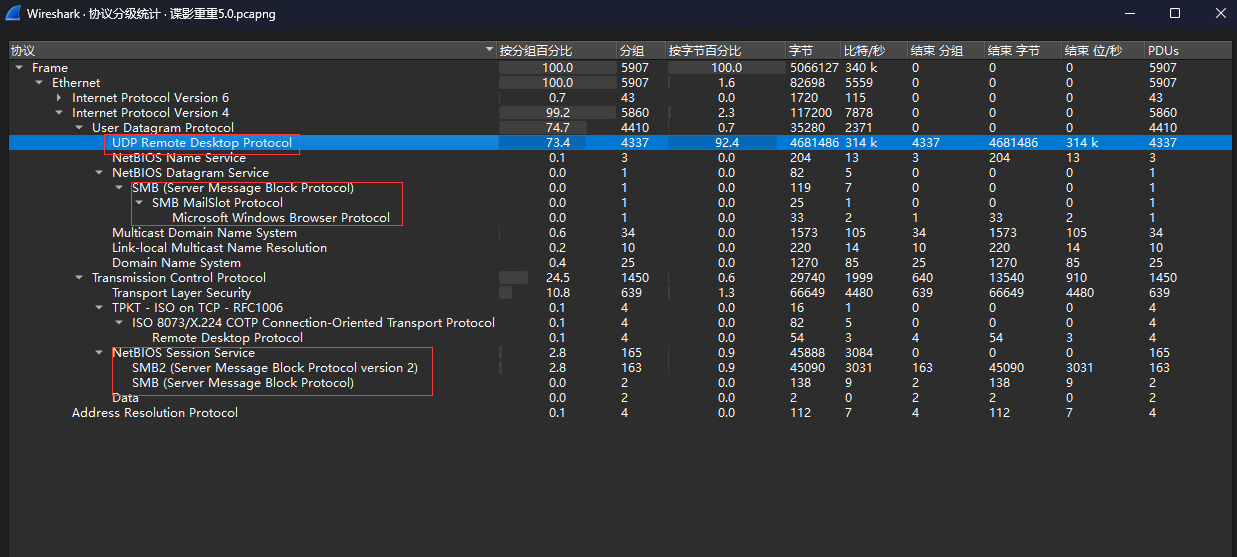
我专挑Misc的做,其他的做不来🤣,拿到附件打开是个流量包,看了下协议分级统计
UDP协议中的RDP包比较多,TCP有个SMB协议的
先查看SMB流,过滤一下,这个就跟浙江大学生网络安全预赛EZtraffic做法类似,参考文章:2024第七届浙江省大学生网络与信息安全竞赛预赛 | 热心市民
整理下拼接后得到的NTLM V2的hash
1 tom::.:c1dec53240124487:ca32f9b5b48c04ccfa96f35213d63d75:010100000000000040d0731fb92adb01221434d6e24970170000000002001e004400450053004b0054004f0050002d004a0030004500450039004d00520001001e004400450053004b0054004f0050002d004a0030004500450039004d00520004001e004400450053004b0054004f0050002d004a0030004500450039004d00520003001e004400450053004b0054004f0050002d004a0030004500450039004d0052000700080040d0731fb92adb0106000400020000000800300030000000000000000100000000200000bd69d88e01f6425e6c1d7f796d55f11bd4bdcb27c845c6ebfac35b8a3acc42c20a001000000000000000000000000000000000000900260063006900660073002f003100370032002e00310036002e003100300035002e003100320039000000000000000000
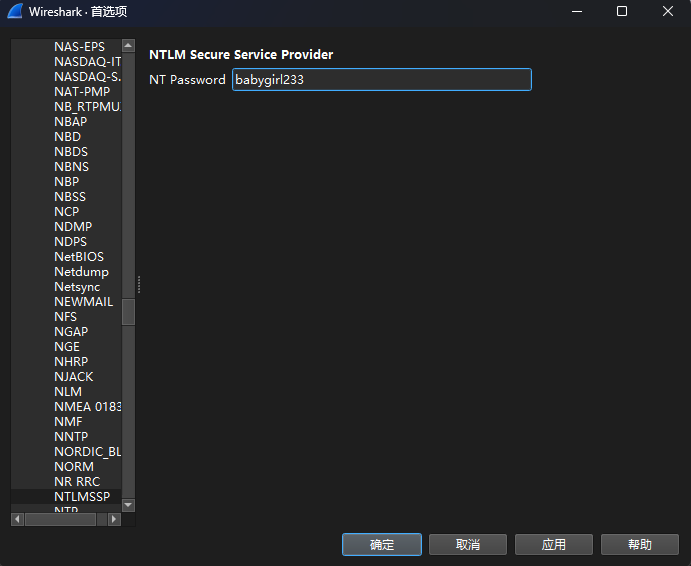
使用hashcat爆破下,得到密码为babygirl233
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 ❯ hashcat -a 0 -m 5600 hash /usr/share/wordlists/rockyou.txt.gz rockyou.txt hashcat (v6.2.6) starting OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, LLVM 17.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform ============================================================================================================================================ * Device Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Rules: 1 Optimizers applied: * Zero-Byte * Not-Iterated * Single-Hash * Single-Salt ATTENTION! Pure (unoptimized) backend kernels selected. Pure kernels can crack longer passwords, but drastically reduce performance. If you want to switch to optimized kernels, append -O to your commandline. See the above message to find out about the exact limits. Watchdog: Hardware monitoring interface not found on your system. Watchdog: Temperature abort trigger disabled. Host memory required for this attack: 1 MB Dictionary cache built: * Filename..: /usr/share/wordlists/rockyou.txt.gz * Passwords.: 14344392 * Bytes.....: 139921507 * Keyspace..: 14344385 * Runtime...: 2 secs TOM::.:c1dec53240124487:ca32f9b5b48c04ccfa96f35213d63d75:010100000000000040d0731fb92adb01221434d6e24970170000000002001e004400450053004b0054004f0050002d004a0030004500450039004d00520001001e004400450053004b0054004f0050002d004a0030004500450039004d00520004001e004400450053004b0054004f0050002d004a0030004500450039004d00520003001e004400450053004b0054004f0050002d004a0030004500450039004d0052000700080040d0731fb92adb0106000400020000000800300030000000000000000100000000200000bd69d88e01f6425e6c1d7f796d55f11bd4bdcb27c845c6ebfac35b8a3acc42c20a001000000000000000000000000000000000000900260063006900660073002f003100370032002e00310036002e003100300035002e003100320039000000000000000000:babygirl233 Session..........: hashcat Status...........: Cracked Hash.Mode........: 5600 (NetNTLMv2) Hash.Target......: TOM::.:c1dec53240124487:ca32f9b5b48c04ccfa96f35213d...000000 Time.Started.....: Wed Nov 20 17:16:05 2024 (6 secs) Time.Estimated...: Wed Nov 20 17:16:11 2024 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base.......: File (/usr/share/wordlists/rockyou.txt.gz) Guess.Queue......: 1/2 (50.00%) Speed.#1.........: 1704.6 kH/s (0.67ms) @ Accel:512 Loops:1 Thr:1 Vec:8 Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new) Progress.........: 9838592/14344385 (68.59%) Rejected.........: 0/9838592 (0.00%) Restore.Point....: 9836544/14344385 (68.57%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1 Candidate.Engine.: Device Generator Candidates.#1....: babygurl1230 -> babyfowler Started: Wed Nov 20 17:15:46 2024 Stopped: Wed Nov 20 17:16:12 2024
将得到的密码填入Wireshark中的NT Password,否则无法解密SMB流也不能导出SMB对象
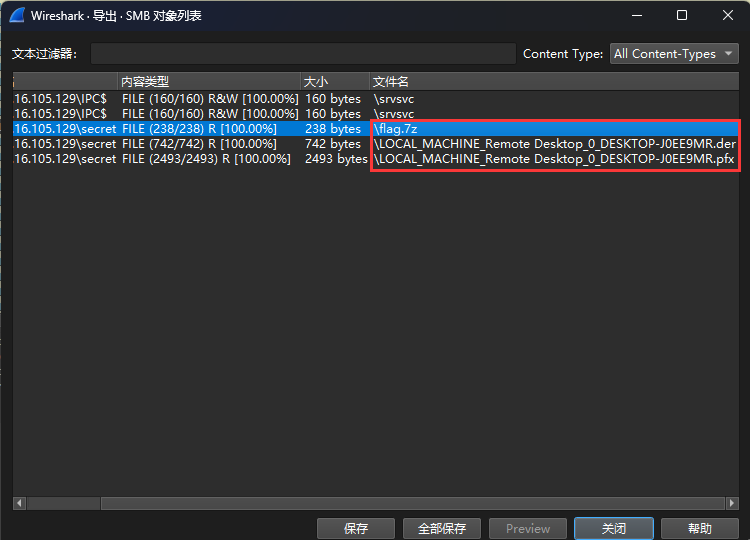
导出SMB对象得到三个文件,分别是压缩包和两个类似证书密钥的文件
很显然压缩包是加密的无法直接打开,那就从其他两个文件入手,回想上文提到的RDP协议,RDP协议是使用TLS/SSL进行加密的,那这两个文件大概率就是密钥文件了,针对于这两个文件分别进行解密,DER文件本身就包含公钥信息不需要进行解密,解密PFX文件需要使用OpenSSL解密但又提示需要PFX文件的密码,这个如何获取呢?
经过查询得知windows本身不会提供任何导出PFX私钥的方法,但是通过软件猕猴桃Mimikatz可以到导出,然而导出的密码就是mimikatz
1 2 3 4 ❯ openssl x509 -inform der -in LOCAL_MACHINE_Remote\ Desktop_0_DESKTOP-J0EE9MR.der -outform pem -out server.crt ❯ openssl pkcs12 -in LOCAL_MACHINE_Remote\ Desktop_0_DESKTOP-J0EE9MR.pfx -nocerts -nodes -out server.key Enter Import Password: ❯ cat server.crt server.key >server.pem
PEM文件可以包含各种类型的加密材料,包括:
X.509证书 :用于SSL/TLS通信的服务器和客户端证书。私钥 :与证书配对的私钥,用于加密数据和签名。证书链 :一系列证书,用于建立信任链,证明证书的合法性。
提取公钥参数解释:
openssl x509:OpenSSL工具,用于处理X.509证书。-inform der:指定输入文件格式为DER。-in yourfile.der:指定输入文件名为yourfile.der。-outform pem:指定输出文件格式为PEM,如未指定将默认为PEM。-out yourfile.crt:指定输出文件名为yourfile.crt
提取密钥参数解释:
-in yourfile.pfx:指定输入的PFX文件。-nocerts:不输出证书链。-nodes:不使用DES加密算法对私钥进行加密。-out keypair.key:指定输出的私钥文件。
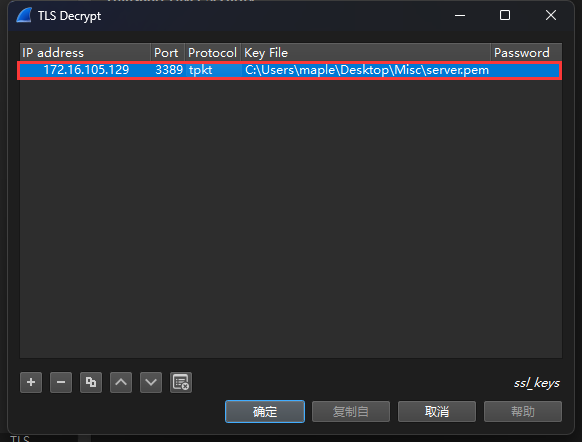
将PEM文件导入Wireshark解密RDP传输的TLS包,端口默认3389,ip为172.16.105.129,而常用的RDP协议(Remote Desktop Protocol,远程桌面协议)是基于TPKT协议的的
解密后的RDP肉眼看下一堆Mouse的流量
利用Github上一个项目pyrdpGoSecure/pyrdp: RDP monster-in-the-middle (mitm) and library for Python with the ability to watch connections live or after the fact
安装一下,不知道为啥使用pipx装上用pyrdp-player出不来GUI界面,只能使用git源安装了,在python的虚拟环境中pip3安装
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ❯ git clone https://github.com/gosecure/pyrdp.git Cloning into 'pyrdp' ... remote: Enumerating objects: 14909, done . remote: Counting objects: 100% (1766/1766), done . remote: Compressing objects: 100% (463/463), done . remote: Total 14909 (delta 1402), reused 1359 (delta 1302), pack-reused 13143 (from 1) Receiving objects: 100% (14909/14909), 20.80 MiB | 15.00 MiB/s, done . Resolving deltas: 100% (10943/10943), done . Updating files: 100% (267/267), done . ❯ python3 -m venv .rdp ❯ source venv/bin/activate ❯ pip3 install -U pip setuptools wheel ❯ pip3 install -U -e '.[full]'
GoSecure/pyrdp: RDP monster-in-the-middle (mitm) and library for Python with the ability to watch connections live or after the fact 根据文档导出OSI Layer 7另存为xxx.pacp包,不要导出为pcapng,PyRDP不支持
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 ❯ pyrdp-convert -o output 123.pcap [*] Analyzing PCAP '123.pcap' ... - 0.20.0.4:1638404 -> 0.21.0.4:1703940 : plaintext - 116.108.115.0:2 -> 172.16.105.1:50819 : plaintext - 116.108.115.0:2 -> 172.16.105.129:3389 : plaintext - 172.16.105.1:50834 -> 172.16.105.129:3389 : plaintext - 115.95.0.0:3 -> 172.16.105.1:50503 : plaintext - 115.95.0.0:3 -> 172.16.105.129:3389 : plaintext [*] Processing 0.20.0.4:1638404 -> 0.21.0.4:1703940 100% (9 of 9) |################################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104800_0.20.0.4:1638404-0.21.0.4:1703940.pyrdp' [*] Processing 116.108.115.0:2 -> 172.16.105.1:50819 100% (2 of 2) |################################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104800_116.108.115.0:2-172.16.105.1:50819.pyrdp' [*] Processing 116.108.115.0:2 -> 172.16.105.129:3389 100% (2 of 2) |################################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104800_116.108.115.0:2-172.16.105.129:3389.pyrdp' [*] Processing 172.16.105.1:50834 -> 172.16.105.129:3389 0% (0 of 603) | | Elapsed Time: 0:00:00 ETA: --:--:-- [-] Failed to handle data, continuing anyway: 524305 is not a valid RDPVersion [-] Failed to handle data, continuing anyway: list index out of range [-] Failed to handle data, continuing anyway: 'NoneType' object is not subscriptable [-] Failed to handle data, continuing anyway: 'NoneType' object is not subscriptable [-] Failed to handle data, continuing anyway: 'NoneType' object is not subscriptable [-] Failed to handle data, continuing anyway: 'NoneType' object is not subscriptable 100% (603 of 603) |############################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104801_172.16.105.1:50834-172.16.105.129:3389.pyrdp' [*] Processing 115.95.0.0:3 -> 172.16.105.1:50503 100% (8 of 8) |################################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104802_115.95.0.0:3-172.16.105.1:50503.pyrdp' [*] Processing 115.95.0.0:3 -> 172.16.105.129:3389 100% (12 of 12) |##############################################################################################| Elapsed Time: 0:00:00 Time: 0:00:00 [+] Successfully wrote '/home/ctf/Desktop/qwb/output/20241030104802_115.95.0.0:3-172.16.105.129:3389.pyrdp'
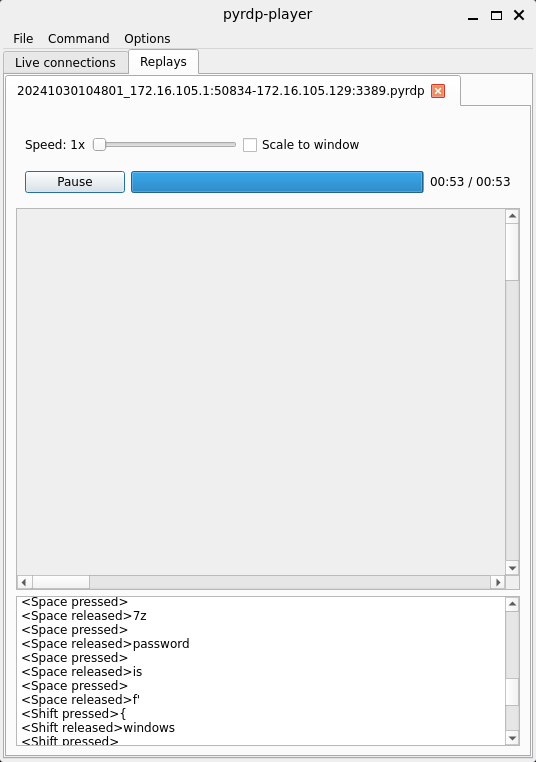
在output目录会生成一个后缀为.pyrdp的文件,使用pyrdp-player <FILE1> <FILE2> ...打开一下
1 2 ❯ pyrdp-player 20241030104801_172.16.105.1:50834-172.16.105.129:3389.pyrdp [2024-11-20 20:58:30,453] - INFO - pyrdp.player - Listening for connections on 127.0.0.1:3000
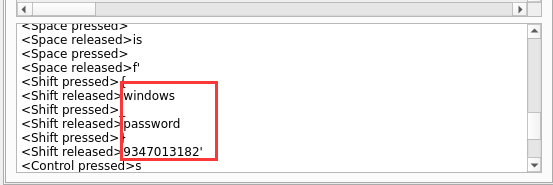
打开GUI界面后发现鼠标虽然有动但没什么信息,主要键盘打了一些字
给出压缩包密码为{windowspassword}9347013182,结合上面提到的windowspassword=babygirl233,拼接组合得到压缩包密码为babygirl2339347013182,解压后得到flag{fa32a0b2-dc26-41f9-a5cc-1a48ca7b2ddd}
PyRDP 是一个 Python 远程桌面协议 (RDP) 中间人攻击 (MITM) 工具和库
参考:[分享]如何使用Wireshark解密Windows远程桌面(RDP)协议-二进制漏洞-看雪-安全社区|安全招聘|kanxue.com
SMB 解密 - TryHackMe :: MWLab — Ladislav 的恶意软件实验室
分析捕获的 RDP 会话 |哈克索号 — Analyzing captured RDP sessions | haxor.no
iHack 2020:Monster Inc The Middle(RDP 网络取证)作者:埃米利奥·冈萨雷斯 |中等的 — iHack 2020: Monster Inc The Middle (RDP Network Forensics) Writeup | by Émilio Gonzalez | Medium