
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
80端口看一下是什么类型的站点
看来是默认的nginx页面
但是为啥标题是apache2❓
1 | ❯ whatweb -v $ip |
扫一下目录,加个限制长度
然而并没有任何收获
当我去访问robots.txt时发现还是会跳转到这个默认页面
并不会显示404报错或者其他的返回,比如没有这个网页的话就会报404
我随便打一串路径访问也是会跳转到默认页面
我curl一下,无论你输入什么到会返回200ok
但是我发现了藏在结尾的一行注释
1 | ❯ curl -iv "http://$ip/1fhaskfhla" |
给了个提示,让我们从图片格式下手
到这就卡住了,没什么有用的信息
我在想为什么无论请求什么路径都会跳转到index.php
猜测可能编辑了.htaccess或者是apache的配置文件
我curl一下.htaccess发现403报错了,没有权限
1 | ❯ curl -iv "http://$ip/.htaccess" |
群里给了个提示,需要找到一张猫的图片,没招了
搁置吧
发现图片文件名在源代码的中间部分😅
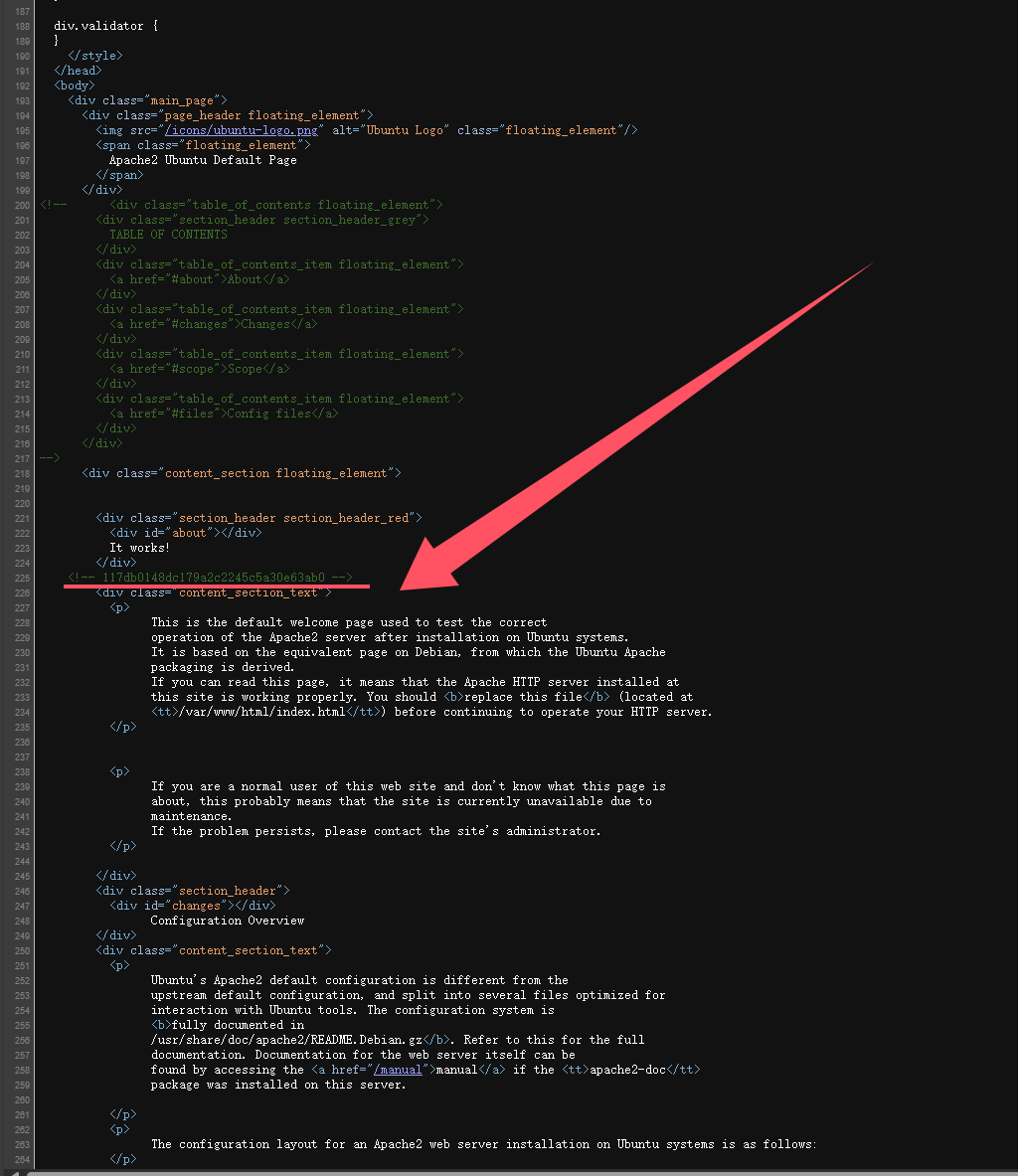
这我属实是没找到,我只关注了结尾的注释提示,中间的一般都是apache自带的文档注释
找到猫了,哈哈哈群头像🤣

图片隐写
不用想就是图片隐写了
但是jpg和png各有一张,对于隐写之类的两者都有
CTF中常见的就是藏个文件之类的操作
wget一下两张图片
1 | ❯ wget http://192.168.60.182/117db0148dc179a2c2245c5a30e63ab0.jpg |
利用zsteg一把梭
得到疑似密码的字符串morainelake
1 | ❯ zsteg 117db0148dc179a2c2245c5a30e63ab0.png |
既然png中隐藏信息找到了,那jpg必然也有一个
利用上面的密码得到一个secret.zip压缩包
1 | ❯ steghide extract -sf 117db0148dc179a2c2245c5a30e63ab0.jpg |
解压一下得到ssh登录凭证
1 | ❯ x secret.zip |
用户提权
1 | ❯ ssh morainelake@192.168.60.182 |
到这里就已经拿到user了
在opt目录下有个提示,顺便打个广告哈哈哈🤣
1 | morainelake@listen:~$ cd /opt/ |
reverse逆向
还有一个可执行程序,IDA Pro逆向一下
得到伪C代码
简单看一下逻辑
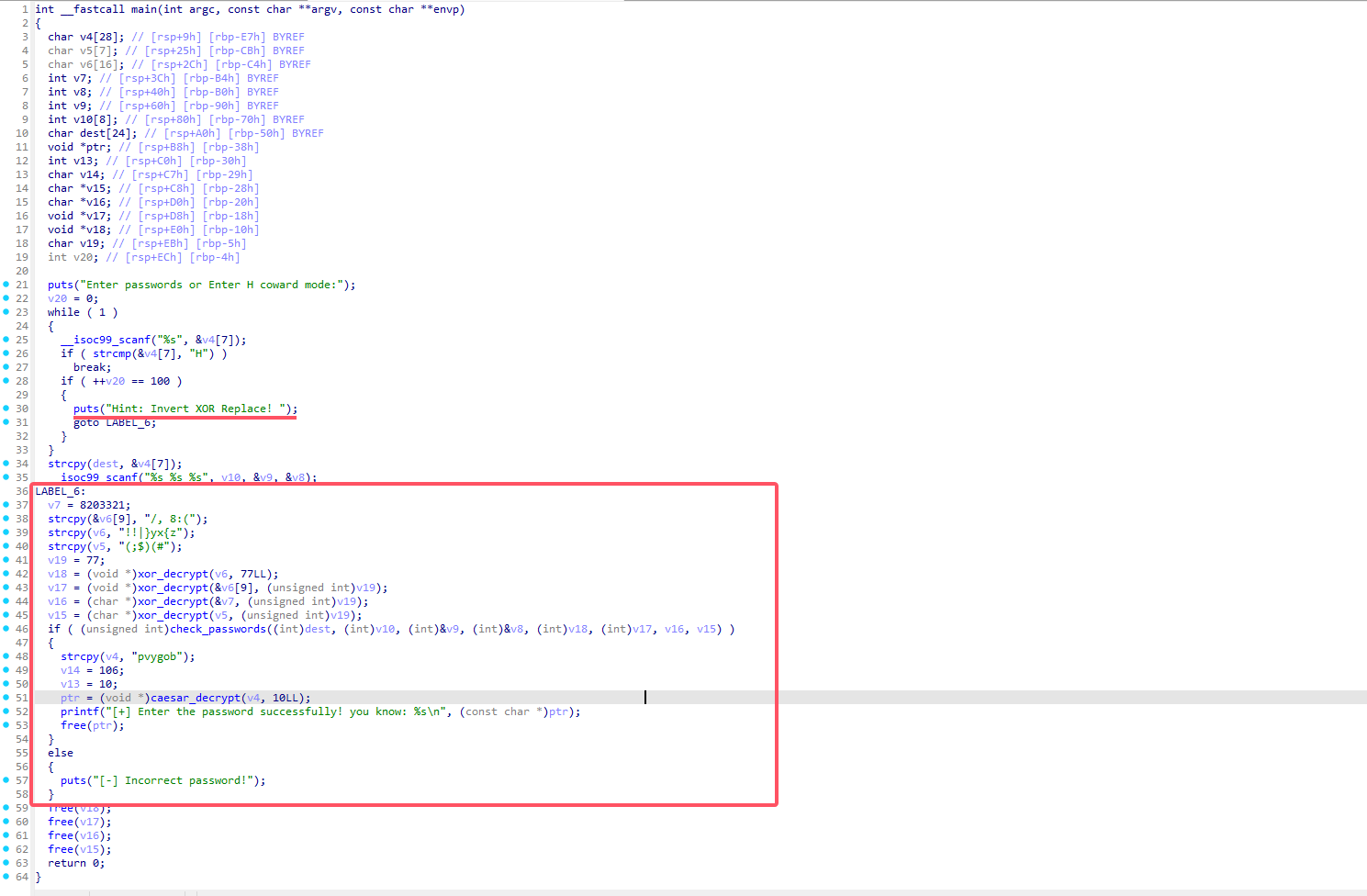
按H进入懦夫模式,哈哈哈😅
在hint中,提示我们反转XOR或者替换
从伪代码中可以得知V19是异或值77转为ASCII为M
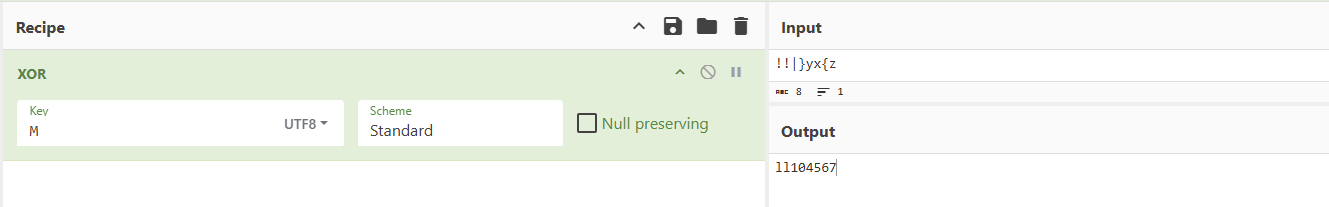
第一次输入是对比v18,v18与v6异或得知密码是ll104567
后面依次进行分别得到bamuwe eviden还有一个v16是与v7异或M得到的
但v7是数字不能直接异或,需要转为字符数组,再次进行异或得知ta0
利用GPT给出的脚本
1 |
|
编译一下
1 | ❯ gcc a.c |
得到密码后验证一下
1 | morainelake@listen:/opt$ ./reverse |
哈哈flower是个彩蛋
Root提权
利用上面正确的密码顺序切换一下用户
1 | morainelake@listen:/opt$ su welcome |
发现拥有gcc的sudo权限
这里*给了操作空间
成功拿到root shell了
1 | welcome@listen:/opt$ sudo /usr/bin/gcc -wrapper /opt/../bin/sh,-s . |
