TheHackersLabs-JaulaCon2025-Walkthrough

信息收集
服务探测
1 | ❯ sudo arp-scan -l |
编辑hosts文件,添加域名
1 | ❯ echo "$ip jaulacon2025.thl"|sudo tee -a /etc/hosts |
枚举目录
1 | ❯ gobuster dir -u http://jaulacon2025.thl -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt -x php,html,zip,txt -b 403,404 |
可以得知存在一个bludit的CMS框架
不过无法得知是什么版本的框架
POC利用爆破
但是有个admin的后台登录地址
我们可以利用这个POC进行爆破登录
Bludit 3.9.2 - Auth Bruteforce Bypass - PHP webapps Exploit

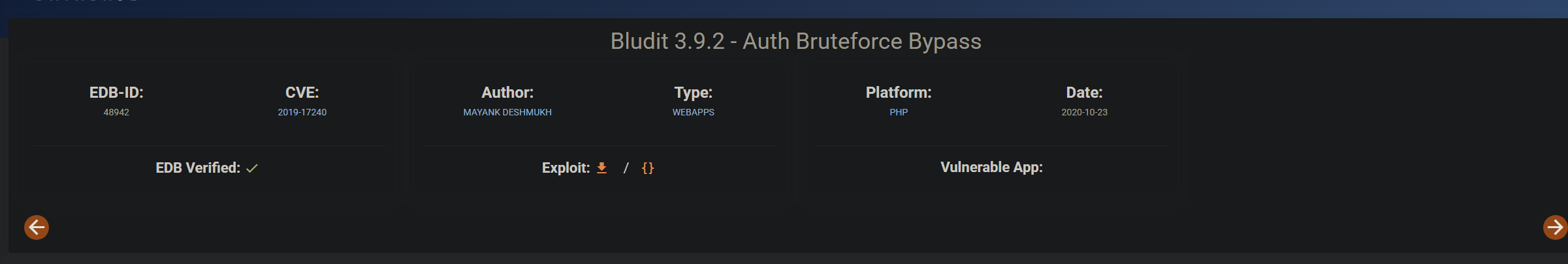
用户名就是在首页中出现过的Jaulacon2025
不过我直接运行脚本会报编码错误,改一下代码绕过编码解析错误即可
得到登录凭证Jaulacon2025:cassandra
1 | ❯ wget https://www.exploit-db.com/download/48942 |
同时在此版本下还有个通过上传插件可以获取webshell的漏洞
hg8/CVE-2019-16113-PoC: Bludit >= 3.9.2 - Authenticated RCE (CVE-2019-16113)
修改一下地址和账户凭证以及反弹地址
1 | ❯ vi CVE-2019-16113.py |
用户提权
监听一下端口
得到两个用户debian JaulaCon2025
1 | ❯ pwncat-cs -lp 4444 |
再次信息收集
可以在bl-content/databases中发现用户的数据库信息
其中就包含了JaulaCon2025用户的密码hash
1 | (remote) www-data@JaulaCon2025:/var/www/html/bl-content/databases$ cat users.php |
尝试在线网站爆破一下
得到凭证JaulaCon2025:Brutales
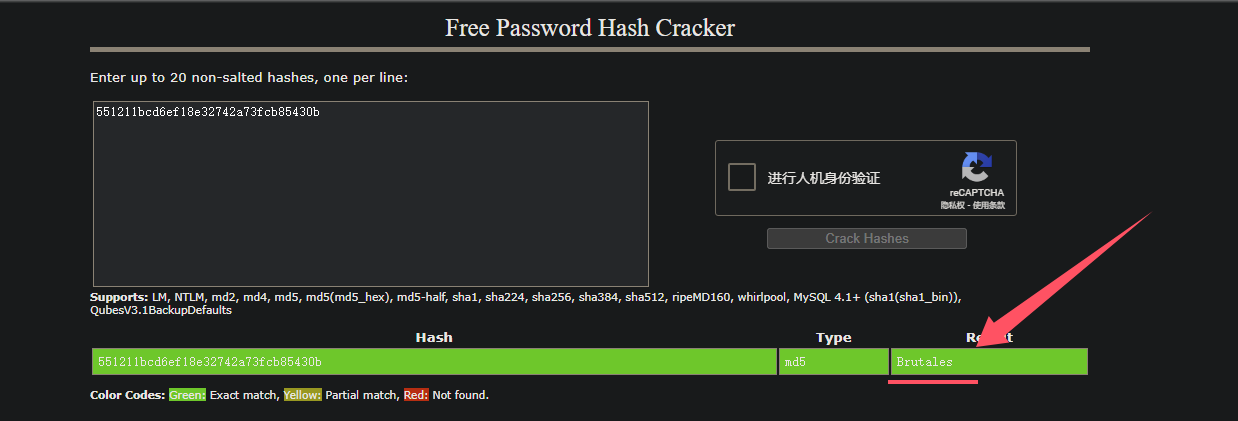
尝试登录一下
1 | (remote) www-data@JaulaCon2025:/var/www/html/bl-content/databases$ su JaulaCon2025 |
Root提权
得知存在用户拥有sudo权限
正常提权即可
1 | JaulaCon2025@JaulaCon2025:~$ sudo -l |
